Cybersecurity news headlines for April 2021
April’s edition of cybersecurity news talks about one massive data breach, an extortion attempt, a cyberattack, an official accusation of cyber espionage, and the eradication of a significant cyber threat. Stories include Facebook’s 533 million user data leak, REvil’s $50 million extortion attempt on Apple, Russia named the culprit behind SolarWinds cyberattack, cyberattacks against EU organizations, and removal of the notorious Emotet from all infected devices. We also discuss the long-awaited iOS 14.5 App Tracking Transparency feature.
Without further ado, here’s what made the biggest cybersecurity headlines in April 2021.
Information of 533 million Facebook users leaked online for free
Social media giant Facebook was involved in yet another data leak scandal. A threat actor released on a publicly accessible cybercrime forum a database containing information of 533 million Facebook users. The database contained phone numbers, some number of email addresses, Facebook ID numbers, profile names, location information, gender, and other information from Facebook profiles. While the majority of this information is available to anyone, many phone numbers are not public in profiles. Facebook has called the incident web scraping, citing a vulnerability that it patched in 2019.
The most worrying news is not the database itself as its existence has been known for a while. It’s the fact that it’s now available to anyone. Back in January this year, Alon Gal from Under the Breach spotted a Telegram bot that allowed users to query the database for a low fee. For whatever reason, the database was later made available for free.
The leaked data appears to mostly be from 2019. An attacker was able to exploit a vulnerability in Facebook’s Add Friend feature. The automatic scrapping process lasted for some time until Facebook noticed and stopped it. The threat actor was still able to scarp data of 533 million Facebook users.
Besides tweeting that the data is old and the incident was already reported in 2019, Facebook has not addressed what happened. It has also not informed affected users, a decision criticized by many. Instead, users who want to check whether they have been affected can do so on haveibeenpwned.
Ireland’s Data Protection Commission (DPC) is currently investigating the incident. It has noted that the social media giant is not being forthcoming with information related to the incident or communication with the DPC in general.
Facebook received further criticism when a DataNews journalist received internal Facebook communication by accident. The email in question was intended for Facebook’s public relations staff located in Europe, Middle East, and Africa. The email explained that the company is anticipating media attention to decrease gradually. It also stressed the importance of “normalizing” data scrapping incidents to avoid criticism in the future.
“Longer term, though, we expect more scrapping incidents and think it’s important to both frame this as a broad industry issue and normalize the fact that this activity happens regularly,” the email reads.
REvil ransomware gang tries to extort Apple for $50 million
The notorious REvil ransomware gang tried to blackmail tech giant Apple into paying $50 million to not expose stolen product blueprints. They gave until May 1st to pay the ransom. The cyber crooks also threatened to post the blueprints on REvil’s platform if the ransom was not paid.
They were able to steal the blueprints from Quant Computer, a major manufacturer of Apple. It appears the cyber crooks wanted to extort Apple directly after Quanta refused to pay the ransom. Quanta Computer, a Taiwan-based company, has many high-profile clients including Microsoft, Lenovo, and Dell.
REvil (Sodinokibi) is one of the most notorious currently active ransomware gangs. It’s a private ransomware-as-a-service (RaaS). Its authors rent out the ransomware to affiliates who then carry out attacks against high-profile targets. It’s speculated that the group is Russia-based, as they do not target Russian organizations. The gang is known to steal large amounts of information during an attack. They later use it to blackmail victims into paying ransoms. In one famous case, the group tried to extort then-US President Donald Trump. It demanded $42 million to not reveal data they stole from law firm Grubman Shire Meiselas & Sacks.
It appears that Quant Computer is their latest high-profile victim. The company has acknowledged that they were indeed targets of REvil. But according to reports, the attack affected only a small number of Quant servers. Nonetheless, it seems that the REvil gang was able to steal some Apple product information. They have already leaked a part of the allegedly stolen information. Though it’s difficult to say whether it’s related to new Apple products.
Apple is yet to release a statement at the time of writing. It is also not known whether Apple made the decision to pay the ransom. But it has been reported that the ransomware gang removed all traces of Apple’s data from its website. Though considering that paying the ransom sets a dangerous precedent and increases the risk of a repeat cyberattack, it is unlikely that the tech giant gave in to the demands.
The US confirms Russia’s Cozy Bear is behind the SolarWinds hack
The US and UK governments have officially blamed the hacker group Cozy Bear for the massive SolarWinds cyberattack. Cozy Bear is a hacker group operating from Russia, believed to be led by Russia’s Foreign Intelligence Service (SVR). The official accusation came during the US’s announcement of sanctions against Russia. The announcement is not surprising, as a Russian-sponsored hacker group was believed to be responsible from the very beginning. A joint task force made up of US’s Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Office of the Director of National Intelligence (ODNI), and the National Security Agency (NSA) has previously said the attack was “likely Russian in origin”. Though at the time it was not attributed to Cozy Bear specifically.
The SolarWinds cyber attack came to light in December 2020 and is one of the most serious cyberattacks in recent years. The hackers targeted Orion, an IT management software managed by software company SolarWinds. Malicious actors were able to add malicious code to Orion updates. 18,000 of its customers downloaded the updates. The malicious code opened backdoors for the cyber crooks to access infected systems.
Soon after, it became known that among affected Orion customers were various US government agencies, including the Department of Justice, the Department of Homeland Security, the National Nuclear Security Administration, the Treasury, and the Department of Energy. Tech giant Microsoft was also among those affected, as were cybersecurity companies FireEye and Malwarebytes.
“Today the United States is formally naming the Russian Foreign Intelligence Service (SVR), also known as APT 29, Cozy Bear, and The Dukes, as the perpetrator of the broad-scope cyber-espionage campaign that exploited the SolarWinds Orion platform and other information technology infrastructures. The U.S. Intelligence Community has high confidence in its assessment of attribution to the SVR,” a statement released by the White House states.
The UK government has also claimed Russia is to blame for the SolarWinds cyber attack.
“The UK and US are today calling out Russia for carrying out the SolarWinds compromise, part of a wider pattern of activities by the Russian Intelligence Services against the UK and our allies,” a press release by Foreign, Commonwealth & Development Office and The Rt Hon Dominic Raab MP reads.
US President Biden has announced new sanctions against six Russian technology companies for their involvement in cyber attacks against the US. ERA Technopolis, Pasit, SVA, Neobit, AST, and Positive Technologies are the sanctioned companies. US companies and financial institutions are prohibited from doing business with them unless a license by the Office of Foreign Assets Control is first issued.
European Commission among EU organizations hit by cyberattacks
The European Commission and other European Union organizations were targets in a series of cyberattacks in March, it has been revealed. A spokesperson of the commission said EU organizations suffered an IT security incident in their IT infrastructure. According to Bloomberg, the incident was bigger than the usual attacks against the EU.
“We are working closely with CERT-EU, the Computer Emergency Response Team for all EU institutions, bodies and agencies and the vendor of the affected IT solution,” the spokesperson told Bloomberg. “Thus far, no major information breach was detected.”
Reportedly, due to the seriousness of the attack, senior commission officials were alerted. No other information, including the nature of the attack or who was behind it, has been released at the time of publication. The incidents are likely still under investigation.
Emotet malware removes itself from all infected devices
Law enforcement has eradicated Emotet, one of the most prevalent pieces of malware in recent history. After six years of activity, Emotet was finally disrupted by a global law enforcement operation early this year. And on April 25, 2021, law enforcement started eliminating the malware from all infected systems.
Emotet was initially a banking trojan but in 2016 was reconfigured to operate as a “loader” malware. To put it simply, Emotet could install malware onto a system it was infecting. Soon after, the Emotet gang started offering it as a malware-as-a-service (MaaS). Upon infection, Emotet would have been dormant until someone bought access to the network and released their own malware. One famous client of Emotet was the notorious Ryuk gang. They were among many ransomware gangs that rented out access to Emotet’s network for ransomware distribution. In just a few years, its creators made Emotet into one of the most sophisticated botnets with a sizeable network of infected computers. It is estimated that damage caused by Emotet exceeds hundreds of millions of dollars.
Early in 2021, Europe’s Europol announced that an operation involving eight countries disrupted Emotet. Law enforcement was able to take control of Emotet’s infrastructure during the joint operation. This allowed them to take down the botnet from the inside. Between its takedown in late January and its eradication on April 25, law enforcement controlled Emotet. Infected devices were in no danger during that time.
Law enforcement pushed a new Emotet configuration, forcing the malware to use a command and control server controlled by Germany’s federal police agency Bundeskriminalamt. Police then distributed a new Emotet module to every single infected system. It deleted the malware on April 25, 2021. We should note that the Emotet removal module did not delete malware that entered the system using Emotet. Rather, it only prevents future infections via this particular botnet.
The FBI has provided security specialist Troy Hunt with over 4 million email addresses obtained during Emotote’s takedown. Hunt owns Have I been Pwned, a service that allows users to search whether their email addresses (or phone number in some cases) have been part of a data breach. According to Hunt, the FBI reached out to him to make alerting victims easier. Hunt notes that to prevent victims from being targeted, he has made the decision to make this incident non-publicly searchable. To check whether they have been affected, users would need to either perform a domain search or subscribe to the “Notify me” service that would send an email to the provided email address whenever it’s included in a data breach.
Emotet, while one of the most notorious threats, is still only one threat. It’s more than likely that some other malware will take its place as the biggest MaaS soon enough.
Apple introduces App Tracking Transparency in new iOS 14.5 release
Apple released the long-awaited iOS 14.5 update on Monday and made the App Tracking Transparency (ATT) feature available to all users. While many users rejoice at being able to stop apps from gathering data about their activities on other platforms, advertisers criticized Apple’s decision to introduce this feature.
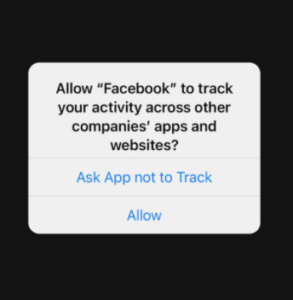
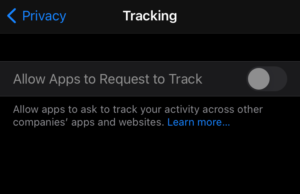
While the iOS 14.5 update introduced a couple of other features, the ATT is perhaps the most anticipated one. App Tracking Transparency is a feature that will inform users about an app installed on their iPhones trying to track their activities across other companies’ apps and websites. When users open an app, a pop-up will appear and ask users to choose either “Ask App not to Track” or “Allow”. Selecting the former option will prevent the app in question from being intrusive in its tracking. Users can also go to their Settings -> Privacy -> Tracking and toggle off the “Allow Apps to Request to Track” option. This will stop apps from tracking automatically without users needing to stop each individual app.
It should be mentioned that some users may think of this feature as an adblocker but that is not the case. Preventing an app from tracking means users will see non-personalized advertisements, as the app will not have access to data it could use to tailor ads. The ad amount will remain the same whether users allow tracking or not. If users prefer to see personalized ads, they can allow apps to track them. The important thing is that users are now given the choice.
However, it appears that the App Tracking Transparency feature does not work for everyone. Soon after release, user reports about grayed out “Allow Apps to Request to Track” started coming in. When users go to Settings -> Privacy -> Tracking, the “Allow Apps to Request to Track” feature is grayed out, preventing users from toggling it on or off.
Apple is aware of the issue and has said that the setting may be disabled in cases where the account belongs to a person under 18 years old, if the Apple ID is managed by an education institution, or if the account is younger than 3 days. However, multiple users have said the above-mentioned clauses do not apply to them.
Apple has said that if the option is grayed out, all app requests to track are denied by default.
References
- Kartikay Mehrotra. Apple Targeted in $50 Million Ransomware Hack of Supplier Quanta. Bloomberg.
- FACT SHEET: Imposing Costs for Harmful Foreign Activities by the Russian Government. The White House.
- Russia: UK and US expose global campaign of malign activity by Russian intelligence services. GOV.UK Press Release.
- Alberto Nardelli, Natalia Drozdiak. European Institutions Were Targeted in a Cyber-Attack Last Week. Bloomberg.
- Emotet botnet has been disrupted by global law enforcement operation. WiperSoft Blog.
- WORLD’S MOST DANGEROUS MALWARE EMOTET DISRUPTED THROUGH GLOBAL ACTION. Europol News Room.
- Troy Hunt. Data From The Emotet Malware is Now Searchable in Have I Been Pwned, Courtesy of the FBI and NHTCU.
- If an app asks to track your activity. Apple Support.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.