Remove P*zdec ransomware (.p*zdec virus)
P*zdec ransomware, or .p*zdec virus, is a file-encrypting malware from the GlobeImposter ransomware family. This is a serious malware infection because it encrypts files and essentially takes them hostage. This ransomware can be identified by the .p*zdec extension added to encrypted files. Unfortunately, all files users hold host important will have this extension, as they’re the ones users are usually most willing to pay for. The ransomware operators will demand a payment for a decryptor, but the amount is not clear, as two very different sums are mentioned in the ransom note. At the moment, it’s only possible to recover files for free via backup.
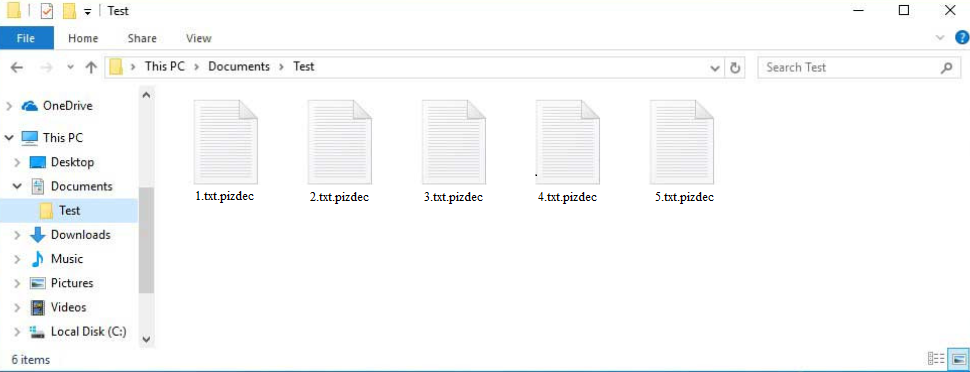
Once it’s initiated, P*zdec ransomware targets all files that may be important, particularly documents. Once encrypted, the files will have the .p*zdec extension added to them. For example, 1.txt file would become 1.txt.p*zdec. None of the files that have this extension will be openable unless you first use a decryptor on them. However, acquiring it is not going to be easy.
The how_to_back_files.html ransom note dropped by the ransomware explains how users can recover their files, which involves paying a ransom. The note mentions two very different sums, which is quite confusing as it’s unclear which one is right. It first says that users would need to pay 0.5 BTC, which is around $47,000 at the time of writing. Further down, it says users need to send $1,000 in BTC to the provided wallet address. The solodinero@seznam.cz email address is provided for users who want to make contact with the cybercriminals.
The full P*zdec ransomware ransom note is below:
YOUR PERSONAL ID
–ENGLISH
YOUR CORPORATE NETWORK LOCKED!
ALL YOUR IMPORTANT DATA HAS BEEN ENCRYPTED.TO RESTORE FILES YOU WILL NEED A DECRYPTOR!
To get the decryptor you should:
Pay for decrypt your network – 0.5 BTC
Buy BTC on one of these sites
hxxps://binance.com
hxxps://www.coinbase.com
Any site you trustBitcoin Wallet: 3FmLKtBZB435pwa8BTknPKXsUeYkRu4u82
Send $1000 usd in BTC for decrypt
Our contacts:
email: solodinero@seznam.cz
ToxID: 9CDB535E2DFE3DFAFF17A2263A03A684 B816FC9E69F159301D25E56C8EB47C32468D0F8129BD
You can download TOXChat here : hxxps://tox.chat/download.html
The message must contain your Personal ID! it is at top of this document.
Never pay to any other addresse BTC than those listed here! We do not use any other messengers except TOX and the contact listed here! Remember! Turning to an intermediary – you risk losing your money, always ask for help yourself using the contacts indicated in this document.
—————————————–
© 2025 Suffering Corporation | All Rights Reserved.
Whether the decryptor’s price is $1,000 or $47,000, buying anything from cybercriminals is never recommended. Users should always keep in mind that they are dealing with malicious actors who feel no obligation to help victims recover their files. What’s more, the reason the ransomware business is able to thrive is that victims pay the ransom. That money also goes towards future criminal activities.
At the moment, only users who have backups can recover their files for free. It’s very important that users first remove P*zdec ransomware from their computers before connecting to their backups. If the ransomware is still present, the backed-up files would become encrypted as well. And because ransomware is a complex infection, using an anti-malware program is a must.
How is ransomware distributed?
One way that malware gets onto users’ computers is through email attachments. Cybercriminals use this method because it requires little effort on their part; they can purchase email addresses in bulk from hacker forums and launch widespread malicious spam campaigns. Thankfully, these campaigns often target random users, making the emails generic and relatively easy to identify. Such emails are typically sent from suspicious addresses, contain numerous grammar and spelling mistakes, are awkwardly phrased, and address the recipient using generic words, all while claiming to be from a known company whose services the user supposedly uses. If a legitimate company whose services you use sends you an email, it would be mistake-free and would address you by name. Malicious actors, however, use generic words like “Member”, “Customer”, or “User” because they do not have access to more specific personal information. Being aware of these warning signs can help you easily identify most generic malicious spam attempts.
In addition to knowing how to recognize malicious emails, we recommend scanning all unsolicited email attachments using anti-virus software or checking them with services like VirusTotal for potential malware. This simple step could prevent significant issues later on.
We should also mention that cybercriminals frequently use torrents to distribute malware. Torrent sites often have very poor moderation, allowing the upload of torrents for popular movies, TV shows, video games, software, and more, containing hidden malware. Torrents for newly released popular content are particularly susceptible to this. Consequently, downloading pirated content not only constitutes theft but also puts your computer and personal data in jeopardy.
How to remove P*zdec ransomware
Ransomware infections are usually very sophisticated and require a professional anti-malware program to remove. Thus, do not try to remove P*zdec ransomware manually as you could end up causing additional damage to your device. Once you delete .p*zdec virus, it’s safe to connect to the backup to start recovering files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.