Remove HiveWare ransomware
HiveWare ransomware is a type of file-encrypting malware that locks users’ files by encrypting them and demands payment for a decryptor to restore access. This ransomware is identifiable by the .HIVELOCKED extension appended to encrypted files. Files with this extension cannot be opened unless they are put through a decryptor, which only the ransomware operators currently have. The malicious actors demand a payment of $600 in Bitcoin to a designated wallet, and once payment has been made, they will supposedly send the decryption software within 24 hours. However, paying the ransom does not ensure access to the decryptor. At present, only users with backups of their files can recover their data with certainty.
The type of ransomware infecting your computer can often be identified by checking the extension added to encrypted files. This particular ransomware adds the .HIVELOCKED extension to file names. For example, an image.jpg file becomes image.jpg.HIVELOCKED if encrypted. It targets all personal files, such as photos, videos, and documents, rendering them unopenable unless first decrypted. The only people with a functioning decryptor are the cybercriminals behind this ransomware, and they will demand that you pay $600 to get it.
Once the encryption process is complete, the HiveWare ransomware drops a ransom note titled HiveWare-ReadMe.txt. This note provides simple instructions on how to buy Bitcoin to pay the ransom, and specifies that $600 worth of Bitcoin should be transferred to the provided wallet address to get the decryption software. While the decision to pay ultimately lies with you, you need to be aware of the associated risks. First of all, paying the ransom does not guarantee you will get the decryptor, as there is no guarantee that the criminals will send you the decryptor. Many victims have paid the ransom in the past, only to receive nothing in return. What’s more, any money you pay will go towards financing future criminal activities, of which you could become a target again because you’ve paid the ransom once.
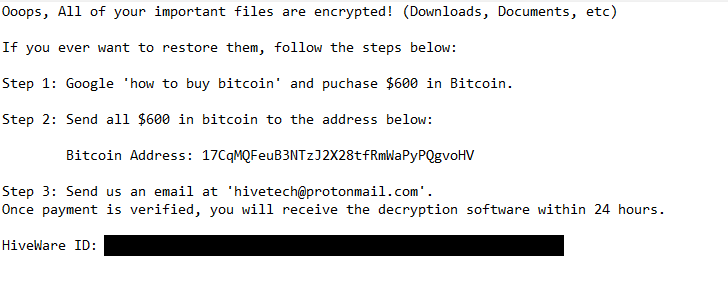
The full HiveWare ransomware ransom note is below:
Ooops, All of your important files are encrypted! (Downloads, Documents, etc)
If you ever want to restore them, follow the steps below:
Step 1: Google ‘how to buy bitcoin’ and puchase $600 in Bitcoin.
Step 2: Send all $600 in bitcoin to the address below:
Bitcoin Address: 17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHV
Step 3: Send us an email at ‘hivetech@protonmail.com’.
Once payment is verified, you will receive the decryption software within 24 hours.HiveWare ID: –
The only free way to recover your files currently is by using a backup. If a backup is unavailable, the best course of action is to wait for the release of a free decryptor; however, no such decryptor exists at this time. Should one become available in the future, it will be released on NoMoreRansom.
If you have a backup of your files, recovering them should not pose an issue. However, before anything else, you will have to remove HiveWare ransomware from the system using anti-virus software. Ensuring that the ransomware has been fully removed is very important, as connecting to a backup while the ransomware remains active could result in the encryption of the backup files as well.
Ransomware distribution methods
Malware often infiltrates computers through users opening malicious email attachments. Distributing malware through emails requires minimal effort from cybercriminals. They purchase email addresses in bulk from hacker forums and launch extensive malicious spam campaigns. These campaigns, targeting users randomly, are usually generic and easy to identify. Suspicious emails often originate from dubious addresses, contain numerous spelling and grammar mistakes, use awkward language, and address recipients with generic words while claiming to represent a company whose services users use. Legitimate companies address their customers by name and ensure their emails are free of mistakes to avoid looking unprofessional. Malicious actors rarely have access to personal information, so they use generic words to address users, such as “Member”, “Customer”, or “User”. Being able to recognize these signs can help identify most generic spam attempts.
To stay safe, it is recommended to scan all unsolicited email attachments with antivirus software or services like VirusTotal to detect potential malware, potentially saving significant trouble later on.
Another common method cybercriminals use to spread malware is through torrents. Torrent sites, often poorly moderated, allow malicious actors to upload torrents for popular movies, TV shows, video games, software, and more, embedding malware within the files. This is especially prevalent in torrents of newly released content. Downloading pirated content is not only content theft, but it also exposes your computer and data to significant risks.
Remove HiveWare ransomware
Ransomware is a serious malware issue, so it’s important not to attempt to remove HiveWare ransomware manually. Trying to do so could cause more problems with your computer, and you might accidentally leave behind parts of the ransomware, allowing it to recover. Additionally, connecting to your backup while the ransomware is still active could lead to your backup files being encrypted as well. The safest way is to use reliable anti-virus software to remove HiveWare ransomware before accessing your backup.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.