Remove Lomx ransomware (.lomx virus)
Lomx ransomware is a file-encrypting malware from the Djvu/STOP ransomware family. It’s a dangerous malware infection that encrypts files and demands a payment for a decryptor. The ransomware adds .lomx to all encrypted files, and you will not be able to open any of them unless you first use a decryptor on them. The malicious actors operating the Lomx ransomware are the only ones who have the decryptor, and they will demand a payment of $980 for it. Unfortunately, even paying for a decryptor does not guarantee that you’ll get it. Only users who have backups are guaranteed file recovery.
Lomx ransomware adds the .lomx extension to encrypted files, which is how you can recognize both the ransomware strain and which files have been affected. For example, an image.jpg file will be changed to image.jpg.lomx. Ransomware targets various personal files, including images, documents, videos, and more, all of which will have the .lomx extension. You won’t be able to open any of these files unless you use a specific decryptor on them.
During the encryption process, you might see a fake Windows update window designed to divert your attention from the fact that you’re files are being encrypted. Once the files are encrypted, a _readme.txt ransom note will appear in all folders that have encrypted files. This note is pretty generic and is used by various versions of this ransomware. It provides instructions on how to obtain the decryptor, which, unfortunately, requires a payment of $980. It also claims that those who contact the malicious actors within the first 72 hours can receive a 50% discount. However, it’s important to note that paying the ransom is generally not a good idea.
Ultimately, the choice to pay is yours, but it’s important to understand the potential risks that come with it. One major concern is that there’s no guarantee you’ll receive a decryptor even after payment. Since you’re dealing with cybercriminals, and they aren’t obligated to assist you, you may not be sent a decryptor.
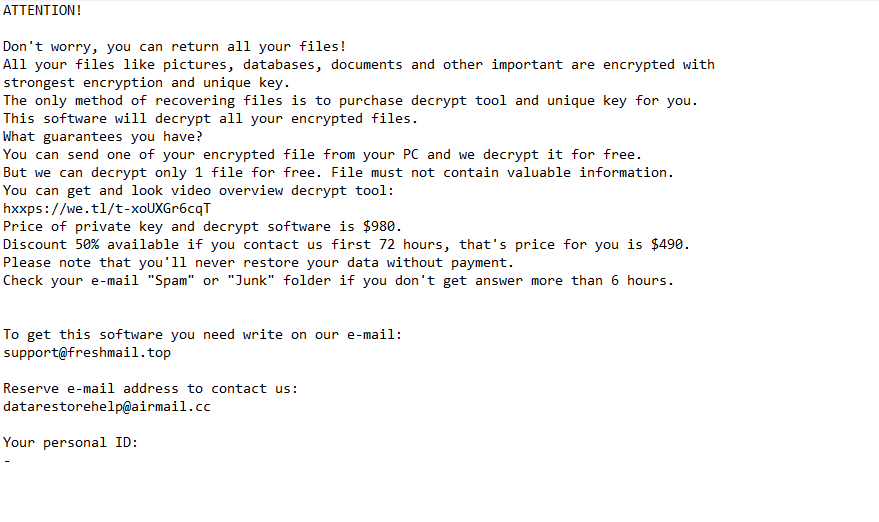
The full _readme.txt ransom note is below:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-MhbiRFXgXD
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelpyou@airmail.ccYour personal ID:
–
If you regularly back up your files, recovering them shouldn’t be difficult. However, before you connect to your backup, it’s crucial to first remove Lomx ransomware from your computer to prevent it from encrypting your backup files as well. To successfully remove Lomx ransomware, using anti-malware software is highly recommended.
For users without a backup, recovering files might be very difficult, if not impossible, right now. However, while there isn’t a decryptor available at the moment, it’s possible that a free Lomx ransomware decryptor could be released in the future. Keep an eye on reputable sources like NoMoreRansom for any updates regarding a decryptor.
How does ransomware infect computers?
Users with poor browsing habits are more likely to encounter malware, primarily because they often open unsolicited email attachments, download pirated content via torrents, and click on ads while visiting high-risk websites. By improving their online habits, users can significantly reduce their chances of encountering malware.
Spam emails are one of the leading ways users unwittingly acquire infections like ransomware. Simply opening an attachment can trigger malware. Malicious emails are generally easy to spot unless they are tailored to someone whose personal information cybercriminals have obtained. Typically, generic malicious emails are riddled with grammar and spelling mistakes. The senders usually claim to be from companies/organizations whose services users use, such as a delivery service, government agency, or tax office. When these emails contain noticeable mistakes, it becomes clear they are not legitimate. Another red flag is the use of generic words like “User,” “Customer,” or “Member” when addressing recipients, instead of their names. Reputable companies usually address users by name in their correspondence to maintain professionalism. Even if an email appears completely legitimate, it is recommended to scan any unsolicited attachments with anti-virus software or VirusTotal.
Users who use torrents to download copyrighted content are also at a heightened risk of infection. Torrent sites are notorious for their lack of moderation, which allows cybercriminals to upload malicious torrents of popular movies, TV shows, games, and software. This is particularly prevalent for newly released films and series; for instance, when a new Marvel movie is released, it is almost guaranteed that many of its torrents will have malware.
How to remove Lomx ransomware
It’s not recommended to attempt to manually remove Lomx ransomware, as this could lead to further complications. You might also risk leaving parts of the ransomware behind, which could enable it to recover later. Additionally, if you connect to your backup while the ransomware is still active, your backed-up files could become encrypted too. Using anti-virus software is a safer and more effective way. Once the ransomware has been completely eliminated, you can safely connect to your backup and begin recovering your files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.