Remove “Data From All Your Devices Is Copied To My Servers” sextortion email
The “Data From All Your Devices Is Copied To My Servers” email is part of a sextortion email spam campaign that tries to blackmail recipients into paying $1,300. The email claims that the recipient’s computer has been infected with malware (specifically, a trojan horse), which allows its operator to monitor the infected computer. This has supposedly allowed the trojan operator to spy on the user while they were watching pornography. The scammers threaten to release a video of the user watching pornography if they do not agree to pay the requested sum. The email’s contents are completely false; recipients’ computers have not been infected with malware, nor is there a video of them watching pornography. The email can be safely ignored.
The vast majority of sextortion scam emails typically follow a similar pattern, regardless of the cybercriminal group behind them. Scammers usually start with menacing subject lines aimed at capturing the recipient’s attention. These alarming headlines are designed to provoke curiosity and entice users to open the email. In this case, the subject line is “Data From All Your Devices Is Copied To My Servers”. That will immediately catch many users’ attention, prompting them to open the email.
Once the email is opened, recipients are confronted with a threatening wall of text. The “Data From All Your Devices Is Copied To My Servers” email is written in a very threatening tone and has many grammar and spelling mistakes. The sender claims to have watched and recorded the recipient while they were viewing adult content, insisting that a payment of $1,300 be made to a specified crypto wallet if the recipient wants to avoid having the video shared with their contacts. This was supposedly possible because the sender infected the recipient’s computer with malware.
This email serves as a typical example of a sextortion scam, and all the claims within it are false. There is no video, and there is no need to pay anything. Despite the low-effort nature of this extortion method, it remains one of the more convincing variations. Other extortion emails may threaten violence, such as assassination attempts or bomb threats at workplaces. During the pandemic, there had even been scams that claimed they would spread COVID-19 to recipients and their families unless a payment was made. Generally, these scams do not deceive many people, as indicated by the small amounts sent to their wallet addresses. However, the persistence of these scams suggests they still yield enough profit for the scammers to continue their operations.
If you receive the “Data From All Your Devices Is Copied To My Servers” sextortion email, the best course of action is to delete it. Unfortunately, if you have already sent Bitcoin to the provided address, it cannot be retrieved, as cryptocurrency transactions are irreversible.
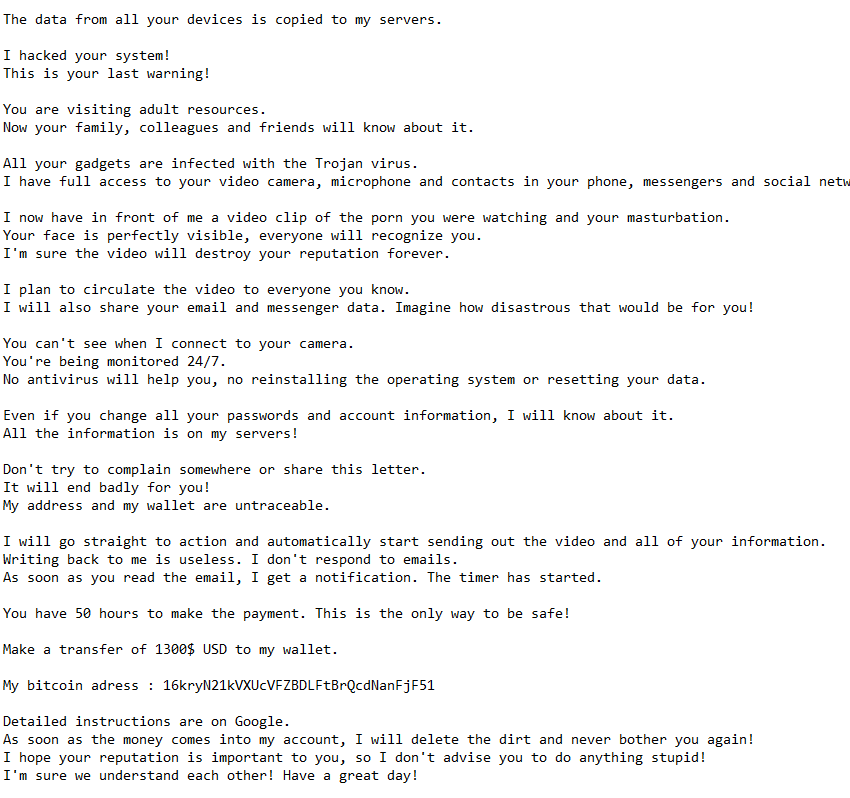
The full “Data From All Your Devices Is Copied To My Servers” email is below:
Subject: The data from all your devices is copied to my servers.
The data from all your devices is copied to my servers.
I hacked your system!
This is your last warning!You are visiting adult resources.
Now your family, colleagues and friends will know about it.All your gadgets are infected with the Trojan virus.
I have full access to your video camera, microphone and contacts in your phone, messengers and social networks.I now have in front of me a video clip of the porn you were watching and your masturbation.
Your face is perfectly visible, everyone will recognize you.
I’m sure the video will destroy your reputation forever.I plan to circulate the video to everyone you know.
I will also share your email and messenger data. Imagine how disastrous that would be for you!You can’t see when I connect to your camera.
You’re being monitored 24/7.
No antivirus will help you, no reinstalling the operating system or resetting your data.Even if you change all your passwords and account information, I will know about it.
All the information is on my servers!Don’t try to complain somewhere or share this letter.
It will end badly for you!
My address and my wallet are untraceable.I will go straight to action and automatically start sending out the video and all of your information.
Writing back to me is useless. I don’t respond to emails.
As soon as you read the email, I get a notification. The timer has started.You have 50 hours to make the payment. This is the only way to be safe!
Make a transfer of 1300$ USD to my wallet.
My bitcoin adress : 16kryN21kVXUcVFZBDLFtBrQcdNanFjF51
Detailed instructions are on Google.
As soon as the money comes into my account, I will delete the dirt and never bother you again!
I hope your reputation is important to you, so I don’t advise you to do anything stupid!
I’m sure we understand each other! Have a great day!
Why do scammers have my email address?
Sextortion scam emails often allege that your email and computer have been hacked, and that’s why you received the email, but these claims are not true. If you receive such an email, it’s usually because your email address has been leaked in a data breach from a service you use. To check if your email address has been leaked, you can visit HaveIBeenPwned. Unfortunately, receiving one sextortion email can lead to more, and you may also receive emails that might contain malware, which is why you need to be wary of any unsolicited emails.
If you get an email threatening to disclose an explicit video of you, it’s understandable to feel anxious, especially if it includes a password you recognize. However, there’s a simple explanation for why the sender may have your password that doesn’t involve malware. Your password could have been leaked in a data breach, particularly if the service where you used that password has weak security measures. As a result, your email and password might be part of a database along with thousands of others, often sold on hacker forums to scammers and malicious actors. You can verify if your password has been compromised by visiting the same HaveIBeenPwned website. If you discover that your password has been leaked, it’s essential to change it immediately for all accounts that use it. Additionally, make sure to use unique and strong passwords for different accounts to enhance your overall security.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.