Remove Cdtt ransomware
Cdtt ransomware, or .cdtt virus, is ransomware from the Djvu malware family. It’s a type of malware that takes users’ personal files hostage and demands payment if victims want to recover them. This specific ransomware can be identified by the .cdtt extension that gets added to all encrypted files. Unfortunately, you will not be able to open any files that have that extension, unless you first put them through a decryptor. Unfortunately, the only ones who have it are the cybercriminals operating this malware. They will try to sell it to you, but trusting cybercriminals is not a good idea.
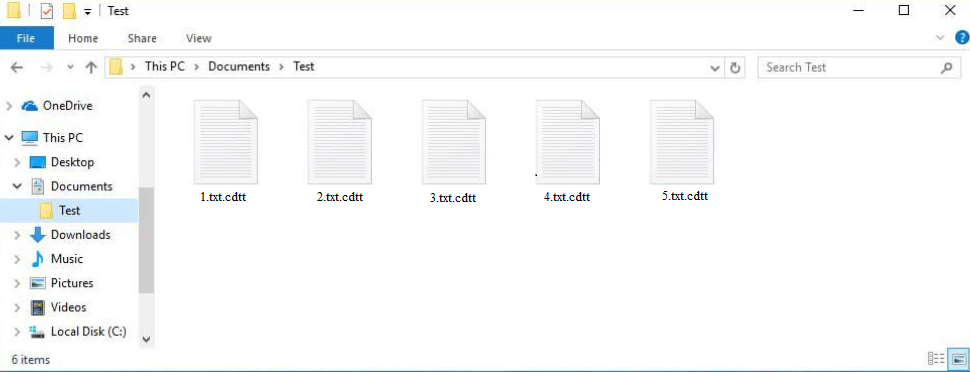
Cdtt ransomware is part of the Djvu/STOP ransomware family, and while certain Djvu variants may be more prevalent than others, all of them pose significant risks. These ransomware infections focus on personal files and will encrypt them. You can expect common file types—such as photos, videos, documents, and more—to be affected. Once encrypted, files will have an extension added to their names, which in this case is .cdtt. For example, a 1.txt file would become 1.txt.cdtt. You will not be able to open any of these files.
After the encryption process, a _readme.txt ransom note will be generated, detailing how to obtain a decryptor. Unfortunately, the malicious actors demand a payment of $1,999. The note also offers a 50% discount for those who contact the perpetrators within the first 72 hours, although the authenticity of this offer is questionable. Generally, paying the ransom and purchasing the decryptor is a risky choice. Ultimately, the decision is yours, but remember that there is no guarantee that you’ll receive a Cdtt ransomware decryptor. Cybercriminals do not operate malware like legitimate businesses, regardless of how they may present themselves. There is no guarantee they will uphold their end of the bargain after payment. In fact, many victims have reported not receiving their decryptors after spending substantial amounts of money. Additionally, your payment would contribute to further criminal activities. However, the choice to pay or not is entirely yours to make.
The ransom note dropped by the .cdtt virus contains the following text:
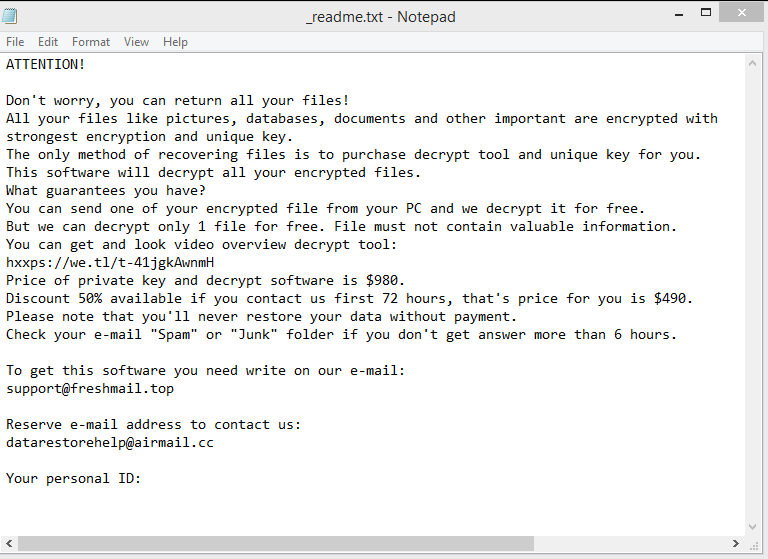
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-FCWSCsjEWS
Price of private key and decrypt software is $1999.
Discount 50% available if you contact us first 72 hours, that’s price for you is $999.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshingmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
–
To begin safely recovering your files from backup, you’ll first need to remove Cdtt ransomware from your computer. It’s essential to use a trustworthy anti-malware program since ransomware can be quite complex. Once you fully delete Cdtt ransomware, you can safely access your backup.
If you don’t have a backup, recovering your files will be significantly more challenging, if not impossible. You can choose to wait for a free Cdtt ransomware decryptor to be released, but there’s no guarantee that it will happen.
How does ransomware infect computers?
Ransomware, like many forms of malware, is commonly spread through email attachments, torrents, and malicious advertisements. Typically, users with poor online habits are the ones who inadvertently infect their computers with all kinds of malware, which is why developing safe browsing habits is very important. It’s also important to familiarize yourself with the various ways malware is distributed.
When it comes to email attachments, exercise caution, especially if they come from unknown sources. Opening an attachment from an unfamiliar sender could lead to your computer being compromised. Thankfully, malicious emails often contain clear warning signs. Many ransomware operators lack proficiency in English, resulting in emails filled with grammar and spelling errors. If a sender claims to be from a reputable company but their email appears unprofessional and has many mistakes, that’s a significant red flag. Additionally, consider how you are addressed in the email; legitimate companies typically use users’ names in their communications. For instance, if you receive an email from a company whose services you use, it will address you using the name you used when registering. On the other hand, if an email refers to you generically as “Customer,” “Member,” or “User,” proceed with caution before opening any attachments.
It’s worth noting that some malware campaigns are more sophisticated and can deceive even the most vigilant users. Therefore, it’s recommended to scan any email attachments using anti-virus software or services like VirusTotal before opening them.
Torrents are another common method through which users can unknowingly download malware. Torrent sites often have poor security, and uploading malicious files is relatively easy. Malicious actors may disguise malware within torrents of popular movies, TV shows, software, and video games. Not only is torrenting copyrighted material content theft, but it also poses risks to your computer and personal data.
.cdtt virus removal
Make sure to use anti-malware software to remove Cdtt ransomware from your system. This type of infection is very sophisticated and should be handled with the help of a reliable anti-malware program. Attempting to manually delete Cdtt ransomware without sufficient knowledge can lead to further damage to your computer. It’s important to thoroughly eliminate all components of the ransomware, as leaving any behind could allow it to restore itself. If that occurs while you’re trying to recover files from your backup, those files could also become encrypted. Once the anti-malware software has successfully removed the ransomware, you can safely access your backup to begin restoring your files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.