Remove Gunra ransomware
Gunra ransomware is a file-encrypting type of malware. The ransomware will take all important files hostage by encrypting them, and demand a payment to recover them. In addition to encrypting the files, the malicious actors operating this ransomware claim to have stolen the files as well and threaten to publish them on the dark web if payment is not made. This ransomware can be identified by the .ENCRT extension added to encrypted files. Unfortunately, there is currently no free Gunra ransomware decryptor, and only users who have backups can recover files for free.
Once Gunra ransomware manages to get into a computer, it starts encrypting files right away. The primary targets are documents, photos, and videos. Encrypted files can be easily identified by the extensions that are added to their names. This particular ransomware appends the .ENCRT extension. For example, a text.txt file would change to text.txt.ENCRT.
When it’s done encrypting files, the ransomware creates a R3ADM3.txt ransom note. This note explains that files have been encrypted, as well as stolen. Victims who want to recover their files are instructed to download the Tor browser and access the linked site to contact the ransomware operators. The note does not mention how much victims would be required to pay for the decryptor, but it’s likely to be several if not more thousand dollars. Malicious actors also threaten to publish the stolen data on the dark web if victims do not agree to pay.
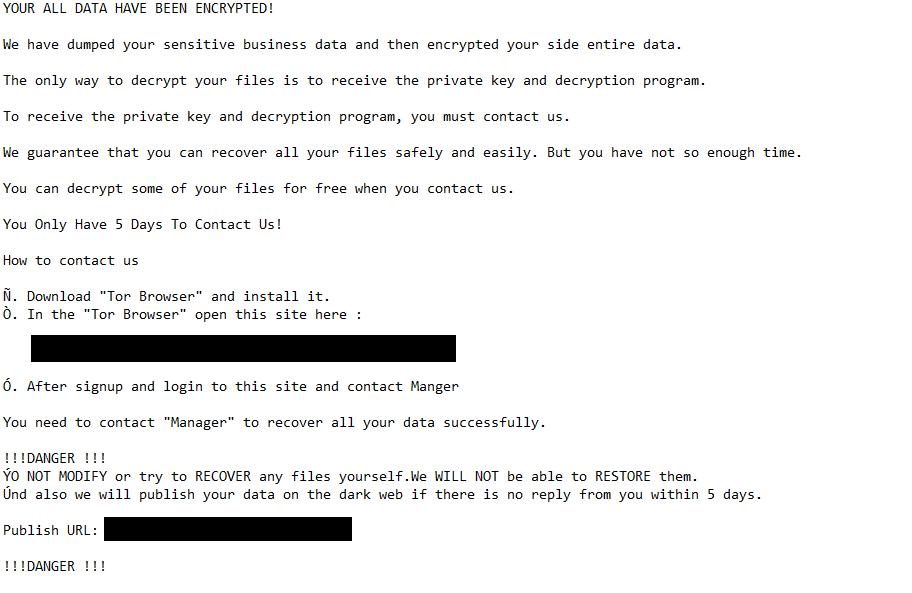
The R3ADM3.txt ransom note dropped by Gunra ransomware is below:
YOUR ALL DATA HAVE BEEN ENCRYPTED!
We have dumped your sensitive business data and then encrypted your side entire data.
The only way to decrypt your files is to receive the private key and decryption program.
To receive the private key and decryption program, you must contact us.
We guarantee that you can recover all your files safely and easily. But you have not so enough time.
You can decrypt some of your files for free when you contact us.
You Only Have 5 Days To Contact Us!
How to contact us
Ñ. Download “Tor Browser” and install it.
Ò. In the “Tor Browser” open this site here :–
Ó. After signup and login to this site and contact Manger
You need to contact “Manager” to recover all your data successfully.
!!!DANGER !!!
ÝO NOT MODIFY or try to RECOVER any files yourself.We WILL NOT be able to RESTORE them.
Únd also we will publish your data on the dark web if there is no reply from you within 5 days.Publish URL: –
!!!DANGER !!!
Engaging with cybercriminals and paying a ransom is strongly discouraged. What users need to keep in mind is that they are dealing with cybercriminals who have no obligation to assist them, even after receiving payment. There’s no assurance that victims will receive a working decryptor or that their files won’t be posted on the dark web. Unfortunately, many who have paid ransoms in the past have not received effective decryptors. Whether to pay is your decision, but you need to be aware of the risks associated with it.
For those with backups, the recovery process can begin immediately after they remove Gunra ransomware from their computers. It’s highly recommended to use an anti-malware program, as this particular infection is quite sophisticated. Once the ransomware is eliminated, it’s safe to connect to a backup. For users without backups, the only course of action is to back up the encrypted files and wait for a free decryptor for Gunra ransomware to become available. However, there’s no guarantee that such a tool will be released.
How does ransomware infect computers?
Malicious actors use all kinds of methods to spread ransomware, including torrents, email attachments, and harmful links or ads. Users with poor online habits are considerably more susceptible to infections because they’re more likely to engage in risky online activities (e.g., clicking on random links). If users take the time to develop better habits, they should be able to avoid a lot of malware infections.
Emails are a very common method for distributing malware. Emails that carry malware can be disguised as notifications for parcel deliveries or order confirmations. The emails may mention that the attached files are important documents or claim that expensive purchases have been made. This tactic effectively pressures users into acting without thoroughly screening the emails. However, if checked closely, tell-tale signs of malicious emails can be identified. Typically, these emails contain noticeable grammar and spelling mistakes—something that is rarely present in legitimate emails. Additionally, they often address recipients using generic words like User, Member, or Customer while claiming that recipients are clients. Most legitimate companies personalize their emails by using the recipient’s name, while malicious actors usually do not have access to such information and have to use generic words.
In cases where malicious emails are aimed at specific people or companies, they are typically much more sophisticated. These targeted emails often lack the usual red flags, address the recipient by name, and include relevant details that lend them credibility. Therefore, it’s always advisable to avoid opening unsolicited email attachments unless they’ve been scanned with anti-virus software or checked via VirusTotal.
Torrents are another common avenue for malware distribution among cybercriminals. It’s well-known that torrent sites often lack effective moderation, allowing malicious actors to upload infected torrents. In particular, torrents for entertainment content, such as movies, TV shows, and video games, frequently contain malware. Engaging in the piracy of copyrighted content is not only theft but also jeopardizes your computer and personal data.
How to remove Gunra ransomware
Ransomware is a sophisticated type of malware, and it’s crucial to remove it using a professional program. Attempting to manually remove Gunra ransomware virus could potentially lead to more harm to your device. Therefore, it is highly recommended to use an anti-virus program for this purpose. Once the ransomware has been completely removed and is no longer detected, you can safely reconnect to your backup to begin recovering your files. Be cautious, though: if ransomware is still present when you access your backup, it could also encrypt those backed-up files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.