Remove Eqza ransomware (.eqza virus)
Eqza ransomware is file-encrypting malware from the Djvu/STOP ransomware family. It’s a dangerous malware infection because it encrypts personal files and could lead to permanent file loss if users have no backups. The ransomware can be recognized by the .eqza extension added to encrypted files. Unfortunately, files with that extension will not be openable unless you first use a decryptor on them, which will not be easy to get.
Ransomware infections can be identified by the unique extensions they add to encrypted files. In this case, the extension is .eqza. For instance, an encrypted image.jpg file would become image.jpg.eqza. Files with this extension cannot be opened. This ransomware targets all types of personal files, including photos, videos, documents, and more.
The moment this ransomware is activated, it begins encrypting files immediately. To mislead victims, it even displays a fake Windows update notification. After completing the encryption, Eqza ransomware drops a _readme.txt ransom note in folders that contain the encrypted files. This note mirrors those typically found in other ransomware variants from the same family. It outlines that the files have been encrypted and provides instructions on how to decrypt them. Unfortunately, this process involves paying a ransom to the attackers. The cost for the Eqza ransomware decryptor is set at $980, but a 50% discount is advertised for those who reach out within the first 72 hours. However, paying the ransom is risky as there’s no guarantee you will receive the decryptor, given that you are dealing with criminals. There are numerous accounts of victims who paid but never received the decryptor. While the choice to pay or not is entirely up to you, it’s crucial to understand the associated risks.
The full _readme.txt ransom note is below:
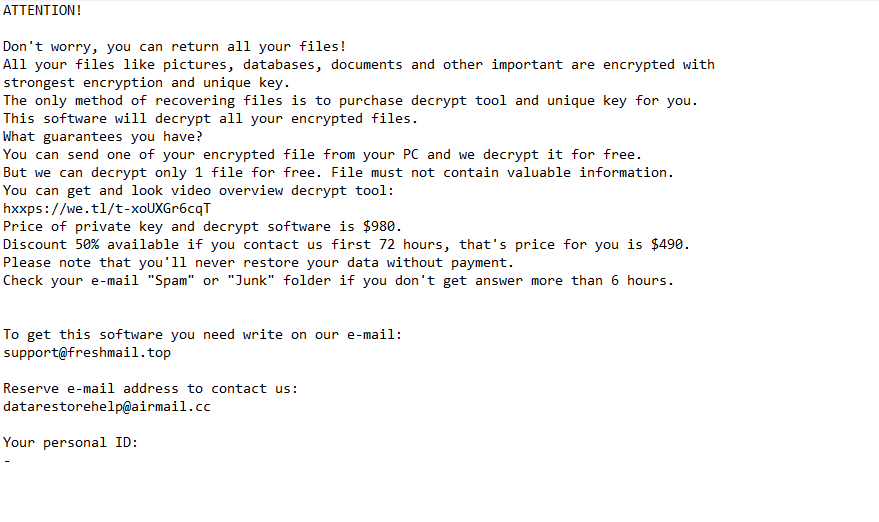
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-Y6UIMfI736
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
–
If you don’t have backups of your files, recovering the encrypted data isn’t currently possible. Nevertheless, a free decryptor might be developed in the future. We suggest backing up the encrypted files and keeping an eye out for a free Eqza ransomware decryptor. NoMoreRansom is a reliable resource for decryptors.
Once you have successfully removed Eqza ransomware from your system, you can start recovering your files if you have a backup. Just ensure that you fully remove Eqza ransomware before connecting to your backup to avoid encrypting those files as well.
Ransomware distribution methods
Spam emails are a primary method through which cybercriminals spread malware. This technique requires minimal effort and skills. Malicious actors often buy lists of email addresses from various hacker forums and then send out mass spam emails. These emails usually stand out for several reasons; they aren’t aimed at specific individuals and target many users with the same email instead. As a result, the emails lack any personalization (e.g., addressing the recipient by name). Additionally, they often contain numerous grammar and spelling mistakes, which makes them even more suspicious. Often, the senders impersonate legitimate organizations, claiming to represent services that users often use. However, the presence of these mistakes clearly indicates that the email is not from a trustworthy source. Furthermore, when contacting users, these emails usually use generic words like “Customer,” “User,” or “Member” instead of using the recipient’s name. A legitimate company will address you by your name in all emails.
To protect yourself from opening harmful content, it’s advisable to scan any unsolicited email attachments with anti-virus software or VirusTotal. Developing this habit, along with regularly backing up your files, can help prevent numerous issues.
Malware is also distributed through torrents. It’s common knowledge that torrent sites are often poorly regulated, making them easy targets for malicious actors who post infected files masquerading as torrents for popular movies, TV shows, video games, or software. This is particularly prevalent with newly released movies. For instance, when a new Marvel film is released, you can expect to find numerous malicious torrents for that movie. It’s important to note that downloading copyrighted content for free through torrents is not only illegal but also poses significant risks to your computer’s safety.
Eqza ransomware removal
To effectively remove Eqza ransomware from your computer, it’s essential to use anti-virus software, as this type of malware is quite complex. We strongly advise against attempting to delete Eqza ransomware manually unless you have extensive knowledge, as this could lead to additional problems or might not fully eliminate the ransomware. If any parts of it remain and you connect to your backup, it could result in the encryption of those backed-up files as well, jeopardizing your chances of recovery. Therefore, using anti-virus software is the best approach to ensure the ransomware is completely removed. After it’s gone, you can proceed with recovering your files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.