Remove Jawr ransomware (.jawr virus)
Jawr ransomware is file-encrypting malware from the Djvu/STOP ransomware family. These types of malware infections take personal files hostage by encrypting them and demanding a payment for a decryptor to recover them. This ransomware is identifiable by the .jawr extension added to encrypted files. Unfortunately, unless you decrypt the files first, you will not be able to open them. And obtaining a decryptor is not going to be easy. The malicious actors operating this ransomware will offer a decryptor for a payment, but even paying does not guarantee you’ll be able to recover your files.
Jawr ransomware is designed to target all of your personal files, which include photos, documents, videos, and more. Once encrypted, these files will have the .jawr extension added to them. For instance, image.jpg will become image.jpg.jawr. You won’t be able to access any files with this extension unless you first use a decryptor on them. Unfortunately, the only people who have this decryptor are the cybercriminals behind the ransomware, and they won’t provide it for free.
During the encryption process, the ransomware will show a fake Windows update window to distract the user from what’s really happening. And once the encryption is complete, it will drop a _readme.txt ransom note. The note is fairly standard and explains how to obtain the decryptor. Unfortunately, this requires paying a ransom. The requested amount is $980, but according to the note, those who reach out within the first 72 hours can supposedly get a 50% discount. However, this claim is questionable at best. Paying the ransom is generally discouraged; after all, you’re dealing with criminals, and there are no guarantees that you’ll receive the decryptor after payment.
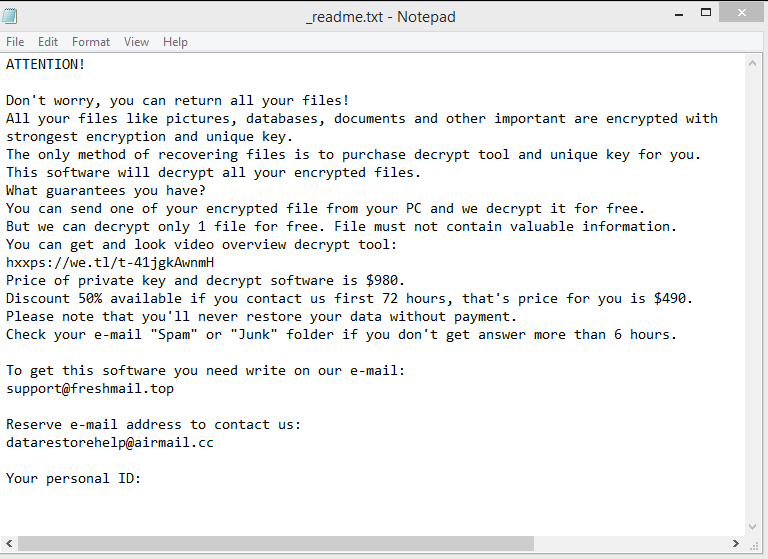
The full _readme.txt ransom note is below:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-iu965qqEb1
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
Once you remove Jawr ransomware with anti-malware software, you can connect to your backup if you have one. It’s important to emphasize that using anti-malware software is very important to deal with ransomware. This type of infection is complex, and attempting to manually remove it can lead to further damage. Additionally, if Jawr ransomware isn’t completely removed from your system before accessing your backup, it could encrypt your backup files too.
If you do not have a backup, make sure to securely back up the encrypted files and wait for a free Jawr ransomware decryptor, which is not currently available but may be in the future.
Common ransomware distribution methods
Malicious threats, such as ransomware, are often spread using methods like emails, torrents, and advertisements. Users with poor browsing habits are more susceptible to infections on their computers. Therefore, one of the most effective ways for everyday users to prevent malware is by developing better browsing habits. This includes refraining from opening random email attachments, clicking on ads while visiting high-risk websites, and pirating content through torrents.
The most common way users inadvertently download ransomware is by opening attachments found in malicious spam emails. This method is low-effort for cybercriminals and surprisingly effective. They can easily acquire large lists of email addresses from hacker forums and send out generic emails with harmful attachments. These emails often resemble emails from legitimate companies, but many contain noticeable grammar and spelling mistakes. Such obvious mistakes are strong indicators of a malicious email. Furthermore, these emails tend to use generic greetings like “User,” “Customer,” or “Member.” In contrast, legitimate emails from companies usually address users by their names. Since cybercriminals don’t have access to the potential victims’ names, they resort to these generic words. However, some malspam can be sophisticated, so it’s always a good idea to scan any unsolicited email attachments using anti-virus software or services like VirusTotal.
Additionally, users who download content via torrents face a heightened risk of malware infections. Many torrent sites are poorly managed, allowing malicious actors to upload harmful content disguised as legitimate torrents for movies, TV shows, video games, and software. This is especially prevalent with torrents for popular releases; for instance, when a new Marvel movie is released, its torrents are frequently laced with malware.
Jawr ransomware removal
We do not recommend attempting to manually remove Jawr ransomware, as this could inadvertently cause more harm. These types of infections can be particularly challenging to get rid of on your own. If the removal is incomplete, the ransomware might be able to restore itself. Additionally, connecting to your backup while the ransomware is still active could result in the encryption of your backed-up files as well. It’s best to use reliable anti-malware software to handle Jawr ransomware removal. Once the ransomware is completely eliminated, you can start the process of recovering your files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.