Drive by Exploit email – What you need to know
Drive by Exploit email is part of a spam campaign that extorts money
Drive by Exploit email or “Your computer was infected with my private malware” is a spam email that blackmails users into paying large sums of money. If you have received such an email, the scammer that sent it to you is likely claiming to have hacked your computer by installing malware onto it via drive-by exploit, hence the name of the scam. Supposedly, they have stolen all your contacts, personal information, and recorded you via webcam while you watched pornography. Furthermore, they threaten to expose the video to all your contacts. It goes without saying that this is merely a scam, and there is no video, nor have your contacts been stolen. Emails that threaten to expose those non-existent videos are called sextortion scams, and there has been an alarming increase in them in the past couple of years.
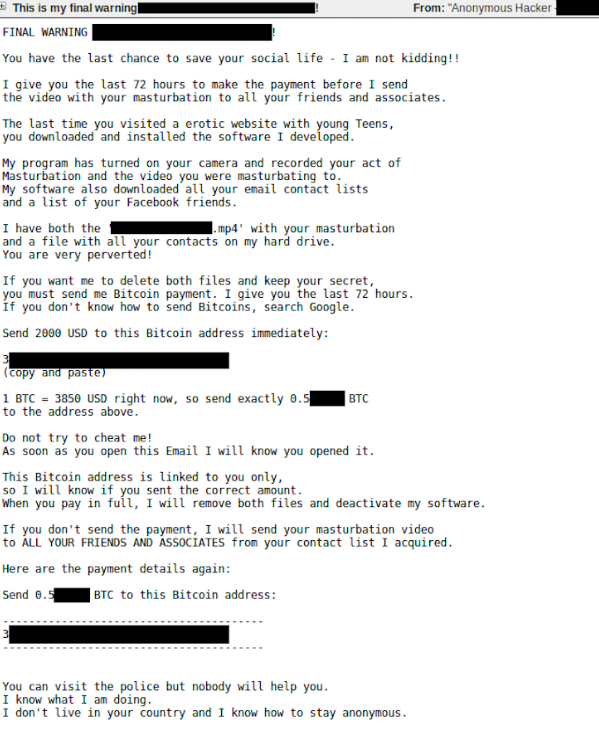
The email is written in quite a threatening manner. The scammer not only claims to have made a dual video of you via webcam and the pornography video you were watching, but also to send it to your contacts if you do not agree to pay the requested sum. Furthermore, the scammers threaten to publish the data publicly, and even on “the darknet, where the very sick people are”.
While sextortion scam emails may be worded differently, they follow the same pattern. They claim to have infected your device, stolen your contacts, recorded that video, and want you to pay in exchange for them deleting everything on their end. Typically, the money requested ranges from $700 to $1500, and Drive by Exploit email will likely request somewhere between that, depending on which scammers send you the email. You obviously do not need to pay, and can just delete Drive by Exploit email from your inbox.
Legitimate passwords are displayed in these “Your computer was infected with my private malware” emails
Soon after these emails started landing in users’ inboxes, scammers began inserting legitimate passwords into them in attempts to make them seem more real. It’s not difficult to see why displaying a password makes the email seem much more legitimate and why users would fall for it. Because how else would have these scammers have the password if not because they actually hacked the computer? The explanation of why scammers have passwords is quite simple. The password, as well as the email address, are obtained from old data breaches. It’s likely that your information was part of a data breach in the past and was sold on the net to hackers and scammers. The password is likely one you do not use anymore because the breaches are usually pretty old. However, in case it’s a password you currently use, you need to change it immediately.
Ignore the threatening messages like “I know one of your passwords”, or “Your password is”, and just delete Drive by Exploit emails from your inbox.
Remove Drive by Exploit email
If you receive a sextortion scam email, you don’t need to do anything besides delete it from your inbox. If the displayed password is one you use currently, change it immediately, and do not reuse passwords, at least for important accounts. If the email comes with some kind of attachment, do not open it. If you have opened it, we strongly suggest you scan your computer with anti-malware software as some kind of infection was likely hidden in the attachment.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
