Remove StarFire (.Celestial) ransomware
StarFire ransomware is a file-encrypting malware. The ransomware takes users’ files hostage by encrypting them and demands payment for a decryptor to recover them. The malware can be identified by the .Celestial extension added to encrypted files. If your files have that extension, you will not be able to open them until you put them through a decryptor. However, the only ones who have the decryptor at the moment are the cybercriminals operating this ransomware. They will ask that you pay $3,000 in Bitcoin to the provided wallet. However, paying does not guarantee a decryptor. At the moment, only users who have backups can recover their files for free.
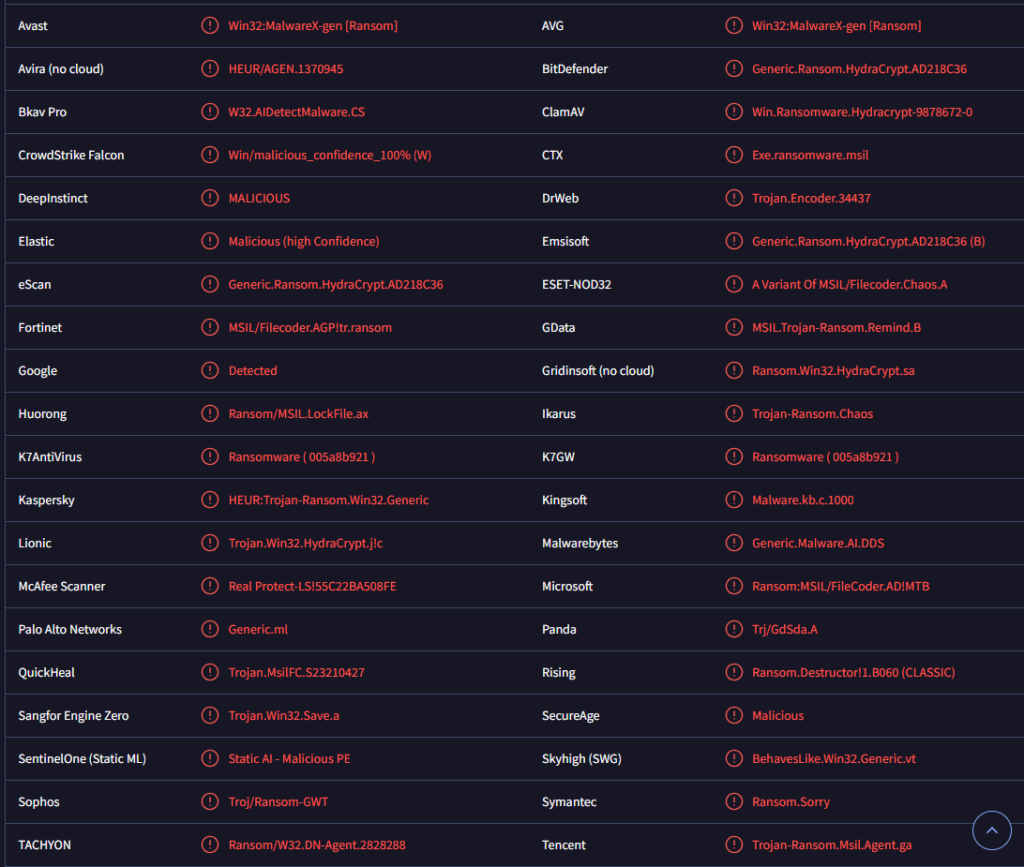
You can determine which ransomware has infected your computer by looking at the extension attached to the encrypted files. This specific ransomware appends .Celestial to file names. For instance, an image.jpg file would turn into image.jpg.Celestial. It affects all personal files, including photos, videos, and documents, rendering them unopenable unless first put through a decryptor. Unfortunately, the only individuals who possess a functioning decryptor are the cybercriminals responsible for this ransomware, and they won’t simply provide it for free. Instead, they will demand a payment of $3,000 for it.
After completing the encryption process, StarFire (.Celestial) ransomware will drop a StarFire-README.txt ransom note. This note explains how to decrypt your files and informs you that a decryptor is available for purchase as long as you’re willing to pay $3,000. While the decision to pay is yours, it’s important to understand the risks involved. One of the primary reasons against paying the ransom is that doing so does not guarantee that you will receive a decryptor. Remember, you are dealing with criminals, and there’s no assurance they will fulfill their end of the bargain, even if you pay up. Many ransomware victims in the past have paid only to receive nothing in return.
The full ransom note is below:
*****StarFire Ransomware*****
Hello User. Your computer has been attacked and infected by the StarFire Ransomware. All of the files on your computer have been encrypted with AES and RSA encryption algorithms and are now completely unaccessable. Do not go to any professionals or authorites as they will not help you. The only way to restore your files is with our special decryption software that is hosted on our server. In order to get this decryption software. You must first download the TOR browser at hxxps://torproject.org/ and access one of the three darknet sites listed below. You must then transfer $3000 USD worth of bitcoin to the address listed on the site. Then, simply send us an email to the address that you got our ransomware from. We will then verify your payment and send you the decryption software to decrypt your files. Refusal to pay the ransom will result in the decryption software being deleted after 72 hours and your files will be lost forever.
Our Sites:
–
Your personal ID: –
May The Stars Guide You
Kind Regards
The StarFire Group.
Currently, the only completely free method to recover your files is through a backup. If you don’t have a backup available, your best bet is to wait for a free decryptor to be released, but unfortunately, there isn’t one available at this time. If a decryptor does become available, it will be found on NoMoreRansom.
For those with a backup, recovering files shouldn’t be a problem. Users have to first remove StarFire (.Celestial) ransomware from their systems using anti-virus software before accessing their backup. It’s crucial to make sure that the ransomware is completely removed before connecting to the backup; otherwise, the files in the backup could also become encrypted.
How is ransomware distributed?
A common method for malware to infiltrate users’ computers is through email attachments. For cybercriminals, this method requires minimal effort, as they only need to buy email addresses in bulk from hacker forums and use them to launch large-scale spam campaigns. Fortunately, since these campaigns target users at random, they tend to be generic and quite easy to identify. Such emails usually come from suspicious email addresses, have numerous grammar and spelling mistakes, are written in quite awkward language, and address recipients with vague terms, all while claiming to be affiliated with a company that the user might recognize and whose services they use. If a legitimate company of which you are a customer were to send you an email, its email would be free of mistakes and would greet you by name. Malicious actors are forced to use generic words like “Member,” “Customer,” or “User” to address users, as they do not have access to more personal information. Recognizing these signs can help you spot most generic spam attempts.
As a precaution, it’s always a good idea to scan all unsolicited email attachments with anti-virus software or use services like VirusTotal to check for malware. This could save you a lot of trouble down the road.
Additionally, cybercriminals often use torrents to spread malware. Torrent sites are often poorly moderated, making it easy to upload torrents for popular movies, TV shows, video games, software, and more with malware in them. It’s especially common to find malware in torrents of newly released content. Therefore, by downloading pirated content, you not only engage in theft but also risk compromising your computer and data.
StarFire (.Celestial) ransomware removal
Ransomware is a very serious malware infection. Therefore, it’s very important not to try to manually remove StarFire (.Celestial) ransomware, as doing so could lead to further issues with your computer. You might also inadvertently miss some components of the StarFire (.Celestial) ransomware, allowing it to recover later. And if you connect to your backup while the ransomware is still active, it could result in your backup files also becoming encrypted. It’s best to rely on trusted anti-virus software to delete StarFire (.Celestial) ransomware from your system before attempting to access your backup.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.