Remove Ptrz ransomware (.ptrz virus)
Ptrz ransomware is a file-encrypting malware from the Djvu/STOP ransomware family. This ransomware can be identified by the .ptrz extension added to encrypted files. The malware takes all personal files hostage by encrypting them, and users cannot open them unless they are first decrypted using a specialized decryptor that only the ransomware operators have. They will try to sell it to victims for $980, but buying it is not a good idea, as it does not guarantee that a decryptor will be sent. At the moment, only users who have backups are guaranteed file recovery as long as they remove Ptrz ransomware before connecting to their backups.
The Djvu/STOP ransomware family is operated by a prominent ransomware group that regularly releases new versions. The version can be differentiated by the extensions they add to encrypted files. In this case, Ptrz ransomware adds .ptrz. For example, an encrypted text.txt file would become text.txt.ptrz. Once this ransomware infiltrates a computer, it begins encrypting files, primarily targeting personal data like photos, videos, and documents. As these files become encrypted, they cannot be opened unless a decryption program is used. Unfortunately, only the malicious actors behind the ransomware have the decryption tool, and they are unlikely to provide it, whether you pay the ransom or not.
According to the _readme.txt ransom note that is dropped after the files are encrypted, a payment of $980 (or $490 if you reach out within the first 72 hours) is required to obtain the decryptor. However, paying the ransom does not guarantee that you will receive the decryptor; many victims who have paid have ended up receiving nothing in return. While the decision to pay is ultimately yours, it’s important to understand the risks involved with dealing with cybercriminals. Paying the ransom may also encourage further criminal activities in the future. As long as victims continue to comply, ransomware will remain a serious issue.
The full _readme.txt ransom note is below:
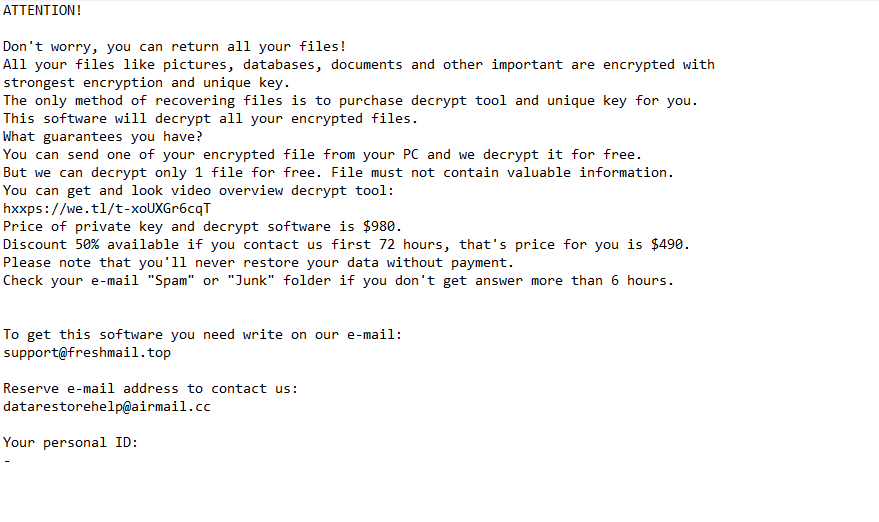
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-dHFDYXqlkk
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
–
For users with backups of their files, recovery is very likely with no issues. However, it’s crucial not to access your backup until you fully remove Ptrz ransomware from your system, as this could lead to the backup files also being encrypted. For those without backups, the only option may be to wait for the release of a free decryption tool. NoMoreRansom is a good source for decryptors. We should also stress how important it is to use an anti-malware program to remove Ptrz ransomware, as it’s a complex infection that requires a professional program to get rid of.
Ransomware distribution methods
Users who have poor online habits are at a higher risk of encountering a malware infection. If you open unsolicited email attachments without verifying their safety, interact with ads on high-risk websites, and download pirated content through torrents, you have poor browsing habits. Developing better ones can significantly reduce the likelihood of a malware infection.
A very common method of acquiring malware is through malicious spam (malspam) attachments. Cybercriminals often launch spam email campaigns using addresses obtained from hacking forums. If your email address has previously been leaked, there’s a strong chance you’ll encounter malspam in your inbox. Never open unknown email attachments without scanning them with an anti-malware program or VirusTotal. Look out for grammar/spelling mistakes in emails that claim to be from legitimate companies, and always check the sender’s email address to make sure it belongs to whomever the sender claims to be. Finally, be skeptical of emails that address you as User, Member, Customer, etc., especially when the sender should know your name.
We advise against using torrent sites and engaging in piracy. Torrent sites are notorious for having a lot of malware, as they are poorly regulated. This allows malicious users to distribute torrents embedded with malware, often disguised as popular movies or TV shows. Be cautious with software cracks as well; they frequently contain malware, so it’s wise to reconsider stealing paid programs.
How to remove Ptrz ransomware
Ransomware, unlike adware or browser hijackers, is a very complex malware infection. Therefore, attempting to manually delete Ptrz ransomware is not a good idea; instead, it’s best to use anti-virus software. The anti-virus program will remove Ptrz ransomware and any related files, allowing you to access your backup for file recovery. However, it’s important to understand that simply removing the ransomware does not automatically decrypt your files. You will require a decryptor for that purpose, and unfortunately, there isn’t a free Ptrz ransomware decryptor available at the moment.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.