Cybersecurity news headlines for March 2022
In March’s edition of cybersecurity news headlines, there are three stories to discuss. A malicious app was downloaded over 100,000 times from the Google Play Store, alleged REvil’s hacker is facing a 115-year prison sentence, and software company/two-factor authentication provider Okta revealed a cyber incident that potentially impacted 2.5% of its customers.
Without further ado, here’s what made the biggest cybersecurity headlines in March 2022.
Malicious app downloaded 100,000 times from Google Play
Android app Craftsart Cartoon Photo Tools has been identified as an Android trojan dubbed Facestealer. The app was available on both Google Play Store and on other third-party app stores and was advertised as an app that can modify photos into cartoons. The malicious app was downloaded over 100,000 times from Google Play before it was removed from the store following reports from specialists. While it was disguised as a photo modifier app, in reality, it’s a malicious app that phishes login credentials.
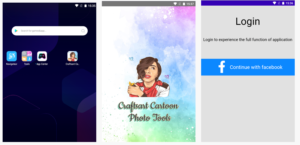 The concealed Facestealer app (Pradeo)
The concealed Facestealer app (Pradeo)
When users download and install the app, they will be asked to log in using Facebook in order to even use the app. When the credentials are entered, the app will send them to a command and control (C&C) server operated by the malicious actors. Stolen credentials are usually sold on hacker forums to other cybercriminals or they’re used by the cybercriminals themselves. Whatever the case, users who fall for this phishing campaign will likely lose access to their Facebook accounts. Hijacked accounts can be used for a variety of purposes, including sending phishing links, committing fraud, spreading fake information, etc.
The app has since been removed from the Google Play Store but not before potentially 100,000 users gave away their Facebook credentials to malicious actors. This is not the first time a malicious app was able to bypass Google Play’s security measures to be listed. Malicious actors find different ways to achieve this and in this case, Facestealer operators did so by injecting a small piece of code into an otherwise legitimate app. It allowed the malicious app to slip past all the safeguarding on Google Play.
The app itself is pretty low-effort and more attentive users will notice the unprofessional interface, as well as numerous mistakes. For example, Facebook is written with a lowercase “f”. Furthermore, the fact that it’s necessary to log in to Facebook to use a random app should raise alarm bells for users. Legitimate apps do give the option to log in using Facebook but it’s never the only option. And while it may be a convenient option, using Facebook to log in to even legitimate apps is not a good idea.
If users inspected the Craftsart Cartoon Photo Tools app before downloading it, they would have encountered clear signs of it being potentially malicious. The developer being named Google Commerce Ltd gives the impression that Google is behind this app but the provided email address susnnaooysh776@gmail.com quite obviously does not belong to Google. Furthermore, the app had a score of 1.7 at the time of deletion, and many reviews pointed out that it was fake or could have led to Facebook account hijacking.
Users tend to trust Google Play and often download apps without double-checking anything. But while Google is certainly much safer to download from than third-party app stores, it’s not perfect at keeping malicious apps away.
Alleged hacker behind Kaseya cyberattack extradited to Texas
Yaroslav Vasinskyi, the alleged hacker involved with REvil’s ransomware attack on Kaseya in 2021, has been extradited and arraigned in Texas. The US Department of Justice (DOJ) revealed that the Ukrainian is linked to the Russian-based cybercrime group REvil. Vasinskyi was apprehended in Poland in October last year and is being charged with conspiracy to commit fraud and related activity in connection with computers, damage to protected computers, and conspiracy to commit money laundering. If convicted, he could be facing a total of 115 years in prison.
Vasinskyi is suspected to be responsible for the Kaseya cyberattack that affected hundreds of companies all over the world and is believed to be the mastermind behind the cybergang’s operations. The REvil group is also accused of carrying out the ransomware attack on food supplier JBS. According to the indictment by the DOJ, Vasinskyi has been part of REvil since 2019 and is responsible for launching at least 2,500 attacks.
“In the alleged attack against Kaseya, Vasinskyi caused the deployment of malicious Sodinokibi/REvil code throughout a Kaseya product that caused the Kaseya production functionality to deploy REvil ransomware to “endpoints” on Kaseya customer networks. After the remote access to Kaseya endpoints was established, the ransomware was executed on those computers, which resulted in the encryption of data on computers of organizations around the world that used Kaseya software,” the DOJ has said.
Okta suffers a cyber incident
On March 22, notorious hacker group LAPSUS$ shared screenshots on Telegram claiming that its hackers were able to get access to software company Okta’s systems. The company offers two-factor authentication to companies and organizations. Among its customers are Siemens, Nordstrom, and JetBlue.
The CEO of Okta Todd McKinnon confirmed that the company did suffer an incident in late January, and the screenshots are linked to that particular event. The breach is believed to have originated with a computer used by a third-party customer support engineer working for Sitel, to which malicious actors had access between January 16 and January 21.
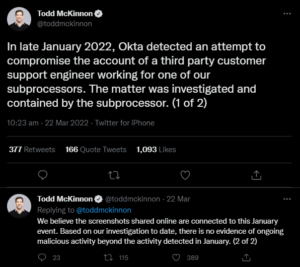 Okta CEO Todd McKinnon confirms cyberattack
Okta CEO Todd McKinnon confirms cyberattack
Okta became aware of the incident immediately when the company’s security received an alert that a new factor was added to a Sitel employee’s Okta account from a new location. The incident was investigated and Sitel hired a leading forensic team for outside support. However, the incident was not made public until the hacker group responsible shared screenshots online in late March.
“After a thorough analysis of these claims, we have concluded that a small percentage of customers – approximately 2.5% – have potentially been impacted and whose data may have been viewed or acted upon. We have identified those customers and already reached out directly by email,” Okta’s Chief Security Officer David Bradbury initially said in a blog post.
Okta assured that during the 5-day period between January 16-21, 2022, when the malicious actor(s) had access to Sitel, only minimal malicious actions could have been taken. The company noted that Sitel’s customer support engineers have very limited access and cannot create/delete users or download customer databases. They can, however, trigger a password or 2FA reset without being able to choose the password. So what the attackers could have done was repeatedly trigger a password reset for users without being able to actually log in to the service. Impacted customers have already been contacted. The company reassured customers that they do not need to take any corrective actions.
Okta also acknowledged that it made a mistake in delaying notifying customers of the incident.
“In January, we did not know the extent of the Sitel issue – only that we detected and prevented an account takeover attempt and that Sitel had retained a third party forensic firm to investigate. At that time, we didn’t recognize that there was a risk to Okta and our customers. We should have more actively and forcefully compelled information from Sitel. In light of the evidence that we have gathered in the last week, it is clear that we would have made a different decision if we had been in possession of all of the facts that we have today,” Okta said.
The company revealed that they no longer work with Sitel and have terminated their account access.
References
- Roxane Suau. Spyware dubbed Facestealer infects 100,000+ Google Play users. Pradeo.
- Sodinokibi/REvil Ransomware Defendant Extradited to United States and Arraigned in Texas. The United States Department of Justice.
- Raphael Satter. Hackers hit authentication firm Okta, customers ‘may have been impacted’. Reuters.
- David Bradbury. Updated Okta Statement on LAPSUS$. Okta.
- Frequently Asked Questions Regarding the January 2022 Compromise. Okta.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.


