Flaw in antivirus can be abused to hijack a computer
An Austrian cyber security auditor, Florian Bogner, recently discovered a flaw that allows a local attacker to abuse the ‘restore from quarantine’ feature in antivirus software. The flaw, named AVGater, allows to move malware from an AV’s quarantine folder to a sensitive locations on the victim’s system, allowing the malware to run with full privileges.
source: https://bogner.sh/2017/11/avgater-getting-local-admin-by-abusing-the-anti-virus-quarantine/
How does AVGater work?
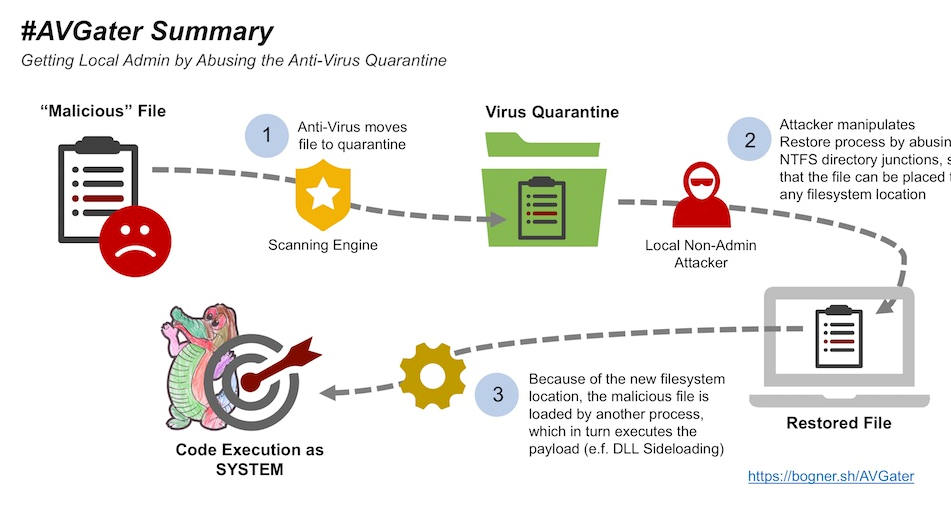
When an antivirus program detects a threat, it is not immediately deleted, but rather moved to quarantine. This is done because AVs are not perfect and can sometimes detect false positives. If a user decides to keep the quarantined file, whether it is because it is a false positive or for other reasons, they can restore it. The flaw takes advantage of the ‘restore from quarantine’ function, and can move malware from quarantine to a sensitive location on the computer.
Normally, a non-administrator user would not have the authorization to move a quarantined file to locations such as C:\Program Files or C:\Windows, but this flaw takes advantage of Windows’ NTFS function which allows them to do just that.
“#AVGater in plain English: By abusing NTFS directory junctions, the AV quarantine restore process can be manipulated, so that previously quarantined files can be written to arbitrary file system locations,” Bogner summarizes.
“First a malicious library is moved to the AV quarantine. Then, by abusing directory junctions the original source path is redirected to another destination. Most likely a folder within C:\Program Files or C:\Windows. By restoring the previously quarantined file, the SYSTEM permissions of the AV Windows user mode service are misused, and the malicious library is placed in a folder where the currently signed in user is unable to write to under normal conditions. Because of how the DLL search order works, it is finally loaded by another privileged Windows process. Thereby the code within the DLLMain of the malicious library is executed. Hence, a local non-admin attacker gained full control over the affected endpoint,” the security auditor also provides a complete attack scenario.
The flaw has one serious limitation, however. The attacker needs to have physical access to a computer. Security patches have already been released by some AV vendors, but even if this flaw remained unpatched, not many would be able to take advantage of it. However, people working in environments with shared computers, like an office, would be able to use the flaw.
How to protect yourself
Bogner notified antivirus vendors of the flaw, and some have already released a fix. They include Trend Micro, Emsisoft, Kaspersky, Malwarebytes, ZoneAlarm and Ikarus. Others have also been notified but are yet to release an update, thus are not named.
He advises users to always install updates in a timely manner but otherwise, there is not much users can do. Bogner also suggests that people in corporate environment block regular users from restoring files from quarantine, which would prevent the flaw from being exploited. This, however, would cause inconveniences for regular users as antivirus programs sometimes quarantine completely legitimate programs, and in order to restore them, regular users would need to contact IT services.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
