Remove Adventurer ransomware
Adventurer ransomware is a file-encrypting malware. It’s a dangerous type of infection that takes files hostage by encrypting them. It specifically targets all personal files, encrypts them, and adds the .adventurer extension to them. You will not be able to open any encrypted files unless you first use a decryptor on them. However, getting the decryptor is not going to be easy because only the malicious actors operating this malware have it. They will try to sell it to you, but even paying the ransom does not guarantee you’ll get a decryptor. At the moment, only users who have backups can recover their files for certain.
The Adventurer ransomware starts encrypting files as soon as it is initiated. You may not notice the process while it’s happening, but once it’s done, it will be obvious as you won’t be able to open any of the files. Each encrypted file will have an extension added, which includes your unique ID and the .adventurer suffix. For instance, a file named 1.txt would be renamed to 1.txt.{unique ID}.adventurer after being encrypted. Files with this extension will be unopenable. This ransomware targets a wide variety of file types, including documents and images, targeting anything that victims might want to get back and be willing to pay for.
After the encryption is finished, the ransomware drops a README.txt file as a ransom note. This note informs you that your files have been encrypted and states that the only way to retrieve them is by purchasing a unique private key. Unfortunately, the note is correct. The malicious actors demand payment for the decryption tool, but they do not specify the amount, which is likely to be several hundred or even thousands of dollars.
The full Adventurer ransomware ransom note is below:
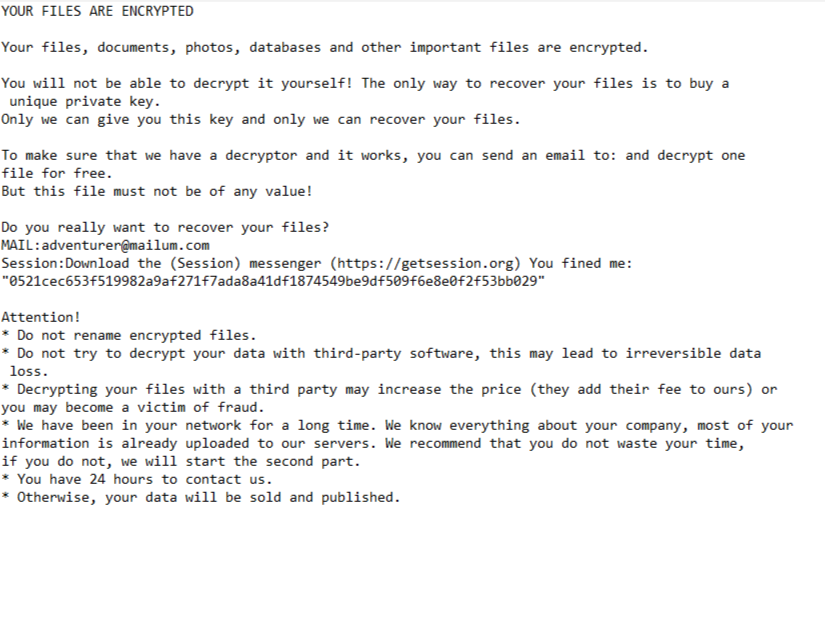
YOUR FILES ARE ENCRYPTED
Your files, documents, photos, databases and other important files are encrypted.
You will not be able to decrypt it yourself! The only way to recover your files is to buy a unique private key.
Only we can give you this key and only we can recover your files.To make sure that we have a decryptor and it works, you can send an email to: and decrypt one file for free.
But this file must not be of any value!Do you really want to recover your files?
MAIL:adventurer@mailum.com
Session:Download the (Session) messenger (https://getsession.org) You fined me: “0521cec653f519982a9af271f7ada8a41df1874549be9df509f6e8e0f2f53bb029”Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data with third-party software, this may lead to irreversible data loss.
* Decrypting your files with a third party may increase the price (they add their fee to ours) or you may become a victim of fraud.
* We have been in your network for a long time. We know everything about your company, most of your information is already uploaded to our servers. We recommend that you do not waste your time, if you do not, we will start the second part.
* You have 24 hours to contact us.
* Otherwise, your data will be sold and published.
Paying the ransom or even engaging with malicious actors is never recommended for several reasons. First, paying the ransom does not guarantee that victims will receive a decryption tool; they remain at the mercy of cybercriminals who have no obligation to help even after the payment is made. Additionally, any money paid to these criminals is likely to support their future illegal activities.
For users with backup copies of their files, recovery can begin as soon as they remove Adventurer ransomware from their systems. However, it’s important to guarantee that the ransomware is completely removed before accessing backups. Otherwise, there’s a risk that backups could also become encrypted. To safely and thoroughly remove Adventurer ransomware, users need to use a trusted anti-malware program.
How does ransomware enter computers?
Users who take risks while online are significantly more susceptible to malware infections. Those with good online habits are much less likely to face such threats, which is why developing better habits is strongly recommended. Additionally, it is important to understand how malware is distributed.
Emails are often used to distribute malware, so being able to identify malicious emails is important. These types of emails are often disguised as order confirmations, shipping updates, or delivery notifications to deceive recipients into interacting with them. Fortunately, many of these emails tend to be generic and can often be identified through glaring grammar and spelling mistakes. Furthermore, if an email addresses you with generic words like User, Member, or Customer, that may also be a sign of a spam or phishing attempt, as legitimate companies usually personalize their communications with the recipient’s name.
It’s also important to note that more sophisticated malicious emails often do not have any obvious mistakes, mention credible details, and directly address the recipients. However, these are typically aimed at specific high-profile targets. But to stay safe, it’s recommended to always scan any unsolicited email attachments using anti-malware software or platforms like VirusTotal.
We should also mention that torrents are a common vector for malware distribution. Many torrent sites lack proper moderation, which enables the upload of malware-laden torrents. Often, malware is hidden in torrents for popular content such as movies, TV shows, and video games. Thus, not only is downloading copyrighted content via torrents essentially content theft, but it also poses serious threats to your computer’s security.
How to remove Adventurer ransomware
Manually trying to remove Adventurer ransomware is not recommended, as it may lead to additional issues or harm to your computer. This type of malware is quite complex, so it’s essential to use anti-malware software for effective removal. If you have a backup, it’s best not to connect to it until you completely delete Adventurer ransomware from your system.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.