Ghas ransomware removal
Ghas ransomware is a file-encrypting malware from the notorious Djvu/STOP ransomware family. The ransomware holds personal files hostage by encrypting them and demanding payment for their decryption. Ransomware versions from the Djvu/STOP ransomware family are released on a regular basis, usually at least one ransomware per week. While they are mostly identical to another, they can be recognized by the extensions they add to encrypted files. This one adds .ghas, hence why it’s known as Ghas ransomware. You will not be able to open any files with this extension unless you first use a decryptor on them. However, acquiring a decryptor is not an easy task because the cybercriminals operating this ransomware are the only people who currently have it.
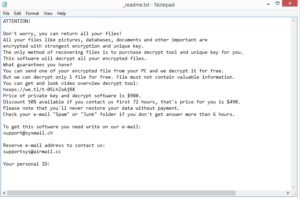
The ransomware will start encrypting files immediately after it’s initiated. It will target all personal files, including photos, videos, images, documents, etc. All files will have .ghas attached to them. For example, an encrypted image.jpg file would become image.jpg.ghas. Files that have this extension will be unopenable unless they are first put through a decryptor. But getting the decryptor will not be easy. The _readme.txt ransom note explains how victims can get the decryptor and it, unfortunately, involves paying a ransom. The decryptor price is $980 but according to the note, there is a 50% discount for users who make contact with the cybercriminals within the first 72 hours. Whether that is actually true or not is not certain but paying the ransom is not a good idea in general. There are no guarantees that you’ll actually get the decryptor even after paying. You are dealing with cybercriminals, and there’s nothing to force them to keep their end of the deal when they can just take the money with no consequences. The decision is yours but you do need to be aware of the risks.
If you have copies of your files in a backup, you can start the file recovery process as soon as you remove Ghas ransomware from the computer. Make sure to use anti-malware software and not try to do it manually because you could cause additional damage to your computer. When the anti-malware program is done removing the ransomware, you can safely connect to your backup and start recovering files.
The likelihood of successful file recovery is much lower if you do not have a backup. Your only option is to wait for a free decryptor to become available but it’s not certain when that will happen. Developing free decryptors for ransomware from the Djvu ransomware family has proven to be quite difficult for malware researchers because the versions use online keys to encrypt files. That means each victim has a unique key, and unless those keys are released, a free Ghas ransomware decryptor is not very likely. There is a free Djvu/STOP decryptor by Emsisoft but it only decrypts files that have been encrypted with a key Emsisoft has. But while it’s unlikely to work, it’s still worth a try. And since it’s not impossible that a free Ghas ransomware decryptor will be released eventually, you should back up your encrypted files and occasionally search for a decryptor.
How are ransomware infections distributed?
Ransomware operators/distributors use a variety of different methods to infect users’ computers. In most cases, malware distribution is done through email attachments, torrents, questionable downloads, ads, etc. Generally, users who have bad browsing habits are much more likely to pick up malware because they engage in high-risk behavior more often. Developing better browsing habits can help avoid a lot of malicious infections.
Malware is often distributed using email attachments. This is why it’s dangerous to open unsolicited email attachments without double-checking them first. It’s a pretty widely used method because it required very little effort. Malicious actors purchase email addresses from various hacker forums and then send them emails with malicious attachments. Fortunately for users, these emails are quite recognizable. Most noticeably, malicious emails are often full of grammar/spelling mistakes. The mistakes are especially noticeable because malicious senders often pretend to be from legitimate companies whose services users use. It goes without saying that because grammar/spelling mistakes look unprofessional, legitimate emails will rarely contain them. Furthermore, malicious senders often claim to be from companies whose services users use but address users with generic words like User, Member, Customer, etc. Legitimate emails from companies of which you’re a customer of will always address users with their names. But because malicious actors often do not know the names, they use generic phrases. In some cases, malware spam campaigns can be more sophisticated, which is why it’s a good idea to scan all email attachments with anti-malware software or VirusTotal before opening them.
Malware can also be found in torrents. Torrent sites are often quite badly regulated, which permits malicious actors to easily upload torrents with malware in them. It’s especially common to find malware in torrents for popular content (movies, TV shows, video games, software). The more popular some piece of content is, the more likely its torrent(s) will contain malware. So not only is pirating copyrighted content essentially stealing, but it’s also dangerous for the computer and personal files.
Ghas ransomware removal
Since ransomware is a very complex malware infection, we don’t recommend that you try to remove Ghas ransomware manually. If you try to do it yourself, you may accidentally cause additional damage or not fully delete Ghas ransomware from your computer. And if you tried to access your backup while ransomware was still preset, the backed-up files would become encrypted as well. And that may mean the files are lost permanently. Thus, it’s highly recommended to use reliable anti-malware software to remove Ghas ransomware. Once the ransomware is fully gone, you can safely access your backup to start the file recovery process.
If you do not have a backup, back up your encrypted files and keep them safe until a free Ghas ransomware decryptor is released. While it’s not available currently, it may be released in the future. However, it’s worth mentioning that there are many fake decryptors. Only download decryptors from reliable sources like NoMoreRansom. Otherwise, you’re risking additional malware infections.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.