Remove Lkhy ransomware (.lkhy virus)
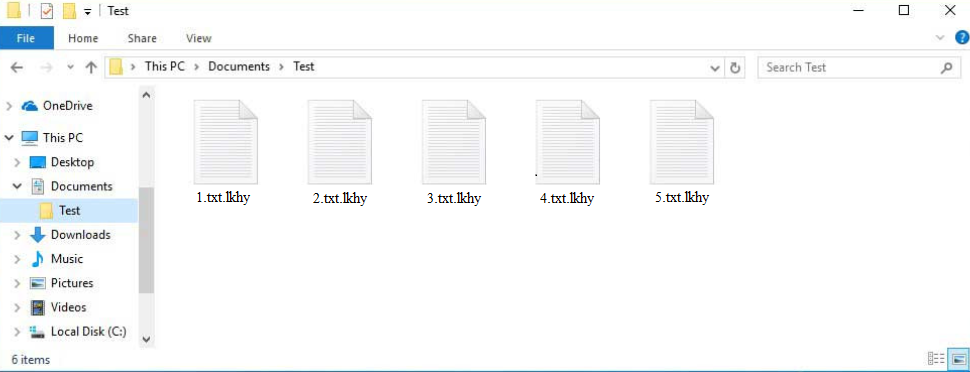
Lkhy ransomware is malware that encrypts files. It’s a dangerous infection that essentially takes files hostage and demands a payment for their recovery. The ransomware is part of the Djvu/STOP ransomware family. This version can be identified by the .lkhy extension added to encrypted files. Unfortunately, files with that extension will not be openable unless they are first put through a decryptor. Acquiring the decryptor is going to be difficult, as only the malicious actors behind this ransomware have it. They will demand that you pay $999 for it, though paying does not guarantee a working decryptor.
While this ransomware encrypts files, it shows a fake Windows update window. This ransomware adds the extension .lkhy to all files it encrypts. For instance, an encrypted file named text.txt would be renamed to text.txt.lkhy. Unfortunately, this affects a wide range of file types, including photos, videos, documents, and more. Once encrypted, these files cannot be opened unless you use a decryptor, which is difficult because only the cybercriminals behind the ransomware have it. They will attempt to sell it to you for $999, but paying the ransom is very risky for several reasons.
Once the encryption process is complete, the ransomware will create a _readme.txt ransom note in every folder containing encrypted files. This note is mostly the same as the one dropped by other versions of this ransomware family. It explains how to purchase the decryptor, emphasizing that it costs $999. However, it claims that those who reach out within the first 72 hours can get a 50% discount. Victims may also be allowed to decrypt one file for free, provided the file doesn’t contain any important information.
When dealing with cybercriminals, users need to be very cautious. Specifically, they should be skeptical of their promises, including the delivery of the decryptor. There have been past incidents where victims lost their money without receiving anything in return. But although we strongly discourage paying the ransom, the choice is ultimately yours. You simply need to be aware of the associated risks.
The full Lkhy ransomware note is below:
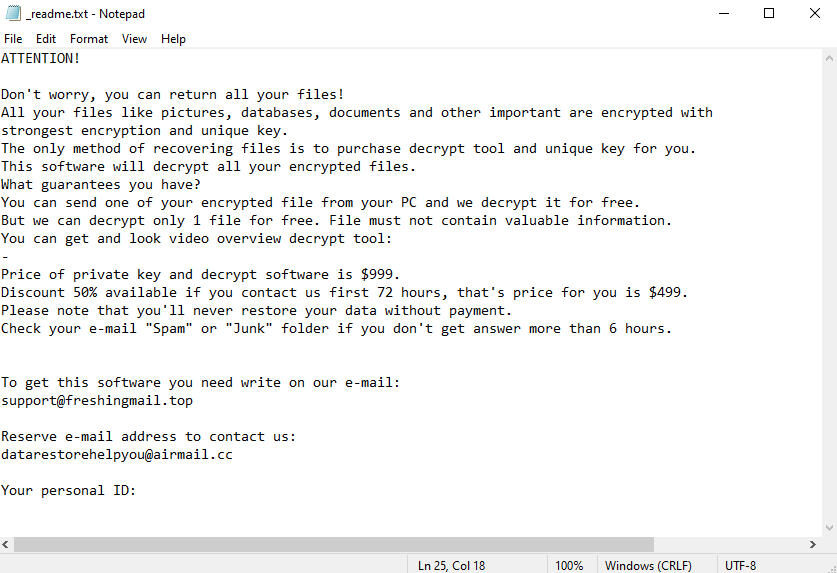
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
Do not ask assistants from youtube and recovery data sites for help in recovering your data.
They can use your free decryption quota and scam you.
Our contact is emails in this text document only.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-uNdL2KHHdy
Price of private key and decrypt software is $999.
Discount 50% available if you contact us first 72 hours, that’s price for you is $499.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshingmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
–
A good way to fight ransomware is to back up all important files. If you have backups, recovering your data will be significantly easier after a ransomware infection. However, it’s vital to completely remove Lkhy ransomware from your computer before you start file recovery. We recommend using anti-malware software to delete Lkhy ransomware, as attempting manual removal could lead to further issues. If the ransomware remains on your system when you access your backup, it could encrypt those files too, potentially causing irreversible loss.
If you don’t have backup copies of your encrypted files, your only remaining option may be to wait for a free Lkhy ransomware decryptor. However, there is no certainty that such a tool will be made available. Nonetheless, if you’ve exhausted your options, consider saving the encrypted files and periodically checking NoMoreRansom for a potential decryptor.
How is ransomware distributed?
It’s quite easy to acquire malware infections, which only highlights the importance of having good online habits. Users who are not cautious while browsing the internet are significantly more likely to pick up some kind of infection. Poor habits include opening unexpected email attachments, clicking on ads while visiting insecure sites, and illegally downloading copyrighted material through torrents. Having better online habits can help avoid a substantial amount of malware.
Torrents, in particular, are notorious for harboring malware. Many unregulated torrent sites are used by malicious actors to distribute various types of malware. It’s quite common to find infected torrents for popular movies, TV shows, software, video games, and more. For those unfamiliar with the signs of malware, it’s all too easy to become infected. Additionally, we should also mention that downloading copyrighted material for free via torrents is essentially stealing.
Another prevalent method for malware distribution is malicious spam. This is a low-effort method for cybercriminals, who only need to buy email addresses from hacker forums, compose somewhat convincing emails, attach a harmful file, and send them out. If users open the attachment, their devices can become infected immediately. Fortunately, identifying malicious emails is straightforward if users know what to look for. Common indicators include grammar and spelling mistakes; senders often impersonate legitimate companies, so these mistakes stand out. Other red flags include unfamiliar email addresses and generic greetings such as “Dear User/Member/Customer”. When users receive emails from companies they are familiar with, they will typically be addressed by their name, as anything else appears unprofessional.
In some cases, malicious emails can be more advanced, particularly if they are aimed at specific individuals. Therefore, it is advisable to always scan unsolicited email attachments with anti-virus software or tools like VirusTotal prior to opening them.
How to remove Lkhy ransomware
Ransomware poses a significant threat, and attempting to manually remove Lkhy ransomware is not a good idea. You risk causing further damage or failing to eliminate the infection completely. If the ransomware remains on your system when you access your backup, it could also encrypt those files. Therefore, we highly recommend using anti-malware software to effectively delete Lkhy ransomware. After you have successfully eliminated the ransomware, it’s safe to connect to your backup.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.