Cybersecurity news headlines for February 2021
February has been a quiet month in cybersecurity, with relatively few big stories. After a disastrous Cyberpunk 2077 release, game developer CD Projekt Red suffered a serious ransomware attack. More than 30,000 Mac computers were found to be infected with new Silver Sparrow malware. Russian internet company Yandex revealed an internal breach that exposed almost 5,000 email accounts. And FTC reported that romance scams made record money sums in 2020.
Without further ado, here’s what made the biggest cybersecurity news headlines in February 2021.
Over 30,000 Mac computers have been infected with new Silver Sparrow malware
Malware researchers have discovered a new piece of malware that infects Mac computers. New malware being detected usually does not make headlines but the sheer amount of infected Mac computers and its strange behavior has caught a lot of attention from both specialists and the media.
Researchers at security company Red Canary were the first to discover this new malware, which they dubbed Silver Sparrow. And according to anti-virus software vendor Malwarebytes, around 30,000 Mac computers all over the world have been infected. But the purpose of the malware is unclear as it doesn’t do anything malicious, or rather it doesn’t do anything. Despite having a large number of infected computers, the malware does not deliver a payload. The only thing that the malware does is connect to a command-or-control server every hour to check for instructions. Furthermore, it has the ability to remove itself and all of its files, and will do is if it finds a ~/Library/.insu file on the Mac. Though, it’s not currently clear what triggers this.
“However, our investigation almost immediately revealed that this malware, whatever it was, did not exhibit the behaviors that we’ve come to expect from the usual adware that so often targets macOS systems,” Red Canary’s security researcher Tony Lambert said in a blog post.
Very little is actually known about the malware, its purpose and distribution methods, in particular, are still a mystery. The malware is (or was as Apple has taken measures to prevent future infections) installed via update.pkg or updater.pkg but it’s not certain how exactly the files ended up on users’ computers. One possible method, according to Red Canary, is malicious search engine results. It’s possible users were shown malicious search engine results, which if interacted with could have triggered the download.
“We suspect that malicious search engine results direct victims to download the PKGs based on network connections from a victim’s browser shortly before download. In this case we can’t be certain because we don’t have the visibility to determine exactly what caused the download,” Red Canary said.
Most anti-virus programs will detect the malware’s presence now so users can use any of the widely used security programs to check their Macs if they’re worried about the infection being present. Since the malware doesn’t exhibit any of the usual infection symptoms, it’s recommended that all Mac users check their computers for Silver Sparrow’s presence.
And despite the fact that it currently doesn’t deliver a payload, the fact that it managed to infect over 30,000 Mac computers in such a short amount of time is very worrying. Whatever its purpose may be, it serves as a reminder that Mac computers are not immune to malware.
Video game developer CD Projekt Red suffers a ransomware attack
CD Projekt Red, a Polish video game developer behind highly popular games like The Witcher series and Cyberpunk 2077, disclosed in early February that the company suffered a ransomware attack. The ransomware, which has since been identified as HelloKitty, was able to gain unauthorized access to the company’s internal network, encrypt and steal data.
“An unidentified actor gained unauthorized access to our internal network, collected certain data belonging to CD PROJEKT capital group, and left a ransom note the content of which we release to the public,” a message posted on Twitter disclosing the attack reads.
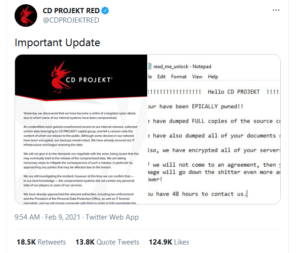 A notification about the ransomware attack posted on the company’s official Twitter account
A notification about the ransomware attack posted on the company’s official Twitter account
CD Projekt Red also released the ransom note which was dropped by the ransomware. In it, the malicious actors claim to have stolen source codes for Cyberpunk 2077, Witcher 3, Gwent, and an unreleased version of Witcher 3, as well “documents relating to accounting, administration, legal, HR, investor relations and more!”.
Encrypting the company’s data was not the main objective behind the attack, as even the ransom note mentions that CD Projekt Red will likely recover data from their backups. Rather, the cybercriminals operating the ransomware were hoping CD Projekt Red would pay them to not leak the data they have stolen, including games’ source codes. As expected, the game developer did have backup and started the recovery process immediately after securing their network.
It has not been disclosed how much the cyber crooks requested but CD Projekt Red said they had no intention to pay or negotiate from the very beginning. The source code was indeed leaked, and according to reports, it was auctioned for a minimum of $1 million. The code was later shared on social media, though CD Projekt Red started using DMCA to take down posts sharing it.
The company has notified all relevant authorities and the investigation is still ongoing. It also reassured users that compromised systems did not contain any kind of customers’ personal data. The affected systems have since been secured and the data has likely been fully restored from backup.
After a rather disastrous release of the long-awaited Cyberpunk 2077, users started speculating that the perpetrator was an unsatisfied gamer, but security researcher Fabian Wosar quickly identified the ransomware as HelloKitty.
The amount of people that are thinking this was done by a disgruntled gamer is laughable. Judging by the ransom note that was shared, this was done by a ransomware group we track as “HelloKitty”. This has nothing to do with disgruntled gamers and is just your average ransomware.
– Fabian Wosar (@fwosar) February 9, 2021
Yandex employee reportedly sold access to almost 5,000 email accounts
Moscow-based internet company Yandex revealed earlier in February that an employee had sold access to 4,887 email accounts. The Russian search engine and email provider said that the employee in question was one of three system administrators and had access rights for providing technical support for the mail service.
According to the press release posted on Yandex official website, the internal breach was discovered during a routine screening by Yandex’s security team. The employee, who has not been named, provided unauthorized access for “personal gain”. While according to Yandex, no payment information stored by Yandex was compromised, almost 5,000 email account were potentially accessed by unauthorized parties.
According to the company, owners of the affected email accounts have been notified about the situation. The compromised accounts were also secured, and all unauthorized logins were blocked. Affected account owners should change their account passwords as soon as possible. Appropriate authorities have also been reportedly contacted, and the employee is no longer part of the company. The company also said that changes will be made to the administrative access procedures in order to “minimize the potential for individuals to compromise the security of user data in future”.
FTC reports a 50% increase in losses related to romance scams in 2020
A report by US Federal Trade Commission (FTC) revealed that 2020 was a record-breaking year for romance scammers, as reported losses to romance scams in 2020 were a record $304 million. While these scams have been on the rise for the last couple of years, this is a 50% increase in losses compared to 2019.
The rise in romance scams can be attributed not only to the COVID-19 pandemic but also to the general increase in the usage of dating apps. The global pandemic has certainly played a huge factor as quarantine has forced many people to switch from in-person dating to online dating apps. And, unsurprisingly, scammers are doing their best to take advantage of the situation.
The way romance scams work is scammers create fake profiles on dating apps and social media using pictures taken from the Internet. They make up names, profile information, essentially create an entirely new persona in order to scam people. Though in some cases, scammers impersonate real people. They then make contact with potential victims and try to establish a connection with them. Even after a while, the scammers will not respond to requests to meet in person, which would not be that suspicious in today’s world considering most of the world is in lockdown and meeting in person is discouraged. And once some kind of bond has formed between the victim and the persona the scammer is playing, scammers will start asking for money.
The requests will be small in the beginning, but as time passes, the sums will get larger and larger. Scammers make up all kinds of scenarios on why they would need the money, from needing money to pay the phone bill to being stuck in a dangerous country with no money to leave. And since victims would have already grown to care about the person at the other end, they would send the money with little hesitation, despite not having met them in real life. In certain cases, victims end up laundering stolen money as well. Scammers would transfer them money and then ask victims to transfer it to someone else, and victims would unknowingly be committing a crime.
According to the FTC report, the usage of gift cards to send money to romance scammers has increased by nearly 70%. That, and wire transfers are reportedly the primary way victims send romance scammers money. The biggest increase in romance scam reports was among people ages 20 to 29, almost double that of 2019. This is rather surprising, as people in that age group should be most familiar with dating apps and the potential dangers that come with them. People aged 70 and over reported the highest individual median losses at $9,475.
References
- Tony Lambert. Clipping Silver Sparrow’s wings: Outing macOS malware before it takes flight. Red Canary Blog.
- Thomas Reed. The mystery of the Silver Sparrow Mac malware. Malwarebytes Labs.
- Press Release. Yandex internal security team uncovers data breach. Yandex.
- Emma Fletcher. Romance scams take record dollars in 2020. Federal Trade Commission blog.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.

