Remove Bitco1n ransomware
Bitco1n ransomware is a malicious file-encrypting malware. It’s a type of malware that takes files hostage by encrypting them and blocking users from opening them. Bitco1n ransomware targets all personal files and encrypts them. Encrypted files will have the .Bitco1n extension added to them. As you may have already realized, the encrypted files cannot be opened, and they will remain unopenable unless a special decryptor is used. Unfortunately, only the ransomware operators have this decryptor, and they will demand payment for its release. However, even after paying, there is no guarantee that a working decryptor will be sent to you. Regrettably, only users with backups are able to successfully recover their files at the moment.
The Bitco1n ransomware starts encrypting files as soon as you initiate it by opening a malicious file. You can identify affected files by the .Bitco1n file extension that gets added to all encrypted files. For example, a 1.txt file would be renamed to 1.txt.Bitco1n after encryption. As you’ve likely already noticed, files with this extension cannot be opened. This ransomware targets many different file types, including documents, photos, and images, targeting anything that victims may wish to get back.
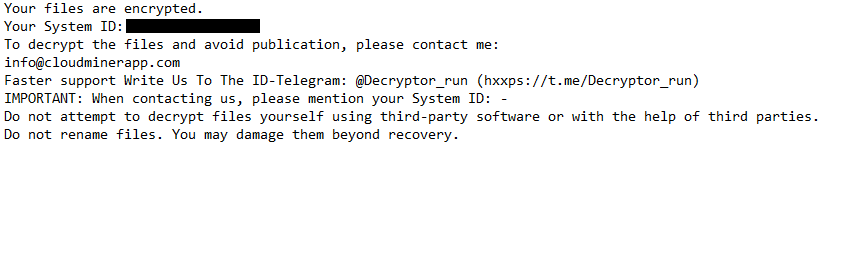
A How To Restore Your Files.txt ransom note is dropped once all targeted files are done being encrypted. The note is brief, as it only explains that files have been encrypted, provides your unique ID, and explains that you need to contact the ransomware operators using the provided contact information. The note does not mention a specific ransom sum, but it’s likely to be at least $1,000.
The full Bitco1n ransomware ransom note is below:
Your files are encrypted.
Your System ID: –
To decrypt the files and avoid publication, please contact me:
info@cloudminerapp.com
Faster support Write Us To The ID-Telegram: @Decryptor_run (hxxps://t.me/Decryptor_run)
IMPORTANT: When contacting us, please mention your System ID: –
Do not attempt to decrypt files yourself using third-party software or with the help of third parties.
Do not rename files. You may damage them beyond recovery.
It is strongly advised against paying the ransom or engaging with the attackers. This is the case with all ransomware. Firstly, there is no guarantee that paying will result in receiving a decryption tool, as victims are placing trust in criminals who have no legal obligation to assist even after payment. Furthermore, any funds sent to these cybercriminals are likely to support their continued illegal activities. What’s more, you may be targeted again as the malicious actors know that you would be willing to pay to get your files back.
If you have a backup, you can begin recovering your files as soon as you remove Bitco1n ransomware from your system. It is very important that the ransomware is fully removed before accessing your backups. Otherwise, the backup files risk being encrypted as well. To safely and effectively eliminate the ransomware, it is recommended to use a trusted and reliable anti-malware program.
Ransomware distribution methods
Poor online habits significantly contribute to malware infections, making it essential to adopt safer habits to minimize risks and prevent future incidents. Equally important is understanding how malware spreads to better protect oneself.
Recognizing malicious emails is an important skill, particularly if your email address has been leaked, as such emails are a prevalent means of malware distribution. Malicious emails often imitate order confirmations, delivery updates, or similar messages to trick users into opening attached files. Fortunately, most malicious emails, unless they are tailored, are generic and can often be identified by poor spelling and grammar. Additionally, generic words like “User,” “Member,” or “Customer” used instead of a recipient’s name may signal a spam or malicious email. Legitimate senders typically address recipients by name, whereas malicious senders rely on generic words because they do not have access to more personal information.
It’s worth mentioning that more sophisticated and personalized malicious emails may be free of mistakes, include credible information, and address recipients by name. To guard against such threats, it is important to scan unsolicited email attachments using anti-malware tools or services like VirusTotal before opening them.
Malware is also commonly distributed via torrents. Poorly regulated torrent sites frequently have malware-infected files disguised as torrents for movies, TV shows, or video games. Thus, downloading copyrighted material via torrents is not only content theft but also exposes users to significant threats.
How to remove Bitco1n ransomware
Do not attempt to remove Bitco1n ransomware manually, as it may lead to additional complications for your computer. Ransomware is a complex form of malware that generally requires advanced anti-malware tools for effective and safe removal. Attempting to resolve the issue on your own could potentially cause even more damage. If you have a backup, ensure that you do not connect to it until the Bitco1n ransomware has been completely removed from your system.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.