Remove “We Have Your Search Requests And Webcam Footage” email
The “We Have Your Search Requests And Webcam Footage” email is part of a sextortion scam email campaign that tries to blackmail recipients into paying $1,350. The email claims that recipients have been spied on via malware on their computers, which allowed the sender to steal search queries and make videos of recipients watching pornography. These scammers threaten to send the stolen information, as well as the videos, to all contacts unless recipients agree to pay $1,350. The entire thing is a scam, and there is no need to pay anything. There are no videos, nor have users been spied on.
Sextortion scam emails are very common, and most users whose email addresses have been leaked will receive one eventually. While they may be operated by different cybercriminal groups, they are all more or less identical to one another. They all follow the same pattern of first trying to catch users’ attention with alarming subject lines, then scare users with threatening walls of text. The emails always claim that users’ computers have been infected with malware that allows its operators to spy on users, steal data, as well as turn on the webcam/microphone.
This particular “We Have Your Search Requests And Webcam Footage” email has a very alarming subject line, which is bound to catch users’ attention. After all, an email with the subject of “Read this email or something terrible will happen” sounds scary. If users open the email, they will see a long piece of text saying the sender works for Russian hacker groups like Cozy Bear and Killnet. Supposedly, the sender claims to be on the lookout for suspicious online accounts, which is how they came across the recipient’s account. The sender claims to have noticed the recipient’s questionable sexual preferences, stole their search queries, and made a video via the webcam of them watching pornography. The sender threatens to send the stolen search queries and the video to all contacts unless the recipient agrees to pay $1,350 in Bitcoin.
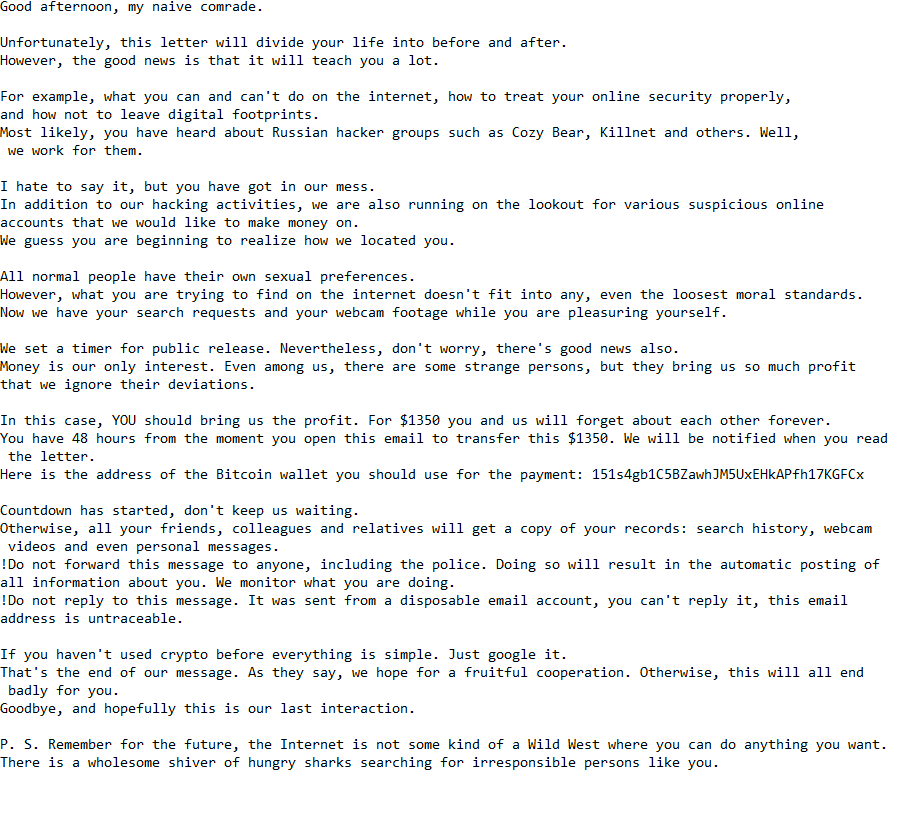
The full “We Have Your Search Requests And Webcam Footage” email is below:
Subject: Read this email or something terrible will happen.
Good afternoon, my naive comrade.
Unfortunately, this letter will divide your life into before and after.
However, the good news is that it will teach you a lot.For example, what you can and can’t do on the internet, how to treat your online security properly, and how not to leave digital footprints.
Most likely, you have heard about Russian hacker groups such as Cozy Bear, Killnet and others. Well, we work for them.I hate to say it, but you have got in our mess.
In addition to our hacking activities, we are also running on the lookout for various suspicious online accounts that we would like to make money on.
We guess you are beginning to realize how we located you.All normal people have their own sexual preferences.
However, what you are trying to find on the internet doesn’t fit into any, even the loosest moral standards.
Now we have your search requests and your webcam footage while you are pleasuring yourself.We set a timer for public release. Nevertheless, don’t worry, there’s good news also.
Money is our only interest. Even among us, there are some strange persons, but they bring us so much profit that we ignore their deviations.In this case, YOU should bring us the profit. For $1350 you and us will forget about each other forever.
You have 48 hours from the moment you open this email to transfer this $1350. We will be notified when you read the letter.
Here is the address of the Bitcoin wallet you should use for the payment: 151s4gb1C5BZawhJM5UxEHkAPfh17KGFCxCountdown has started, don’t keep us waiting.
Otherwise, all your friends, colleagues and relatives will get a copy of your records: search history, webcam videos and even personal messages.
!Do not forward this message to anyone, including the police. Doing so will result in the automatic posting of all information about you. We monitor what you are doing.
!Do not reply to this message. It was sent from a disposable email account, you can’t reply it, this email address is untraceable.If you haven’t used crypto before everything is simple. Just google it.
That’s the end of our message. As they say, we hope for a fruitful cooperation. Otherwise, this will all end badly for you.
Goodbye, and hopefully this is our last interaction.P. S. Remember for the future, the Internet is not some kind of a Wild West where you can do anything you want.
There is a wholesome shiver of hungry sharks searching for irresponsible persons like you.
Considering the email is nothing more than a scam, sending any amount of crypto to the provided wallet address would be a complete waste of money. Recipient’s computers are not infected with malware, nor are there videos of them watching pornography. The email can be safely ignored and deleted.
How do scammers obtain users’ email addresses?
Sextortion scam campaigns typically target users whose email addresses have been leaked or exposed in a data breach. Unfortunately, email addresses are one of the most frequently leaked data. These leaked addresses are often sold on hacking forums for the purpose of distributing scams and malware. Therefore, if you receive a sextortion email, it’s likely due to the exposure of your email address, not because your device is infected with something. Haveibeenpwned is a useful tool to check which data breaches your email address may have been involved in. While there’s not much you can do to prevent such leaks, knowing that your email address has been leaked can help you be careful when dealing with unsolicited emails, especially those featuring file attachments or links.
It’s also important to note that some sextortion emails may include your phone numbers and passwords. In many cases, this information is correct, which makes these scams more convincing. However, there’s a straightforward explanation for how such details end up in sextortion emails—no hacking is involved. Just as email addresses can be leaked, so can passwords and phone numbers. If your password or phone number appears in a sextortion email, it simply means that this information has been exposed by some service you use. If the leaked password is one that you still use, you should change it immediately. Always avoid reusing passwords; if one account is compromised, it could allow hackers access to other accounts that share the same password. If managing strong passwords is a challenge for you, consider using a password manager.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.