Remove .hese Ransomware
About .hese Ransomware
.hese Ransomware refers to the Dharma ransomware. The infection is sometimes referred to as .hese ransomware because it adds the .hese file extension to all encrypted files. Dharma ransomware has been around for a while and has different versions. The most recent one adds the .hese. It’s a pretty serious infection to get because it could mean losing your files. Once it’s inside a computer, the ransomware will look for certain files (photos, documents, etc.) and encrypt them. Once that has happened, unless the files are decrypted, they will not be openable. To decrypt the files, a special decryption tool is necessary, and crooks will try to sell it to you. Selling t decryptors is how ransomware developers/distributors earn money, and that is one of the reasons why paying the ransomware is generally not recommended. Another reason is that the decryption tool might not even be sent to you. 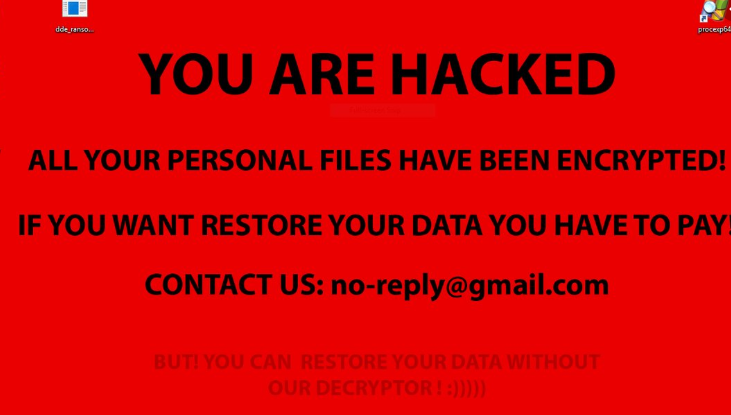
Dharma ransomware has many versions, such as .onion, .wallet, .dharma, .java. Unfortunately, none of its versions are decryptable without paying the ransom to get the decryptor. Users who regularly back up their files are fine, as they can recover files after they remove .hese Ransomware from the computer. Unfortunately, not all users have backup. Ransomware is one of the reasons why it’s so important that you store copies of your files somewhere, be it the cloud or an external drive.
Infecting a computer is pretty easy, and it usually happens when users open malicious emails attachments. The attachments are mostly attached to spam email, so if you stay away from spam, you should be good. We will further explain what emails with malicious attachments look like in the following section of this report.
How is .hese Ransomware distributed
Like most ransomware, .hese Ransomware spreads via spam email. Since people still open spam, it remains one of the more popular ways to spread ransomware. All criminals need to do is add the infected file to an email, write a semi-convincing email and send it to hundreds/thousands of email addresses obtained from various data breaches. The emails are usually money related as that is the most likely topic to catch people’s attention. The emails usually claim that the file attached is some kind of receipt for a purchase, or contains important information. When the file is opened, the ransomware can proceed to encrypt files.
Like we said, spam emails carrying malware are somewhat obvious if you know the signs. One of the most obvious ones is grammar errors in what’s supposed to be an official email. If your bank is supposedly emailing you, the email ends up in spam and there are grammar mistakes, the email is pretty obviously not actually sent by your bank. Other signs of the email being malicious include you not being addressed by your name, and strong pressure to open the attachment.
As a general rule, when you receive an unsolicited email with an attachment, it’s a good idea to scan it with anti-malware software before opening it. If your security program does not have that function, you can use VirusTotal.
Is .hese Ransomware dangerous?
Because ransomware encrypts files, it’s considered to be one of the most serious malware infections. When you open the .hese Ransomware infected file, the malware will immediately start encrypting your files. This can happen without users even noticing. The ransomware targets files with a lot of different file extensions, including .hese, .mp4, .docx, .doc. It essentially targets all files users would be willing to pay for. When files are encrypted, they get an additional file extension added to them. An encrypted file would look like this: filename.ID number.[email address for contacting crooks].hese. File extensions like .hese, .onion, etc., allow users to quickly determine which ransomware they are dealing with.
Once files are encrypted, you will see a ransom note. The RETURN FILES.txt ransom note explains that your files have been encrypted and to restore them, you need to write an email to the provided address. The note claims that the decryption key is stored only for 7 days, after which it would be deleted. The crooks also offer to decrypt one file for free as proof that they can. The note does not seem to specify the amount that needs to be paid to get the decryptor, but whatever it is, it’s not recommended to pay. We already mentioned above that paying does not mean the decryptor will be sent to you. Do not forget that you are dealing with cyber crooks who do not care whether you get your files back. It’s doubtful they feel any obligation to help you even if you paid.
Seeing as no .hese Ransomware decryptor is available, the only option to get files back is backup. All users are recommended to regularly back up any important files in case of ransomware or computer issues. There are plenty of backup options available, including the cloud and external hard drives. The files can be recovered from your backup only after the .hese Ransomware ransomware is fully removed from your computer. Otherwise, the files would be encrypted again.
.hese Ransomware removal
You should not attempt to uninstall .hese Ransomware manually. Instead use anti-malware software. Most reliable security programs will be capable of .hese Ransomware removal. After you delete .hese Ransomware, proceed to recover files. If backup is not an option, your only other solution is to wait for malware researchers to develop a free decryptor.
Try to find free file encryption tool here – https://www.nomoreransom.org/en/decryption-tools.html
IMPORTANT! Before downloading and starting the solution, read the how-to guide. Make sure you remove the malware from your system first, otherwise it will repeatedly lock your system or encrypt files. Any reliable antivirus solution can do this for you.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
