Cybersecurity news headlines (December 1-14)
It has been an eventful two weeks, and while there were no worldwide ransomware attacks, we did see one major data breach, one huge data leak, more than a billion of credentials exposed, hackers stealing money from banks and $80 million worth of Bitcoin stolen. These are only the few incidents that took place over the last 14 days. Below you will find the biggest news headlines from December 1-14, in no particular order.

Hacker group MoneyTaker silently steals millions from US banks
A hacker group has successfully conducted over 20 attacks on financial institutions and legal firms in the USA, UK and Russia in the last two years, Group-IB, an international cybersecurity company reports. 20 victims have been confirmed so far, but the group has gone undetected until now. Group-IB notes that in addition to constantly changing their tools and tactics to bypass antivirus and other security solutions, the group also manages to eliminate all trace of the operation, allowing them remain undetected.
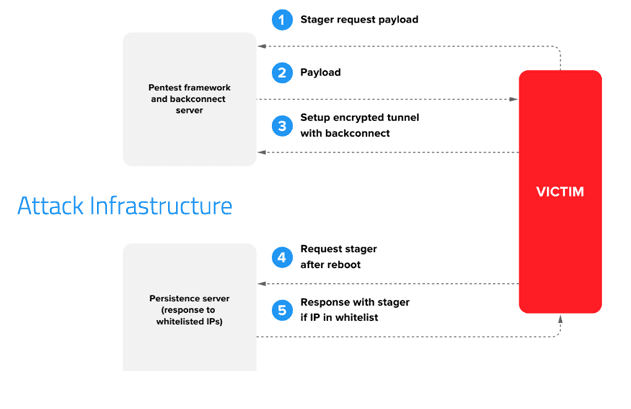
The first attack is believed to have taken place in 2016, in an US bank. Attacks on companies in California, Utah, Oklahoma, Colorado, Illinois, Missouri, South Carolina, North Carolina, Virginia and Florida followed. A Russian bank was also targeted but the attack was prevented. The cybersecurity company made the connection between the incidents after looking into the tools used, attack infrastructure and withdrawal schemes.
Law enforcement agencies, including Europol and Interpol, have been informed about the incidents.
1.4 billion clear text credentials found in a single file
4iQ security researchers have made a rather disturbing discovery during a deep web monitoring session. They stumbled upon a file containing 1.4 billion credentials. And the most worrying thing is that they were not encrypted, rather in clear text. In a report released on the 8th, 4iQ researchers note that the file rather than just being a list of credentials is essentially a database.

“This is not just a list. It is an aggregated, interactive database that allows for fast (one second response) searches and new breach imports, the researchers report. “This database makes finding passwords faster and easier than ever before. As an example searching for “admin,” “administrator” and “root” returned 226,631 passwords of admin users in a few seconds,” they continue.
It is explained that the data came from not one single incident, but rater multiple sources. Login credentials from Netflix, Last.FM, LinkedIn, MySpace, Zoosk, YouPorn, Minecraft and Runescape were among those found on the database. Some of the credentials found were from breaches that took place years ago but because users tend to reuse passwords, they can still be used today to break into an account.
The report also highlights the problem of password simplicity. According to 4iQ, the password ‘123456’ was found 9218720 times, ‘qwerty’ and ‘password’ 1651385 and 1313464 times respectively. Evidently, users are still careless when it comes to password creation, and tend to stick to easy to guess rather than complex passwords.
$80 million in Bitcoin stolen from NiceHash
The largest Bitcoin mining marketplace NiceHash was hacked last week, criminals taking off with a staggering 4,700 Bitcoins, currently worth around $81 million (worth around 70 million when the hack took place). NiceHash is a service that allows users from all over the world to rent out their spare computer resources to make Bitcoin. The company was founded in 2014 and has allowed miners to make over a billion dollars collectively over the years. Company’s CEO Marko Kobal remarks that this success drew the wrong kind of attention which led to the hack.

The hack was first noticed by users who saw their wallets emptied of Bitcoin. NiceHash confirmed the hack after taking the service offline. The service is still offline over a week later, and the company is working along with international law enforcement agencies to identify the hackers and recover the stolen funds.
Keyboard app exposed personal data of 31 million users
Researchers from Kromtech Security Center have discovered that the personal data of 31 million virtual keyboard app users was accidentally leaked online. AI.type, the keyboard app in question, exposed their database containing 577 GB of information online, and anyone could have accesses it without any password.

Founded in 2010, AI.type can boast a user base of around 40 million people, and it allows users to customize and personalize on-screen keyboards. When users install the app, they are asked to provided all kinds permissions but many apps tend to ask for ones they do not need to function. It turns out, AI.type had access to much more information that it needed to work.
The database includes information such as full names, phone numbers, email addresses, device information, IP address, GPS location and information associated with social media profiles (birth data, email, photos). It was also revealed that the app had access to the contact books.
“Based on the leaked database they appear to collect everything from contacts to keystrokes. This is a shocking amount of information on their users who assume they are getting a simple keyboard application,” Bob Diachenko, Kromtech’s Chief Communication Officer, states.
Hacker who tried to have friend released early now faces jail time
Konrads Voits is now facing jail time after he modified records to have an inmate released early. The 27 year old man used social-engineering techniques to make jail employees install malware onto the system, which allowed him to gain access to the County network, search and access inmate records and modify them.
Reportedly, Voits called jail employees posing as people who are actually working in the jail’s IT department. The jail employees were asked to access certain websites, and install a supposed upgrade for the system. Unfortunately, some did fall for Voit’s ploy, which essentially allowed him to obtain information such as passwords, usernames and emails of over 1,600 employees. He then used the acquired information to infiltrate the jail’s system and access the inmate records.
The breach was noticed immediately, the FBI was contacted and Voits was soon taken into custody. He now faces up to 10 years of jail time, as well as a fine of $250,000.
Andromeda botnet shut down
Law enforcement agencies in collaboration with private companies took down Andromeda, the botnet that was active since 2011 and spanned over two million computers. Reportedly, security company ESET and Microsoft were tracking the malware used to create the botnet for 18 months, and the two companies along with Europol and the FBI took control of the domains used to control the botnet, shutting it down.
The malware was first spotted in 2011, and its main intentions were to distribute other malware and to steal credentials. It was one of the ESET’s most detected malware, which led to them collaborating with Microsoft to track it.
Traffic from Andromeda infected computers has been disrupted after law enforcement took charge of the domains used by the malware. Microsoft reports that over two million IP addresses in 223 countries were contacting the malicious domains.
PayPal acquired company suffered a data breach involving 1.6 million people
It was revealed that TIO Networks, the company recently acquired by PayPal, has suffered a security breach, where a hacker gained access to servers containing the personal information of 1.6 million customers.
TIO Networks runs a network of utility and bill payment kiosks in North America, and was bought by PayPal back in July. In November, its operations were suspended by PayPal after someone managed to gain access to their servers. It was not revealed exactly what information has been accesses but it is assumed that it was personal and financial data.
PayPal admitted that the data of around 1.6 million customers could have been compromised, but the breach did not affect PayPal itself. Affected TIO Networks users will be contacted, and offered a free credit monitoring service.
Google to warn Android users about unauthorized data gathering
Google is fighting against Android apps which collect information unauthorized. The company is warning app developers that if they unauthorized collect information, users will be warned by Google Safe Browsing. Apps that collect personal information or device data will have to inform users and provide their own privacy policy. And if data that is not essential for app functionality is collected and transmitted, the app must inform the user about how the information will be used and must acquire affirmative consent from the user.
App developers have 60 days to comply with Google’s policies, and if they fail to do, users will start getting alerts about unauthorized data collection, which would likely encourage them to uninstall the app.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
