Dropbox phishing email – What you need to know?
What is Dropbox phishing email
Dropbox phishing email refers to phishing emails that are made to look like they are sent by Dropbox. The scammers sending out these emails are aiming to hijack accounts by trying to phish login credentials from unsuspecting users. The email basically says that a file has been shared with the recipient, and they need to click on the link to access it. However, if the link is clicked, users would be taken to a fake Microsoft or other email provider website and asked to login to their emails. If users do put in their login credentials, they would be giving away those details to cyber criminals who could then access the account.
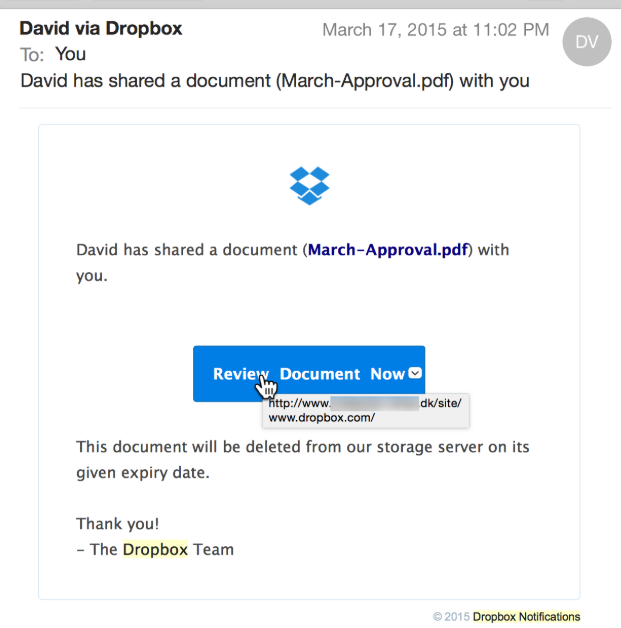
This particular phishing attempt is fairly simple and straightforward. It informs user that a file has been shared with them and that to view it they need to click on the provided link. Users who tend to skim read emails will not necessarily notice anything suspicious. It becomes very clear that one is dealing with a phishing email when users click on the link and are taken a site trying to imitate a Microsoft login page. The site itself looks fairly inconspicuous but the URL gives it away. One of the sites users are redirected to that we’ve seen is a Russian domain .ru. The correct Microsoft login page is login.live.com.
Users who have good browsing habits should definitely be able to tell this is a Dropbox phishing email. But there are plenty of users who are not familiar with phishing emails and have no idea what to look for.
How to spot a phishing attempt
Like we said, phishing emails are usually pretty obvious. The exception is when they target someone specific and have certain information that would make them open the email without much thought. But the generic ones are fairly obvious.
The first thing you should do when you receive an unsolicited email with an attachment or a link is check the sender’s email address. If the email is nonsense, you can immediately delete it. However, some phishing emails are sent from less obvious addresses. Cyber crooks use quite sneaky tactics to make the email addresses seem legitimate, such as imitating a known email address but changing certain letters such as “m” into “rn”, or adding additional ones to trick users. For example, you may receive an email seemingly from Netflix claiming that your account has been put on hold and you need to renter your payment details. The email address might have an additional “f” making it Netfflix, and unless you’re paying close attention, you may not notice this. So even when you receive an email from someone you know, inspect the email address carefully.
One of the most obvious signs of a phishing email is grammar and spelling mistakes. Scam and phishing emails are usually full of them. If an email that’s supposed to be official correspondence has a lot of mistakes in it, that’s more than a little suspicious. The Dropbox phishing email, however, has only a little text and it’s usually mistake-free.
When an email comes with a link and asks that you log in into your account, be very skeptical. You can hover over the link with your mouse and it will show you the site’s you’d be led to URL. The link in the Dropbox phishing email leads to a fake Microsoft website that shows the sign in field. At first glance, it may look identical to the legitimate one but the URL gives it away. As we’ve said above, the legitimate Microsoft login page is login.live.com, but the phishing site is on an unknown Russian domain. Before you log in anywhere, always check the URL and make sure it’s what it should be. We also always recommend that you access your accounts manually, not by clicking on links in emails.
Dropbox phishing email removal
If one such email lands in your inbox, you can safely remove Dropbox phishing email. Do not interact with it, do not click on any links and do not try to log in. If you have fallen for this phishing attempt, you need to change your password immediately. You also need to enable two-factor-authentication to make your account harder to access.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
