Remove Xentari ransomware
Xentari ransomware is designed to encrypt users’ files. If a device gets infected, the ransomware will immediately begin encrypting personal files. Affected files will have the .xentari extension added to them. You will not be able to open files with that extension unless they are first put through a decryptor. However, getting a decryptor is going to be difficult because only the malicious actors operating this ransomware have it. They will demand almost $60,000 for it. At the moment, only users who have backups can recover their files for certain.
Xentari ransomware is a type of malicious software that encrypts files. Ransomware can be identified by the file extension it appends to encrypted files. For Xentari ransomware, the extension is .xentari. For example, a file named text.txt would be renamed to text.txt.xentari. Once it’s initiated, this ransomware immediately begins encrypting personal files, specifically photos, videos, and documents, effectively rendering them unopenable until they’re put through a special decryptor. Malicious actors demand payment in exchange for the decryptor.
After encryption, a README_XENTARI.txt ransom note is dropped, instructing victims to send 0.5 BTC to the provided wallet address. At the moment of writing, 0.5 BTC is $59,000. The note warns against using third-party tools to decrypt files, and gives a deadline of 72 hours to pay or the decryptor price doubles.
The ransom demand is outrageously big, so unless the victims are businesses, no one is going to pay. In general, paying the ransom is never recommended because it does not guarantee that a decryptor will be sent. Users should always keep in mind that ransomware operators are cybercriminals. Not only does paying the ransom not guarantee a decryptor will be sent, but the money also goes towards future criminal activities.
If backups are unavailable, recovery is only possible by waiting for cybersecurity experts to develop a free Xentari ransomware decryptor. Although no such tool exists currently, victims can back up the encrypted files and periodically check NoMoreRansom for updates on free decryption tools. For those with backups, it is crucial to remove Xentari ransomware before accessing them to prevent further encryption. To safely delete Xentari ransomware, using a reputable anti-malware program is necessary, as this type of infection is very sophisticated.
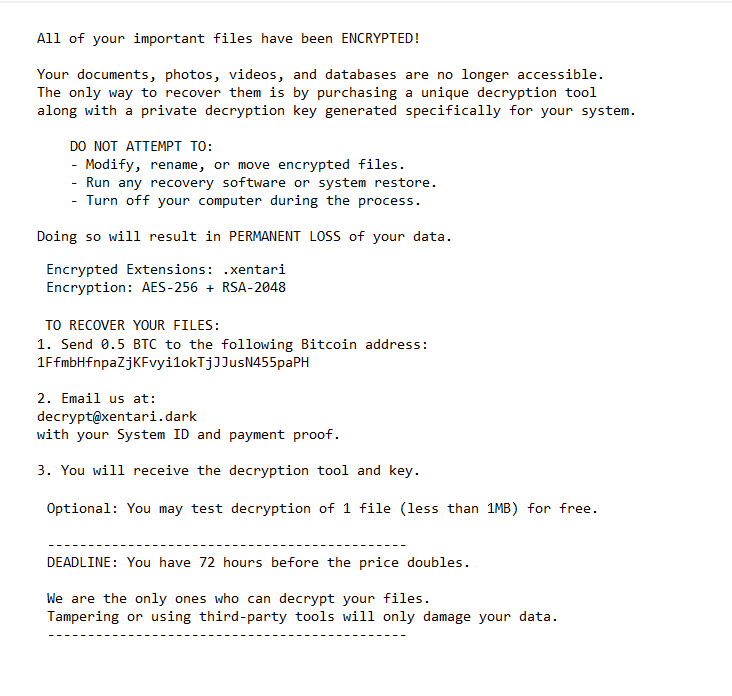
The full README_XENTARI.txt ransom note is below:
All of your important files have been ENCRYPTED!
Your documents, photos, videos, and databases are no longer accessible.
The only way to recover them is by purchasing a unique decryption tool
along with a private decryption key generated specifically for your system.DO NOT ATTEMPT TO:
– Modify, rename, or move encrypted files.
– Run any recovery software or system restore.
– Turn off your computer during the process.Doing so will result in PERMANENT LOSS of your data.
Encrypted Extensions: .xentari
Encryption: AES-256 + RSA-2048TO RECOVER YOUR FILES:
1. Send 0.5 BTC to the following Bitcoin address:
1FfmbHfnpaZjKFvyi1okTjJJusN455paPH2. Email us at:
decrypt@xentari.dark
with your System ID and payment proof.3. You will receive the decryption tool and key.
Optional: You may test decryption of 1 file (less than 1MB) for free.
———————————————
DEADLINE: You have 72 hours before the price doubles.We are the only ones who can decrypt your files.
Tampering or using third-party tools will only damage your data.
———————————————
Ransomware distribution methods
Ransomware can enter your computer in various ways, such as malicious email attachments (known as malspam), fake software updates, torrent downloads, and harmful advertisements. Poor browsing habits make you more vulnerable to malware attacks. Thus, developing better online habits and familiarizing yourself with common malware distribution methods is a good idea.
Malspam is a common method for spreading malware. Cybercriminals can buy leaked email addresses from hacker forums to use them to launch malicious spam email campaigns with harmful attachments. These emails are harmless unless you open the attachments; doing so activates the ransomware, which begins encrypting your files. Luckily, malspam emails are usually easy to spot due to grammar and spelling mistakes and suspicious sender addresses. If you’re cautious with all unsolicited emails, you can often avoid these threats. To be extra safe, scan all attachments from unknown senders using antivirus software or services like VirusTotal.
Torrents also pose a risk for malware. Torrent sites often lack proper moderation, making it easy for attackers to upload infected files. This is especially risky when downloading popular entertainment content. Using torrents for downloading copyrighted content illegally not only breaks the law but also puts your personal data and computer at risk.
How to remove Xentari ransomware
Due to the complex nature of ransomware infections, it’s essential to use an antivirus program to remove Xentari ransomware. Attempting to remove it manually may result in further complications. Additionally, do not access your backup until the ransomware has been completely eradicated, as this could result in the encryption of those files as well.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.