How to remove Wbxd ransomware
Wbxd ransomware is one of hundreds of file-encrypting malware from the Djvu/STOP ransomware family. Files encrypted by this ransomware will have .wbxd added to them. It will also drop a _readme.txt ransom note, which will demand $980 for file decryption.
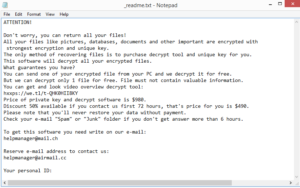 The ransom note dropped by Wbxd ransomware
The ransom note dropped by Wbxd ransomware
Wbxd ransomware is malware that essentially takes your files for hostage until you agree to pay a ransom of $980. This ransomware is part of a notorious Djvu/STOP malware family which has released hundreds of ransomware versions over the last couple of years. You can identify which version you are dealing with by the extension added to your encrypted files. In this case, the extension would be .wbxd. For example, a text.txt file would become text.txt.wbxd. You will be unable to open files with that extension, unless you first decrypt them using a specific decryptor. The problem is that the only people with the decryptor are the ones operating this ransomware. In the ransom note, which will be dropped in all folders containing the encrypted files, the malicious actors will explain how you can obtain the decryptor. And unfortunately, that includes paying a ransom of $980 (or $490 if you make contact within the first 72 hours of infection).
If you have backup for files, you should have no issue recovering them, provided you first remove Wbxd ransomware from the computer. However, if there is no backup, you may be considering paying the ransom. But we must warn you that it’s not a great option. Keep in mind that you are dealing with cyber crooks, meaning they may not necessarily feel obligated to help you. Unfortunately, many users in the past have received nothing in return after making a payment. And $980 is a lot of money, especially considering there are no guarantees you’ll be able to recover files.
We should warn you that you may encounter fake decryptors when looking for one on the Internet. Since a legitimate free decryptor does not exist at this moment in time, what you would end up downloading would be fake, and likely malware. If a decryptor was actually released, it would become available on NoMoreRansom. You can find a decryptor for older Djvu versions on there, but it will not work on versions that use online keys to encrypt files, which unfortunately includes Wbxd ransomware.
Ransomware infection methods
If your computer is infected with ransomware, you likely were pirating (such as via torrents), opened a malicious email attachment, or downloaded a software crack or a fake update. Developing better browsing habits can usually help avoid a malware infection.
You are likely already aware of this but pirating copyrighted content can often lead to a malware infection, especially via torrents. A lot of torrent platforms are so poorly regulated that anyone can upload anything, meaning malicious actors can easily upload malware torrents disguised as popular movies, games, TV shows, etc. So if you are one to download pirated content, do not be surprised if your computer gets infected. Similarly, you can easily pick up an infection by downloading software cracks.
Perhaps one of the most common ways users can infect their computers with infections like ransomware is by opening malicious email attachments. If your email address ever gets leaked, it will more than likely end up in the hands of cyber criminals who will use it to send malspam to. If you pay attention to the emails that land in your inbox, you should be able to easily spot malspam, as it would be full of grammar and spelling mistakes, and would pressure you to open the attachment by claiming it’s some kind of important document. The sender’s email address would also look suspicious. While it’s usually pretty easy to spot malspam, we suggest always scanning all unsolicited email attachments with anti-virus software or VirusTotal before you open them, just as a precaution.
We also want to stress the importance of installing updates in time. Whenever a vulnerability is detected, an update to patch it is usually released. If you don’t install that update, your computer becomes vulnerable, as malware could use said vulnerability to get into the computer. If you don’t want to be bothered with manual updates, enable automatic updating.
Wbxd ransomware takes personal files for hostage
To distract you from what’s about to happen, the ransomware will show a fake Windows Update window while it encrypts files. If you’re familiar with what Windows Update windows look like, it would immediately catch your attention as it does not look that convincing. In the meantime, it will encrypt your documents, photos, videos, images, etc., essentially all your personal files. They will all have .wbxd added to them so you will be able to easily tell which files have been encrypted.
As soon as it’s done with file encryption, it will drop a _readme.txt ransom note in all folders that have encrypted files in them. Besides a different link, the note is identical to the ones dropped by other ransomware in this family. It will explain that you can recover files, provided you pay the ransom.The ransom is $980 but a 50% discount would supposedly be given if you make contact with them within the first 72 hours. Contact email addresses provided in the note are helpmanager@mail.ch and helpmanager@airmail.cc. The note also contains your personal ID, which you would need to include in the email if you decide to make contact.
The malicious actors operating this ransomware offer to decrypt one file for free if it does not contain any kind of important information. It’s supposed to work as proof that they can decrypt your files. However, just because they can, does not mean they will. Like we said above, there is nothing stopping them from taking the money without sending you anything.
Wbxd ransomware removal
Ransomware is a highly complex malware infection, which is why you should use anti-malware software to delete Wbxd ransomware. Do not attempt to remove Wbxd ransomware manually because you could end up causing even more damage by deleting something you shouldn’t.
Only once the ransomware is no longer present on your computer should you access your backup to start recovering files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
