Remove Hgfu ransomware (.hgfu virus)
Hgfu ransomware is part of the Djvu/STOP ransomware family. It’s a type of malware that takes files hostage by encrypting them. This ransomware version can be identified by the .hgfu extension added to encrypted files. Unfortunately, you will not be able to open any encrypted files unless you first decrypt them using a special decryptor. However, only the ransomware operators currently have the Hgfu ransomware decryptor, and they will demand a payment of $980 for it. However, paying the requested ransom does not guarantee file recovery. Only users who have backups can recover their files at the moment.
Hgfu ransomware is a variant of the Djvu/STOP ransomware family. Each new version can be identified by the file extension it adds to encrypted files, which, in this case, is .hgfu. For instance, a 1.txt file would be altered to 1.txt.hgfu once encrypted. If your device becomes infected with Hgfu ransomware, your personal files, such as photos, videos, and documents, will have this extension, rendering them unopenable unless you use a specific decryptor on them first.
After encrypting the files, the ransomware drops a _readme.txt ransom note that provides details on obtaining the decryptor. Unfortunately, to acquire the Hgfu ransomware decryptor, you would need to pay $980. If you reach out to the malware operators within the first 72 hours, they claim you can receive a 50% discount. They also offer to decrypt one file for free—provided it doesn’t contain sensitive information—as proof of their decryptor’s effectiveness. However, the reliability of these claims is questionable, and it is generally not a good idea to engage with cybercriminals.
Paying the ransom poses several risks. The most significant concern is that you are dealing with criminals who have no obligation to send you the decryptor after receiving payment. Many victims have experienced this. Ultimately, deciding whether to pay the ransom is up to you, but it’s important to be fully aware of the potential risks involved.
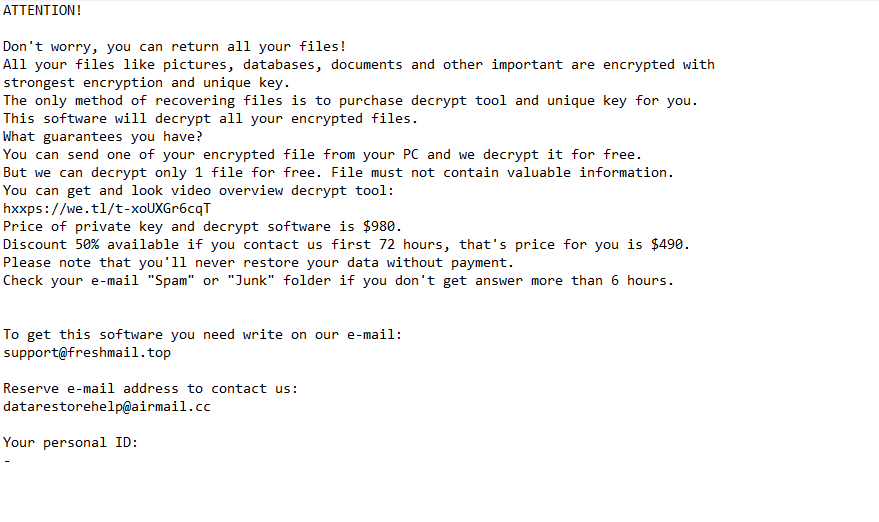
The full _readme.txt ransom note text is as follows:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-iTbDHY13BX
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
–
If you have backups of your files, you can connect to them and initiate the recovery process once you remove Hgfu ransomware from your computer. It’s crucial that the ransomware is completely gone before accessing your backups, as otherwise, the files in your backup could also be encrypted. To delete Hgfu ransomware, use a reliable anti-malware program to prevent any further damage to your computer.
If you don’t have a backup, your only option is to save the encrypted files and wait for a free Hgfu decryptor to become available. NoMoreRansom is an excellent resource for obtaining free decryptors. If you can’t find a Hgfu ransomware decryptor on that site, it’s unlikely you’ll find it anywhere else.
How did Hgfu ransomware enter your computer?
Hgfu ransomware spreads through typical channels such as torrents, email attachments, and harmful links or ads. By developing safe browsing habits, you can significantly reduce your risk of infection. Familiarizing yourself with common malware distribution techniques is also an effective way to protect yourself.
One prevalent method of spreading malware is via email. Malicious attachments are often disguised as notifications for parcel deliveries or order confirmations. Users tend to engage with these emails, especially when large sums of money are mentioned. For instance, a malicious email may mimic an order confirmation and mention a few hundred dollars. These emails might also urge users to review an attached document urgently. However, they usually contain grammar or spelling mistakes, which serve as a red flag—legitimate emails rarely have any mistakes.
The way an email addresses you can indicate its legitimacy. Companies you interact with typically address you by your name, while malicious emails usually use generic words like User, Member, or Customer, as cybercriminals usually do not have access to more personal information beyond your email address.
Malicious actors often target specific users/companies with more sophisticated emails. These emails are generally free of mistakes, use the recipient’s name, and include details that enhance their credibility. This highlights the importance of scanning all email attachments using anti-virus software or tools like VirusTotal before opening them.
Furthermore, if you use torrents for pirated content, you’re not just stealing content—you may also be compromising your computer and data. Malware is frequently found in torrents, particularly for popular movies, TV shows, and video games. Many torrent sites lack proper moderation, and many users are unaware of what a malicious torrent might look like, making it an effective method for distributing malware.
How to remove Hgfu ransomware
Ransomware is a very sophisticated type of infection, making it essential to use a reliable anti-malware program to remove Hgfu ransomware from your system. Attempting to manually remove Hgfu ransomware could lead to further damage to your device, so it’s best to avoid that. If you have a backup, you can access it once you’ve successfully removed the ransomware from your computer.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.