Remove “Human Resource Internal Memo” email
The “Human Resource Internal Memo” email is part of a phishing campaign that tries to steal users’ email login credentials. The email is disguised as a notification email from the recipients’ workplace HR Department, and informs them about the 2025 Annual Salary compensation Report. Supposedly, recipients can check the report by clicking on the provided link. If users were to click on the link, they would be taken to a fake Gmail sign-in page and asked to type in their email account password. If users were to do that, their email login credentials would be stolen by the malicious actors operating this phishing campaign.
Malicious email phishing campaigns are common because these types of login credentials are very valuable. While phishing emails are often very obvious and easy to identify, all it takes is the right timing and circumstances for someone to fall for it. Emails from this particular campaign claim that the recipient’s company’s HR Department has published its annual Salary compensation report, which can be viewed by clicking on the provided link. According to the email, the report shows employees who have not yet fulfilled the 2025 Annual salary compensation in red, while those who have will be marked in green.
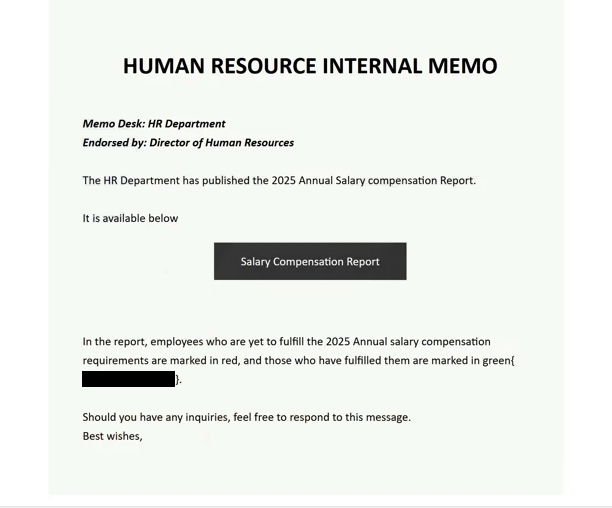
The full “Human Resource Internal Memo” email is below:
Subject: Annual Payroll review
HUMAN RESOURCE INTERNAL MEMO
Memo Desk: HR Department
Endorsed by: Director of Human ResourcesThe HR Department has published the 2025 Annual Salary compensation Report.
It is available below
Salary Compensation Report
In the report, employees who are yet to fulfill the 2025 Annual salary compensation requirements are marked in red, and those who have fulfilled them are marked in green{ – }.
Should you have any inquiries, feel free to respond to this message.
Best wishes,Unsubscribe
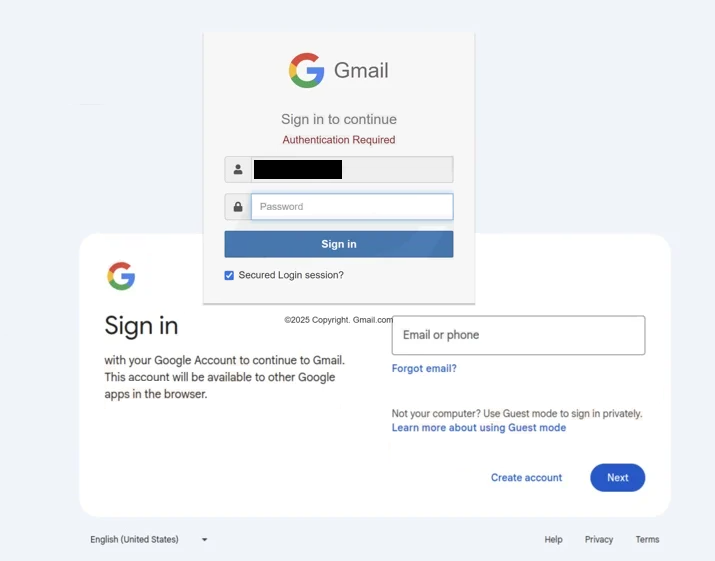
If users were to click on the “Salary Compensation Report” button, they would be taken to a fake Gmail login page (shown below). The site is a poor imitation of the legitimate Gmail login page, but it may work on users who are in a rush.
If users enter their passwords on this site, the credentials will be immediately stolen. The malicious actors operating this phishing campaign will either use the credentials to access the accounts or sell them to other cybercriminals. Whatever the case may be, users would lose access to their accounts.
Email account login credentials are very valuable to malicious actors for several reasons. First of all, if users use the same email account for a long time, it will have a lot of personal and sensitive information, which malicious actors can use for various purposes. What’s more, email accounts are connected to various other accounts, and gaining access to the email could give access to other accounts as well.
If you have interacted with the email, clicked on the link, and typed in your password, you need to change your password immediately. If you cannot access your account and no account recovery options work, you need to disconnect the email from all accounts to prevent them from being hijacked as well.
How to recognize phishing emails
Unless you are the specific target of a particular campaign, you’ll likely mostly encounter generic malicious emails. Such emails are often fairly easy to identify because they are not personalized in any way. This particular “Human Resource Internal Memo” email is themed and is likely sent on a massive scale, so it’s unlikely that many users will fall for it.
Phishing emails like “Human Resource Internal Memo” are very easy to identify because all you need to do is check the sender’s email address. If it does not match your company’s email address, it’s phishing. We should mention, however, that malicious actors try to imitate legitimate email addresses, so you need to be very cautious about additional and switched-up letters. When in doubt, a little research will be very helpful.
Generic phishing emails are often full of grammar and spelling mistakes as well, which immediately gives them away. While this “Human Resource Internal Memo” email does not have obvious spelling mistakes, the way it’s written does not look professional enough to come from a company’s HR department. The fact that the email does not address you in any way is also suspicious. Oftentimes, malicious emails address users as “Users”, “Customers”, or “Members”, or do not address them at all. Legitimate emails generally address recipients by name to make the correspondence feel more personal.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.