9 Ways to Hack Your Bitcoin Wallet
1. Email Phishing
An email arrives in your inbox, seemingly from a service you are familiar with or have used before. The email looks completely legitimate, but it is not. Hackers make their phishing emails look identical to legitimate service emails, with the same formats and design used, thus it can be difficult to differentiate them. In some cases, the company hackers are pretending to be from may not even have your email, but you might not even realize that.

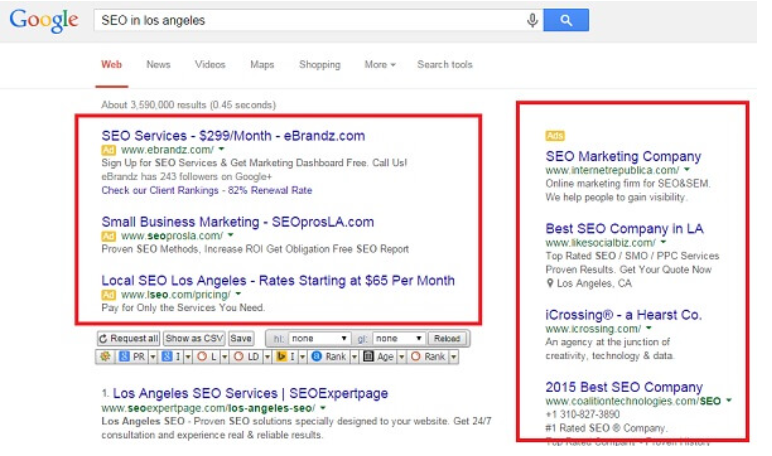
2. Fake Google Ads/SEO:
A quite known technique involving hackers replacing the top results in search engines with similar links to their websites. You use a search engine to look for crypto websites, click on the first results and end up on crooks’ sites because they have replaced legitimate results with their site URLs.
3. Copy Paste:
This method involves a program changing a wallet address you put in into one that belongs to crooks. You decide to transfer some kind of cryptocurrenty (whether it’s Bitcoin or Ethereum) to someone, copy their wallet address, paste it in your wallet and prepare to send the cryptocurrency. A special program, like CryptoShuffler, then changes the receiver’s wallet address into one of cyber crooks’ and you transfer the money to them without even realizing.

4. Clone Websites:
A more elaborate technique involves crooks changing an URL when you type it in the browser address bar. You start typing the URL, it gets changed to a different one (a scam website), and you’re suddenly led to a different, but seemingly identical website. The site may look completely identical to the one you intended to access so you may not realize you’re dealing with a scam page until it is too late.
5. Hacked Mobile Apps:
If you are not careful when installing apps onto your smartphone, you should be especially wary of this method. Scammers can create apps that would supposedly allow you to participate in crypto-exchange, but after some time, you’d realize that you’re not trading anything with it, merely sending money to the scammer’s account.

6. WiFi Hacking
A serious flaw in WPA, a security protocol for WiFi routers, can be taken advantage of to allow hackers to see data going through your WiFi network. Public WiFi (airport, cafe, station, etc.) users are particularly vulnerable to this.

7. Slack Hacking Bots:
A bogus security warning relating to your wallet could be sent to you, you would unsuspectingly press on the URL in the warning, give away your private key and other wallet information, and suddenly someone would have access to your wallet.
8. Browser Extensions
You need to be careful with browser extensions. There are many falsely offering to improve your experience when on trading websites, but instead of doing that, they could be recording everything you type in regards to your wallet. You need to be careful with such extensions, and before installing any of them, make sure they are safe to use.

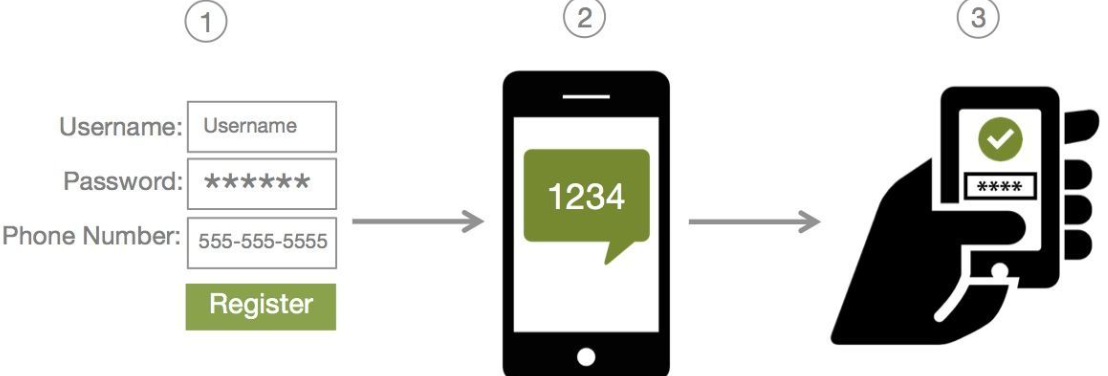
9. Mobile SMS 2FA
It’s not unusual for services to rely on SMS 2FA (two-factor-authentication) for an extra layer of security for the users. However, hackers have found ways to intercept the SMS 2FA, gaining access to the code. This could grant them access to various accounts, including those of Coinbase.
That’s all we have right now and Please note Only one tip to summarize all this: BE extra careful
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
