Cybersecurity news headlines (July 1 – July 15)
July has been a pretty quiet month so far but we do have a couple of headlines to report. There were a couple of data breaches, military information stolen, users threatened with their porn viewing habits and the never ending Facebook controversy. But we did not witness any major incidents so it’s been relatively peaceful.
Here are the news that made headlines in July 1 – July 15.

Scam emails threaten to expose porn viewing habits
A new extortion scam has been noticed to hit users, and it’s threatening to send out a video of users watching adult content. While such emails have been around for a while, they are getting more convincing by revealing users’ passwords.
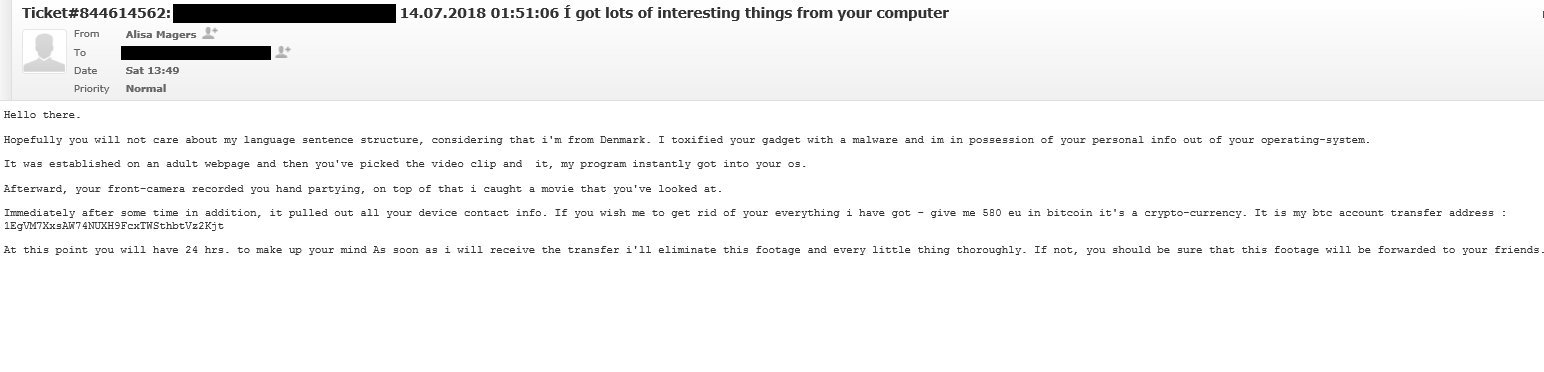
In such sextortion emails, the scammer first explains that they have set up some kind of malware on an adult website. The victim has supposedly visited the website and watched an adult video, which prompted that malware to download on his/her computer. The scammer then claims that a video of the victim watching pornography has been taken via webcam, and it will supposedly be sent to contacts that have been stolen from the user’s device. If victims want those videos to be deleted, they are requested to pay from a couple of hundred to a few thousand dollars.
The new, more elaborate scams also try to scare users by revealing passwords. Those passwords are taken from data breaches (which is how they got the email address as well) and may match the password the victim is actually using or has used in the past. However, a correct password does not make the scam any more legitimate, it simply means the victim’s information has been revealed in some kind of data breach. Passwords should be changed immediately after a breach to avoid crooks getting access to accounts.
If it has not been clear enough yet, these emails are scams, and scammers don’t actually have any videos made via webcam. They’re simply trying to extort money by intimidating users.
Hacker gains access to U.S. military information
It has been revealed that a hacker gained access to top-secret documents on Air Force computers and later tried to sell them on the deep web for only a few hundred dollars. More worryingly, the attack was not even that sophisticated, indicating that the hacker may have been low-level.
Internet company Recorded Future were the ones who stumbled upon the secret information being sold on the dark web for between $150 to $200. The company were able to speak to the hacker directly and found out that the attackers were able to successfully get access to at least two U.S. military personnel computers via a known vulnerability in Netgear routers.
While it does not seem that the information stolen is classified, it is still highly sensitive and could have led to serious incidents if found by the wrong people. The information included training manuals that describe deployment tactics for improved explosive device (IED), how to operate an M1 ABRAMS tank; documents explaining tank platoon tactics and maintenance books for MQ-9 Reaper drone servicing.
Hack on Bancor cryptocurrency exchange results in $13.5 million stolen
Israeli-based cryptocurrency exchange Bancor revealed that it suffered a security breach, which resulted in about $13.5 million worth of cryptocurrency stolen. On July 9th, an unknown attacker gained access to one of the company’s wallets, which was used to upgrade smart contracts.
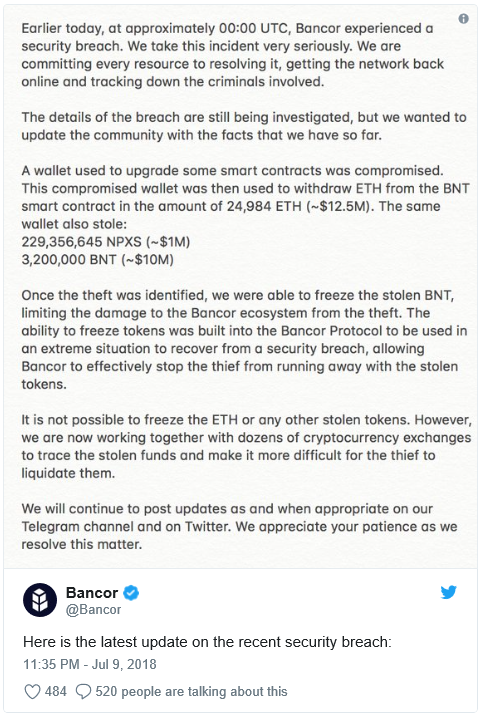
“The compromised wallet was then used to withdraw ETH from the BNT smart contract in the amount of 24,984 ETH (~$12.5M). The same wallet also stole: 229,356,645 NPXS (~$1M), 3,200,000 BNT (~$10M)”, Bancor posted on Twitter.
According to the same report, as soon as the theft was identified, Bancor was able to freeze the stolen BNT and limit the damage to the Bancor ecosystem. However, the company said that while it was not possible to freeze the ETH or any other stolen tokens, they are working with other cryptocurrency exchanges to trace the stolen funds and make liquidating them more difficult.
Timehop affected by data breach, resulting in information of 21 million users stolen
Smartphone app Timehop has revealed that they were a victim of a data breach, during which certain personal information of around 21 million users was accessed by unauthorized parties. While initially it was thought that only information such as names, email addresses and phone numbers was taken, it was later revealed that date of birth, as well as gender may have also been accessed.
Timehop is a basically a time capsule app that resurfaces past social media posts. While there were concerns that the hackers also had access to social media posts, the company reassures that while that is possible, there is no evidence confirming that to be the case.
The company revealed that the malicious party gained access to Timehop’s cloud computing account and transferred the data. Within two hours, the attack was noticed by Timehop and stopped. However, data of 21 million users was still stolen.
Law enforcement has been informed about the breach and an investigation has been launched. Timehop has also added multifactor authentication to its cloud accounts and has informed its users about the breach.
Facebook admits to sharing its user data with 61 companies
Back in 2015, Facebook banned third-party apps from accessing users’ and their friends’ information. These more strict guidelines on how user data is handled were introduced in 2014, and companies were given a year to transition and comply with the new regulations. However, Facebook revealed that it gave 61 companies extended access to users’ data. Companies like Panasonic, Nissan, NIKE, Oracle, Spotify were given an additional six months to access the data, despite Facebook saying these practices were no longer allowed.
Facebook has been in deep waters about how it handles its users’ information ever since the Cambridge Analytica scandal, which revealed that millions of Facebook profiles were harvested by Cambridge Analytica, a company believed to have helped U.S. President Trump win the 2016 elections. In response to the questions the social media giant received from the Senate and House Committees, Facebook submitted a 748 page document, which is where the company admitted to giving 61 companies an additional 6 months to access certain information about users. The information that could have been collected included name, gender, location, birthrate, photos, etc.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
