Remove Ttza ransomware (.ttza virus)
Ttza ransomware is a file-encrypting malware from the Djvu/STOP ransomware family. It encrypts files and demands a payment for their recovery. The ransomware can be identified by the .ttza extension it adds to encrypted files. Once encrypted, the files will remain unopenable unless you first use a decryptor on them. The malicious actors operating this ransomware will offer the decryptor for a price, but engaging with cybercriminals is not a good idea. At the moment, only users who have backups can recover their files for certain.
Ttza ransomware is operated by a cybercriminal group that has produced hundreds of ransomware versions and continues to release new ones regularly. While the latest versions are largely similar, they can be identified by the unique extensions they append to encrypted files. In this case, the ransomware targets your personal files, adding a .ttza extension to them. It focuses on files that users are most likely to pay to recover, such as photos, videos, images, and documents. Without a decryptor, you will be unable to access these files, and unfortunately, the decryptor can only be obtained from the cybercriminals behind the attack.
Once you open the malicious file, the ransomware begins the encryption process and will simultaneously display a fake Windows update window. Upon completion, it drops a _readme.txt ransom note, which explains what has happened and provides instructions for purchasing the decryption tool. The price for the decryptor is typically $980 (with more recent versions demanding $1,999), but they promise a 50% discount for those who contact them within the first 72 hours. Whether this discount is legitimate is uncertain, and before deciding to pay, it’s important to recognize the associated risks. Paying does not guarantee that you will receive the decryptor; many victims have paid the ransom without receiving any means of recovery.
The full Ttza ransomware ransom note is below:
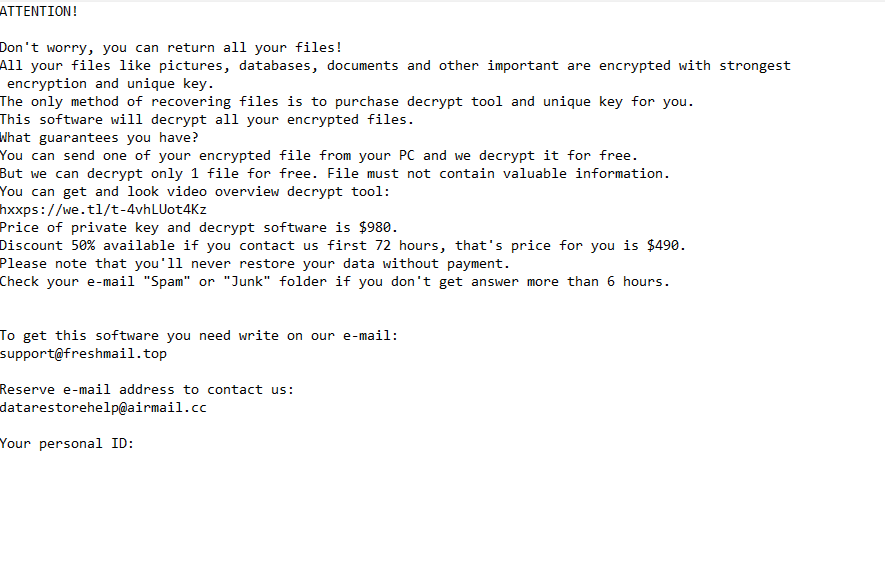
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-4vhLUot4Kz
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
support@freshmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
–
For users with a backup, file recovery should be straightforward. If you regularly backed up your files before the encryption happened, you can restore your files after you remove Ttza ransomware from your device. It’s worth stressing that you need to be very careful. Make sure the ransomware is fully eliminated first, as connecting your backup while the ransomware is still present will lead to those files being encrypted too. Use anti-virus software to safely remove Ttza ransomware rather than attempting to do it manually.
For those without a backup, recovering files will be more challenging. Currently, there is no free Ttza ransomware decryptor available.
How is ransomware distributed?
One of the most prevalent methods that cybercriminals use to spread ransomware is through email spam campaigns. They often buy hundreds of email addresses from hacker forums to launch these campaigns. Fortunately, many of these malicious emails are relatively easy to spot if users know what to watch out for.
A clear indicator of a malicious email is the presence of grammar and spelling mistakes. Malicious senders frequently impersonate well-known companies that users interact with, so the mistakes are very noticeable. Legitimate emails from trustworthy sources typically have no mistakes, especially automatic ones, as mistakes look unprofessional. Therefore, if you receive an email from a postal service, for example, and it contains multiple mistakes, it’s a good idea to be cautious.
Another telltale sign is how the email addresses you. If you’re referred to as “User,” “Member,” or “Customer” by someone who should know your name, it’s likely a malicious email. Legitimate companies generally address you by your name. While less common, some malicious campaigns can be more sophisticated, specifically when they target certain high-profile users or companies. Thus, it’s always advisable to scan any unsolicited email attachments using anti-virus software or tools like VirusTotal.
Additionally, torrent users who pirate content face a higher risk of malware infections. Many torrent sites lack proper regulation, allowing cybercriminals to upload harmful content disguised as torrents for movies, TV shows, video games, or software. So, if you engage in torrenting pirated content, you’re not only committing theft but also putting your computer and data at significant risk.
Ttza ransomware removal
It’s best to use anti-malware software to remove Ttza ransomware. Attempting to manually delete Ttza ransomware could lead to additional harm to your computer or leave the infection partially intact. If that happens and you connect to your backup, backed-up files might also get encrypted. To prevent further issues, it’s advisable to use anti-malware software.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.