UK’s consumer protection organization warns of Omicron variant phishing emails
UK’s consumer protection organization Which? has warned of an ongoing Omicron variant-themed phishing campaign. These phishing emails claim that to avoid restrictions, people need to order a free PCR test. They can do that by clicking on the link in the email. Clicking on the link would lead to a fake NHS website. The site asks users to put in their personal information, as well as pay for the test’s delivery.
With the appearance of the Omicron variant, cybercriminals are wasting no time. UK’s consumer protection organization Which? has come across a new phishing campaign that tries to phish users’ information. Cybercriminals try to do that by taking advantage of users’ fears about the coronavirus. This is certainly not the first time this has happened. Since the beginning of the pandemic, there have been countless COVID-19 phishing campaigns. There was one that claimed people are eligible to get a tax refund because of the pandemic. Back in April, the US Department of Justice warned about a phishing campaign that promises prizes if people fill in a post-COVID-19 vaccine survey. And before vaccinations became widely available, there was a phishing campaign inviting people to register to get the vaccine in the UK.
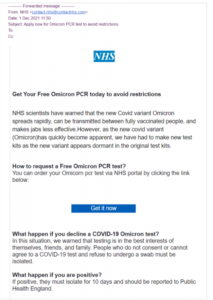
This new COVID-19 phishing campaign warns that with the appearance of the new Omicron variant, people need to take a new test because the original does not show when people are infected. The email claims that people can order their “free Omicron PCR test” by clicking on the link. The email also warns that people who do not order and take the test “must be isolated”.
The email, which can be seen below, is not particularly convincing. It contains grammar mistakes, is missing spaces, and just seems off in general. Furthermore, the sender’s email address is contact-nhs@contactnhs.com. At first sight, it may seem like it could be an email address that belongs to the NHS. However, users familiar with phishing attempts will realize that it’s fake. Malicious actors purposely create email addresses to resemble legitimate ones. But doing a bit of research will allow users to tell the difference. Though in this particular case, using Google to search the email address leads to the NHS’s Contact Us page. This is why it’s important to research which email addresses actually belong to the company/organization that’s supposedly sending the email.
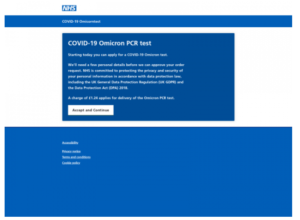
Clicking on the “Get it now” button would lead users to a fake NHS website. The fake site claims that users can apply for the Omicron variant test. But they need to provide personal information, as well as send £1.24 for the supposed delivery. If users continue, they would be asked to type in their full name, date of birth, home address, email address, and phone number. Furthermore, the malicious actors ask users to add a security question to their accounts. The phishing attempt asks the mother’s maiden name question. This is a standard security question people use to secure their online bank and other accounts. The phished information can be used for a variety of purposes. It will likely be sold on a hacker forum for other cybercriminals to use.
The site that users who click on the email link are led to looks pretty legitimate. At least, at first sight. The notification on the site has a few grammar mistakes so that may be a red flag to some users. However, the biggest giveaway is the site’s URL. The phishing site has a healt-service-nh.com URL so it’s obvious that the site is not legitimate.
Generally, it’s recommended to not click on links in any unsolicited emails, no matter who the sender is. In this particular case, users should have looked into whether the NHS is actually sending out new tests kits. If no information about this can be found on the NHS’s official website, then it would be easy to determine that the email is fake.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.