Remove Jlaz ransomware (.jlaz virus)
Jlaz ransomware (or .jlaz virus) is file-encrypting malware from the Djvu/STOP ransomware family. Because it targets and encrypts personal files, it’s considered to be a very dangerous infection. It can be identified by the .jlaz extension added to all encrypted files. Unfortunately, you will not be able to open files with that extension unless you first use a decryptor on them. However, getting a decryptor is not going to be easy, even if you pay. At the moment, only users who have backups can recover their files for certain.
Jlaz ransomware is a serious threat that primarily encrypts personal files, making recovery difficult. It targets important documents, photos, videos, and other valuable files. Once these files are encrypted, they have a .jlaz extension. For example, a 1.txt file would become 1.txt.jlaz after encryption. These files cannot be accessed until a decryptor is used on them. Additionally, a _readme.txt ransom note is dropped, informing the victim that their files have been encrypted and demanding a payment of $980 for the decryption key. The note also mentions that a 50% discount will be given to users who make contact within the first 72 hours of file encryption. What’s more, the ransomware operators offer to decrypt one file for free as proof that their decryptor works, as long as it does not contain any important information.
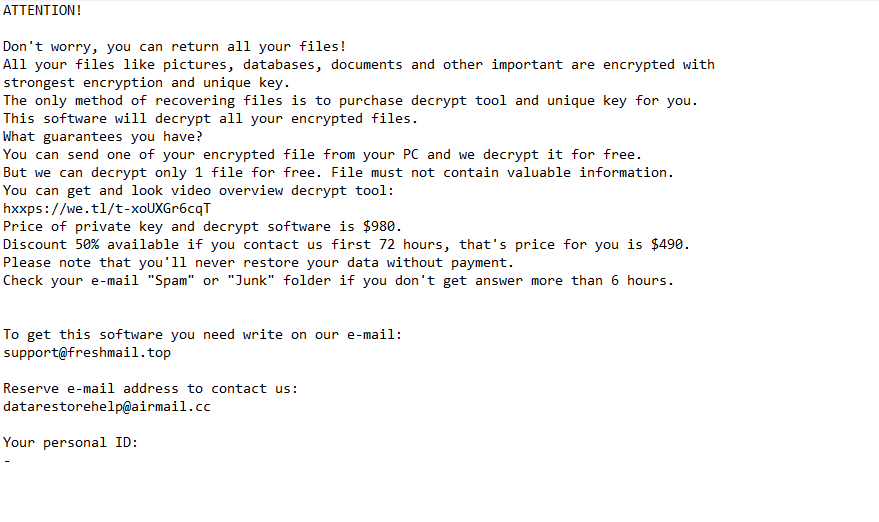
The _readme.txt ransom note is below:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-mFyI2phKff
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
–
Choosing to pay a ransom is typically discouraged. There’s no guarantee that you will receive a working decryption tool even if you comply with the demands, since you’re dealing with criminals who have no obligation to keep their promise. Additionally, paying the ransom only serves to support their continued malicious activities.
If you have backups of your data, restoring your files should be easy. However, it’s essential to first remove Jlaz ransomware from your system. If it remains active while you try to access your backups, it could encrypt the files in your backup as well. For this reason, using a reputable anti-malware program to remove Jlaz ransomware is recommended, as these infections can be quite challenging. Attempting to remove the ransomware manually may lead to further issues.
How is Jlaz ransomware distributed?
Cybercriminals use a variety of strategies to distribute ransomware, using methods such as torrents, email attachments, and deceptive links or ads. Users with poor online habits are particularly at risk for these types of infections, as they often engage in risky behaviors. To lower the chances of encountering malware, it’s important to develop safer online habits and become aware of common distribution tactics.
One common method for spreading malware is through email. These malicious emails are often made to appear like notifications about package deliveries or order confirmations, luring users to open the attachments by mentioning large sums of money or significant purchases. Fortunately, it is usually easy to identify these malicious emails, as they frequently contain glaring grammar and spelling mistakes that would not appear in legitimate emails. Another red flag is the use of generic words such as “User,” “Member,” or “Customer” to address recipients, while reputable companies typically personalize their correspondence using the customer’s name.
More sophisticated phishing emails can pose a greater challenge since they often include the recipient’s name and lack obvious spelling or grammatical mistakes, making them seem more credible. As a precaution, it’s a good idea to refrain from opening any unsolicited email attachments unless they have been scanned for malware through an antivirus program or VirusTotal.
Additionally, torrents serve as another common method for malware distribution. Torrent sites are often poorly moderated, allowing cybercriminals to upload malicious files disguised as torrents. Torrents for entertainment content—like movies, TV shows, or video games—often come bundled with malware. Regularly downloading copyrighted content from these sites not only risks legal issues but also places your computer and personal data in jeopardy.
How to remove Jlaz ransomware
Ransomware is a sophisticated form of malware, making it essential to use an anti-virus program to remove Jlaz ransomware. After you successfully delete Jlaz ransomware from your device, you can connect to your backup to start recovering your files. However, be cautious—if the ransomware is still present on your computer when you access your backup, it could result in the encryption of your backup files as well.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.