Remove APEX ransomware
APEX ransomware is a generic ransomware infection that encrypts files and demands a payment in exchange for a decryptor. The ransomware can be identified by the .Apex extension it adds to encrypted files. Unfortunately, once files have been encrypted, you will not be able to open them unless you first use a specific decryptor on them. However, the only people who have the decryptor are the malicious actors operating this ransomware. They will demand an outrageously large sum of $10,000 for the decryptor, suggesting they do not take helping victims recover files seriously. Because there is currently no free APEX ransomware decryptor available, only users who have backups can recover files for free.
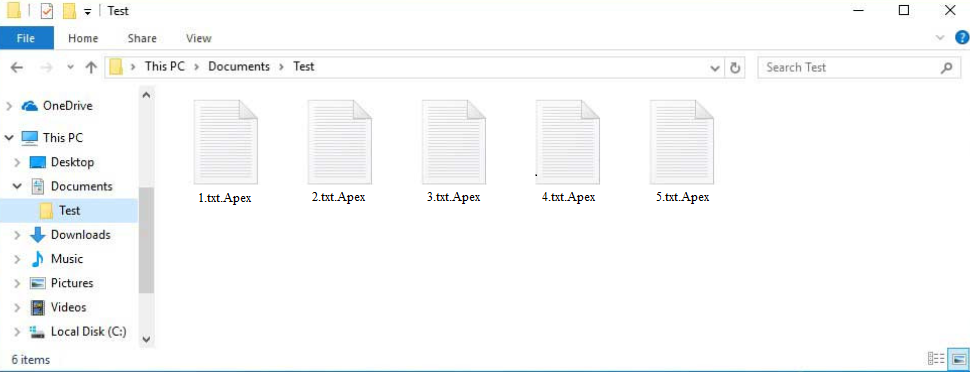
Like all other ransomware, APEX ransomware specifically targets personal files such as photos, videos, documents, and more—these are the types of files people are most likely to pay to recover. Once encrypted by APEX ransomware, files will have the extension .Apex added to them; for instance, image.jpg would become 1.jpg.Apex if encrypted. Opening these encrypted files requires the use of a decryption tool, but obtaining this tool is not easy and involves paying a ransom, which experts generally advise against doing.
APEX ransomware will drop an APEXNOTE.txt ransom note once files have been encrypted. The note informs users that their files have been encrypted and provides instructions on how to obtain a decryptor. From the very beginning, it becomes quite clear that the malicious actors do not have the intention of helping victims recover files as they demand $10,000 in ransom. While such a large amount is not uncommon when businesses are targeted, regular users are usually requested to pay up to $1,000. What’s more, victims are not assigned unique IDs that would allow malicious actors to differentiate between them and know whom to send the decryptions. Thus, it’s very unlikely that a decryptor would be sent even if victims were to pay. The malicious actors also threaten that if the ransom is not paid within 24 hours, the decryptor will be destroyed. Dealing with cybercriminals means there’s always a chance they might take your money without fulfilling their end of the deal. This has happened to many users in the past, and unfortunately, it would likely happen in this case as well.
At this time, there is no free APEX ransomware decryptor. This may change in the future, so if you find yourself with no other options, it might be wise to back up your encrypted files and wait for a free decryption tool to be developed. However, exercise caution about where you source these tools, as there are many fraudulent ones that could introduce additional malware to your system. A reliable resource for finding free decryptors is NoMoreRansom; if a decryptor for APEX ransomware becomes available, it will likely be available there.
The full APEX ransomware note is below:
APEX RANSOMWARE
Attention Dear User. All of your files and personal information have been encrypted.
These encrypted files are now completely corrupted and unusable.
But do not fret. There is still hope for you. All you need to do is visit the darknet site listed below and pay a total of $10,000 USD worth of bitcoin to the address listed on the site. Upon paying the ransom, we can insure that the decryption software will be delivered to you and you will get all of your files back. Failure to pay the ransom within a 24 hour time peroid will result in the decryption software being destroyed and your files will be lost forever. But we are sure you can manage.DARKNET SITE:
–Kind Regards
Apex
How does ransomware infect a computer?
APEX ransomware is distributed in various ways, including email attachments, advertisements, and malicious ads. Typically, users with poor online habits are more susceptible to encountering malware infections. Therefore, it’s crucial to develop better browsing habits to minimize the risk of falling victim to malicious attacks.
Malicious spam is a common method used by cybercriminals to spread malware. They often target users whose email addresses have previously been leaked, purchasing these addresses from hacker forums. To check if your email address has been compromised, you can check on HaveIBeenPwned. If you find that your email is listed, exercise extra caution with any emails that contain attachments and/or links.
Fortunately, many malicious emails have clear indicators of their maliciousness. Look out for grammar and spelling mistakes, especially in emails that claim to be from reputable companies. Additionally, the email addresses of these senders are generally random, consisting of a jumbled mix of letters and numbers. Be wary if the sender refers to you as “Customer,” “Member,” or “User” when they should know your name.
However, some malicious emails can be more sophisticated, particularly when they target someone in particular. This is why you should scan any unsolicited attachments with anti-virus software or VirusTotal before opening them.
Moreover, users who download pirated content are at a higher risk of encountering malware infections. Torrent websites, in particular, are often poorly monitored, allowing malicious actors to upload infected torrents disguised as popular movies, TV shows, video games, or software. By engaging in piracy, users not only violate copyright laws but also expose their devices and personal data to significant risks.
How to remove APEX ransomware
We advise against trying to manually remove APEX ransomware, as this may cause further damage. Instead, it’s best to use a reliable anti-virus program for APEX ransomware removal. Once the ransomware is eliminated from your system, you can proceed with file recovery if you have backups available. However, if you don’t have secure copies of your files, the only option left is to wait for a free decryptor. While there isn’t a free decryptor for APEX ransomware at this moment, it’s possible that one may be made available in the future.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.