Remove Cowa ransomware
Cowa ransomware is a type of malware that encrypts files. It’s a dangerous piece of malware that targets a large variety of file types, encrypts them, and demands payment for their recovery. This ransomware can be identified by the file extension that ends in .cowa added to encrypted files. Unfortunately, encrypted files cannot be opened unless a special decryptor is first used on them. However, getting the decryptor is not easy because only the cybercriminals behind this ransomware have it. They will try to sell the decryptor to you, but engaging with cybercriminals is never recommended, as it does not guarantee that the decryptor will be sent to you. At the moment, only users who have backups can recover their files for certain.
Cowa ransomware can be identified by an extension added to encrypted files. The extension contains your unique ID, and [suppcowa@outlook.com].cowa. Files likely to contain important data, such as photos, videos, images, and documents, are the targets, so they will be encrypted. For example, an encrypted image.jpg file would be renamed to image.jpg.[unique ID].[suppcowa@outlook.com].cowa. Files with this extension cannot be opened unless they are processed through a decryptor, which is not freely available and requires payment.
When it’s done encrypting your files, a +README-WARNING+.txt ransom note will be dropped. The note informs victims that their files have been encrypted and that payment is required to obtain the decryptor. Unfortunately, this claim is accurate, as the decryptor will not be provided for free. The note does not specify the price for the decryptor but instructs victims to contact the cybercriminals. However, even if payment is made, there is no guarantee that a functional decryptor will be provided.
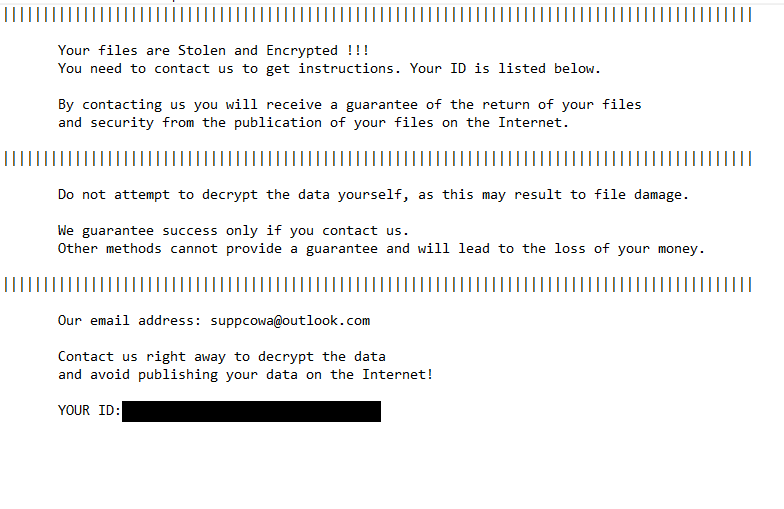
The full Cowa ransomware note is below:
|||||||||||||||||||||||||||||||||||||||||
Your files are Stolen and Encrypted !!!
You need to contact us to get instructions. Your ID is listed below.By contacting us you will receive a guarantee of the return of your files
and security from the publication of your files on the Internet.|||||||||||||||||||||||||||||||||||||||||
Do not attempt to decrypt the data yourself, as this may result to file damage.
We guarantee success only if you contact us.
Other methods cannot provide a guarantee and will lead to the loss of your money.|||||||||||||||||||||||||||||||||||||||||
Our email address: suppcowa@outlook.com
Contact us right away to decrypt the data
and avoid publishing your data on the Internet!YOUR ID: –
When it comes to cybercriminals, keep in mind that they have no obligation to help victims, even if a ransom is paid. They are not a legitimate business, so they’re not obligated to help victims. Additionally, victims’ payments go towards future criminal activities. Ultimately, the decision to pay the ransom is yours, but it’s important to understand the risks involved to make an informed choice.
If you have a backup, remove Cowa ransomware from your computer first and only then connect to your backup. Make sure to use an antivirus program for this task; trying to remove the ransomware manually might allow it to recover later on. If any part of it remains, the ransomware could recover, and accessing your backup while the ransomware is still active could lead to your backed-up files being encrypted as well. Therefore, using antivirus software is strongly recommended.
If you have no backups, the only option may be to wait for a free decryptor to be released. However, there’s no guarantee that a free Cowa ransomware decryptor will become available. If it is released, you can find it on NoMoreRansom.
Ransomware distribution methods
Ransomware infections often originate from malicious email attachments, commonly known as malspam. Cybercriminals purchase lists of email addresses and launch malspam campaigns with malicious attachments. Oftentimes, these emails are low-effort. The low quality of these emails can make them easier to identify as malicious, as long as users know what to look for.
A key sign of a malicious email is the presence of grammar and/or spelling mistakes, particularly in emails claiming to be from reputable companies/organizations, delivery services, or government agencies. Legitimate emails are typically mistake-free, as mistakes are considered unprofessional. If you notice mistakes, be cautious and do not open attachments or click on any links.
Another warning sign is you being addressed using words like User, Member, or Customer. If a sender claims to be from a company whose services you use but does not address you by name, the email is likely spam or malspam. The generic greeting often stems from attackers having limited access to personal user data.
However, it should also be mentioned that some malspam can be highly sophisticated, usually when targeting specific people or companies. For this reason, scanning any unsolicited email attachments with antivirus software or services like VirusTotal is strongly recommended.
Lastly, downloading copyrighted content through torrents poses significant risks. Torrent sites are often poorly monitored, allowing cybercriminals to upload torrents with malware in them. Besides the fact that downloading copyrighted content via torrents is illegal, it also poses significant risks.
How to remove Cowa ransomware
Manually trying to remove Cowa ransomware is not a good idea because it’s a sophisticated infection. The safest approach is to use an anti-virus software to remove Cowa ransomware from your device. This software will take care of the removal process for you. Once Cowa ransomware has been successfully removed, you can then access your backups and restore your files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.