Remove “Virus Intrusion Into Our Office 365 Webmail Server” scam email
The “Virus Intrusion Into Our Office 365 Webmail Server” email is part of a phishing campaign that tries to steal users’ email login credentials. The email is disguised as a notification from the users’ email service provider and informs the recipients that, because of a virus intrusion in their Office 365 webmail server, they need to do a full server sweep. The email includes a button, which will redirect users to a phishing page that asks for email login credentials.
The “Virus Intrusion Into Our Office 365 Webmail Server” email is a generic phishing email, sent to steal users’ email login credentials. The email claims that a virus intrusion has been detected in the Office 365 webmail server, and it’s necessary to perform a full server sweep to supposedly identify and eliminate the virus. The email asks that users click the provided button to initiate the sweep. The contents of the email are completely false, and clicking on the provided button will lead users to a phishing site.
The full “Virus Intrusion Into Our Office 365 Webmail Server” email text is below:
Subject: Price Items- DRAFT PO ORDER( www.pmi-amt.com.tw ) Contempo Industrial Technology Taiwan Co., Ltd. – MBL# New Order20240807SO# 420, 421 / VSL: YM WIDTH V.023E / 2 X 40’HQ / OVERSEAS BUSINESS DEPARTMENT to Norfolk + 4 X 40HQ + CRD:: 5/25
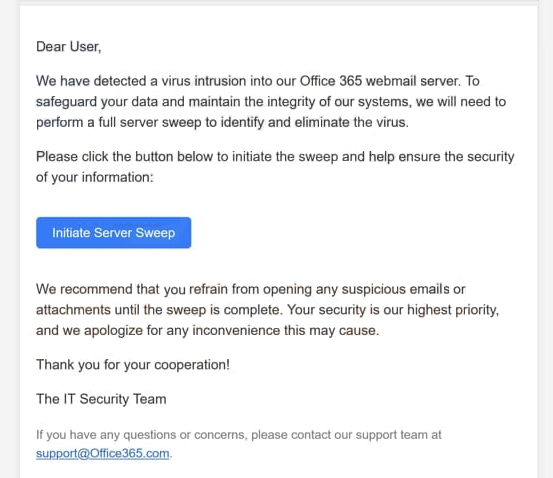
Dear User,
We have detected a virus intrusion into our Office 365 webmail server. To safeguard your data and maintain the integrity of our systems, we will need to perform a full server sweep to identify and eliminate the virus.
Please click the button below to initiate the sweep and help ensure the security of your information:
Initiate Server SweepWe recommend that you refrain from opening any suspicious emails or attachments until the sweep is complete. Your security is our highest priority, and we apologize for any inconvenience this may cause.
Thank you for your cooperation!
The IT Security Team
Threat actors commonly deliver malware by attaching malicious files to their emails. These files might look like regular documents, compressed folders, or programs, but opening them (or taking additional steps, like enabling macros in documents) often leads to malware execution.These emails may also direct users to fake or unsafe websites that prompt them to download harmful software. Sometimes, the malware begins downloading automatically when the site is accessed, even without the user clicking anything.
If you have any questions or concerns, please contact our support team at support@Office365.com.© 2023 Company Name. All rights reserved.
If users click on the “Initiate Server Sweep” button provided in the email, they will be taken to a website that displays a blurry document in the background. A pop-up will appear, saying the document is protected from unauthorized access, and to view it, users need to sign in with their correct credentials. If users enter their passwords, that information gets sent directly to the malicious actors operating the phishing campaign. Cybercriminals may either use stolen login credentials for their own purposes or sell them to other malicious actors on hacker forums. Email login details are especially sought after because email accounts hold a wealth of sensitive information and are typically connected to numerous other accounts. By compromising an email account, these cybercriminals can gain access to various linked accounts as well.
How do you recognize phishing emails?
Identifying generic phishing campaigns that target many users with the same email is relatively straightforward. The “Virus Intrusion Into Our Office 365 Webmail Server” email is a great example as it’s very low-effort, has many mistakes, and looks very unprofessional. The very first line gives away the phishing attempt as the email greets the recipient as “User”. That is an immediate giveaway because an email provider always addresses its users by their names (specifically the names used when creating the account). On the other hand, phishing attempts directed at specific individuals tend to be more sophisticated and can be trickier to identify as malicious. Fortunately, most users encounter more generic phishing emails since they are not considered high-profile targets.
If you receive an unsolicited email that prompts you to click on a link or open an attachment, your first step should be to verify the sender’s email address. While some malicious email addresses may look suspicious, scammers often employ tactics to mask them and make them appear legitimate. For instance, they might alter letters or include extra characters. They may even spoof an email address to make it seem like the email was sent from the user’s own account, as is the case with this “Virus Intrusion Into Our Office 365 Webmail Server” email.
One clear sign of a phishing attempt is the presence of grammar and spelling mistakes. The “Virus Intrusion Into Our Office 365 Webmail Server” email has several grammar mistakes and generally looks very unprofessional. You will never see mistakes in professional emails from companies.
Remove “Virus Intrusion Into Our Office 365 Webmail Server” phishing email
This “Virus Intrusion Into Our Office 365 Webmail Server” email is phishing, so you should remove it if it lands in your inbox. If you’ve already opened the email and entered your login details, change your password right away if you still have access to your account. It’s also a good idea to review your account activity for any signs of unusual behavior. If you find yourself locked out of your email, try all account recovery options. In case you can’t recover your account, make sure to remove your email address from other accounts to prevent them from being compromised as well.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.