Remove Dev ransomware
Dev ransomware is file-encrypting malware from the Makop ransomware family. It targets all important files on the computer and encrypts them, essentially taking them hostage. This version can be identified by the extension that ends in .dev. All encrypted files will have that extension, and you will not be able to open them. This ransomware not only encrypts files but also steals them to pressure users into paying the ransom. At the moment, only users who have backups can recover their files for free, as no free Dev ransomware decryptor is available.
Dev ransomware, part of the Makop ransomware family, can be identified by the unique file extension it adds to encrypted files: .[unique ID].[decryptdevelop@outlook.com].dev. Each victim is assigned a randomly generated unique ID, enabling the cybercriminals to differentiate between victims. This extension also includes the attackers’ contact email address. For example, a 1.txt file would become 1.txt.[unique ID].[decryptdevelop@outlook.com].dev after encryption. Encrypted files are rendered unopenable, with the ransomware primarily targeting documents, photos, and images—files of significant value to victims to increase the likelihood of payment.
Upon completing the encryption process, a ransom note titled +README-WARNING+.txt is created, informing victims that files have been encrypted and stolen. The perpetrators demand payment for a decryption tool, though the specific ransom amount is not disclosed. They also threaten to publish all stolen files on the Internet if the victim does not agree to pay the ransom.
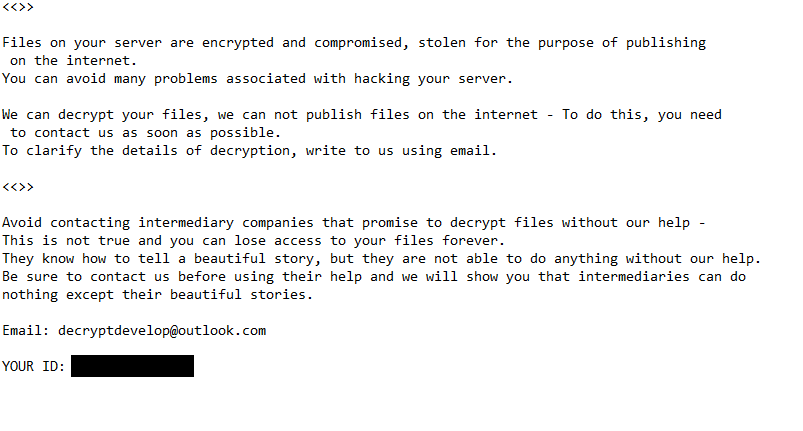
The full Dev ransomware ransom note is below:
Files on your server are encrypted and compromised, stolen for the purpose of publishing on the internet.
You can avoid many problems associated with hacking your server.We can decrypt your files, we can not publish files on the internet – To do this, you need to contact us as soon as possible.
To clarify the details of decryption, write to us using email.Avoid contacting intermediary companies that promise to decrypt files without our help – This is not true and you can lose access to your files forever.
They know how to tell a beautiful story, but they are not able to do anything without our help.
Be sure to contact us before using their help and we will show you that intermediaries can do nothing except their beautiful stories.Email: decryptdevelop@outlook.com
YOUR ID: –
Paying the ransom or engaging with cybercriminals is generally not a good idea for several reasons. Firstly, there is no assurance that payment will result in receiving a functioning decryption tool, as victims are dealing with criminals who have no legal obligation to assist after payment. Moreover, any funds provided to these criminals will contribute to financing their future illegal activities.
For those with backups, file recovery can begin after they successfully remove Dev ransomware from their systems. However, it is crucial to ensure that the ransomware is entirely removed before accessing backups, as doing so while the ransomware remains active will lead to the encryption of those files as well, resulting in permanent loss. Furthermore, using a reliable anti-malware program to completely delete Dev ransomware is essential, as ransomware is a sophisticated and complex threat.
How does ransomware enter computers?
Poor online habits significantly increase the risk of malware infections, while safer practices greatly reduce the likelihood of such issues. Developing better online habits and using an anti-malware program is one of the most effective defenses against malware for regular users. Understanding how malware spreads is equally important.
If your email address has been leaked, you need to be able to identify malicious emails, as emails are a common method of malware distribution. Most malicious emails are generic and easier to identify due to noticeable grammar and spelling mistakes. The mistakes are especially noticeable when the malicious emails are made to look like they’re sent by legitimate companies, such as parcel delivery companies or government organizations. Additionally, generic greetings using words like “User,” “Member,” or “Customer” may indicate a potentially malicious email. Legitimate companies typically personalize their emails with the recipient’s name, whereas malicious senders rely on generic language due to a lack of personal information.
However, we should mention that more sophisticated phishing attempts usually have no mistakes, mention credible information, and even address recipients by name, making them harder to detect. Under the right circumstances, even cautious users may fall victim. To protect themselves from malicious threats, users should always scan unsolicited email attachments with anti-malware software or services like VirusTotal.
Another common method of malware distribution is torrents. Many torrent sites are poorly moderated, allowing cybercriminals to upload torrents with malware in them. Torrents for popular entertainment content like movies, TV shows, and video games often come bundled with malware. Users should also keep in mind that downloading copyrighted content through torrents is not only theft but also puts their computers at significant risk.
How to remove Dev ransomware
Manually trying to remove Dev ransomware is not recommended unless you are completely sure about what you need to do, as it could lead to more issues for your computer. Ransomware is a very sophisticated infection, and it’s highly recommended to use an anti-malware program to remove it correctly. If you have a backup, make sure not to connect to it until you completely delete Dev ransomware from your system.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.