Remove ARROW ransomware
ARROW ransomware will take your files hostage as it’s a file-encrypting malware. You can recognize when you’re dealing with this particular ransomware when encrypted files have the .ARROW extension added to them. Unfortunately, you will not be able to open files that have this extension unless you first use a decryptor on them. However, acquiring the decryptor will not be easy, as only the malicious actors operating this malware have it. They will demand a payment for it, though buying it is not recommended, as you won’t necessarily get a working decryptor. Only users who have backups of their files can currently recover them for free.
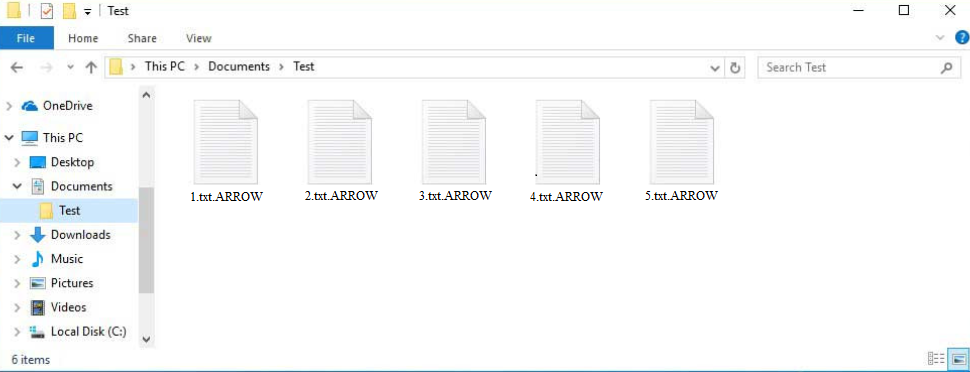
The ARROW ransomware begins encrypting files immediately after it is activated. You might not necessarily notice it happening, but once it’s done, it’s immediately clear that files have somehow been altered, as you will not be able to open them. They will also have the .ARROW extension added to them. For example, a 1.txt file would be renamed to 1.txt.ARROW if it is encrypted. Files with this extension become unopenable. The ransomware targets various file types, including documents and images, affecting anything that victims might want to recover.
Once the encryption process is complete, the ransomware drops a GOTYA.txt ransom note. This note explains that files have been encrypted using military-grade encryption, and that the only way to restore the files is with a special key, which you’d need to purchase. Unfortunately, the note’s content is more or less correct. The malicious actors request a payment for the decryption tool, although they do not disclose the specific amount, which is likely to be several hundred, if not thousands of dollars.
The full ARROW ransomware ransom note is below:
Oops. All the files on your computer have been encrypted with a military grade encryption algorithm. The only way to restore your data is with a special key that is hosted on our private server. To purchase your key and restore your data. please visit the darknet site
that is listed below.
Download the TOR browser and visit this site:
–Your ID: –
Specialists generally recommend against paying the ransom or communicating with the attackers for several reasons. Firstly, paying the ransom does not guarantee that victims will receive a decryption tool; they remain dependent on criminals who have no obligationto help once the payment is made. Furthermore, any money paid to these criminals will likely be used to finance their future illegal and malicious activities.
For those who have backup copies of their files, recovery can begin as soon as they remove ARROW ransomware from their systems. However, it is important to ensure that the ransomware is removed completely before accessing these backups. Otherwise, backups may become encrypted as well. To effectively and securely remove ARROW ransomware, users should use a reliable anti-malware program.
How does ransomware enter computers?
Users who tend to engage in risky online behaviour are much more likely to encounter malware infections. Users who adopt safer habits are significantly less likely to experience such infections, which is why it’s crucial to develop better online habits to avoid future threats. Understanding how malware spreads is equally important.
Having the skill to recognize malicious emails is particularly vital, especially if your email address has been exposed, as this is a common malware distribution method. Malicious emails are commonly disguised as order confirmations, shipping notifications, delivery notices, or similar messages to trick users into interacting with them. Fortunately, many of these emails are generic and can be identified by obvious grammar and spelling mistakes. Additionally, the use of generic words like “User,” “Member,” or “Customer” when addressing recipients could signal a spam or malicious email. Legitimate companies typically personalize their correspondence with the recipient’s name, whereas malicious senders opt for generic greetings because they do not have access to personal information.
It’s also worth mentioning that more sophisticated and tailored phishing emails usually have no mistakes, contain credible information, and address recipients by name. But they’re also usually reserved for specific, high-profile targets. However, just to be safe, you should always scan any unsolicited email attachments using anti-malware software or VirusTotal.
Torrents are also commonly used to distribute malware. It’s widely known that many torrent sites lack proper moderation, which allows malware-infested torrents to be uploaded. Often, malware is hidden in torrents for popular content such as movies, TV shows, and video games. Thus, not only is downloading copyrighted content through torrents essentially content theft, but it also presents significant risks to your computer’s security.
How to remove ARROW ransomware
Attempting to manually remove ARROW ransomware is not advisable, as it can result in further complications or damage to your computer. Ransomware is a sophisticated type of malware, which is why you have to use anti-malware tools for proper removal. If you have a backup, avoid connecting to it until you fully remove ARROW ransomware from your system.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.