Remove Mzre ransomware (.mzre virus)
Mzre ransomware is a file-encrypting malware that takes files hostage and demands a payment for a decryptor. It comes from the Djvu/STOP malware family, and can be differentiated from its other versions by the .mzre extension added to encrypted files. The ransomware targets personal files, so you can expect all your photos, documents, etc., to have the .mzre extension added to them. You will not be able to open any files with that extension unless you first use a decryptor on them. However, getting the decryptor is not going to be easy because only the malicious actors behind this ransomware have it. They will try to sell you the decryptor, but even paying for it does not guarantee you’ll be able to get your files back.
File encryption begins immediately after the ransomware is initiated. The main targets are the personal files that users are likely to want to pay for, such as documents, photos, videos, and images. Encrypted files become identifiable by the new extensions added to their names. This specific type of ransomware uses the extension .mzre, meaning a file like text.txt would change to text.txt.mzre once it’s encrypted.
Once it’s done with file encryption, the ransomware drops a _readme.txt file, which acts as a ransom note. This note informs users that their files have been encrypted and can only be restored by paying a ransom. The demanded amount is $980, but the note mentions a 50% discount for users who make contact within the first 72 hours of infection. Users can also supposedly decrypt one file for free if it does not contain any important information.
The ransom note dropped by Mzre ransomware is below:
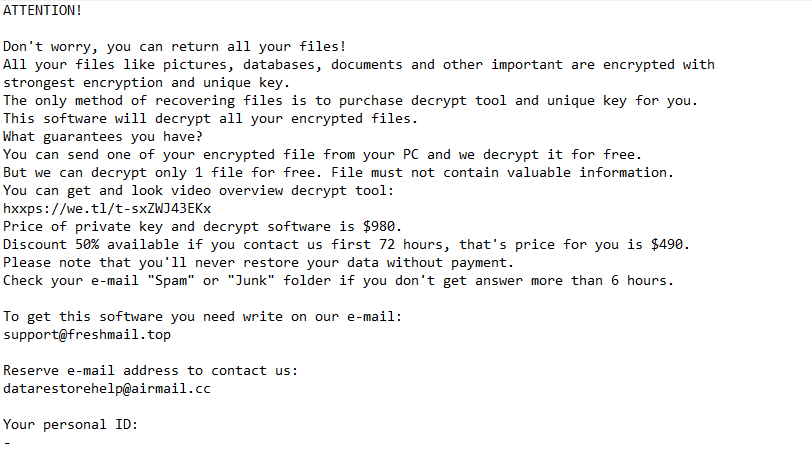
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-sxZWJ43EKx
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
–
While paying the ransom in this situation may seem like a good idea, it’s important to emphasize that doing so is not recommended. Victims must understand that they are dealing with cybercriminals who are under no obligation to help after they receive payment. There’s no assurance that victims will receive a decryption key after paying the ransom. Sadly, many users have previously paid ransoms only to be left with ineffective decryption tools or no assistance whatsoever.
For those with backups, the recovery process can begin immediately after they remove Mzre ransomware from their systems. It’s strongly recommended to use an anti-malware program since this is a complex infection. Once you fully delete Mzre ransomware, it’s safe to connect to the backup. For users who do not have backups, the only course of action is to back up the encrypted files and wait for a free Mzre ransomware decryptor to be made available. However, such a decryptor is not guaranteed.
How does ransomware infect computers?
Malicious actors use a variety of tactics to spread ransomware, such as using torrents, sending email attachments, and sharing harmful links or advertisements. Users with poor online habits are at a higher risk of infecting their computers. To minimize the chances of malware infections, it is strongly recommended to develop better browsing habits and become familiar with common methods of malware distribution.
Email attachments are a common method for malware delivery. Often disguised as notifications for parcel deliveries or order confirmations, these emails create a sense of urgency and pressure users by mentioning large amounts of money or expensive purchases, prompting users to open attachments without thinking twice. However, many malicious emails can be identified as long as users take the time to inspect all unsolicited emails. Users should look out for obvious spelling and grammar mistakes– something many malicious emails have, for whatever reason. Additionally, these emails often address recipients with generic words like “User,” “Member,” or “Customer,” whereas most companies personalize their correspondence by using the recipient’s name. Malicious actors usually lack access to personal information, which is why they use generic words when addressing users.
When emails are tailored to target specific people or companies, they tend to be more sophisticated. These targeted emails are often free of the typical signs of maliciousness, personally address the recipient, and include credible details that enhance their legitimacy. Therefore, it’s always best to refrain from opening unsolicited email attachments unless they have been scanned with anti-virus software or checked on VirusTotal.
Torrents also serve as a popular means for distributing malware. Many torrent sites have insufficient moderation, allowing malicious actors to upload infected files. Torrents for entertainment content such as movies, TV shows, and video games are particularly prone to harboring malware. Thus, by pirating copyrighted content, users not only commit theft but also put their computers and data at significant risk.
How to remove Mzre ransomware
Ransomware is a complex form of malware that requires removal with a professional program. Trying to manually delete Mzre ransomware could potentially harm your device even more. It’s strongly recommended to use an anti-virus program for this. Once the ransomware has been fully removed and is no longer detected, you can safely connect to your backup and begin restoring your files. However, proceed with caution: if the ransomware is still active when you access your backup, there’s a big risk that any backed-up files might also get encrypted.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.