Top 5 Cyber Security Threats for 2016
Cyber security should be a concern for all computer users as nobody is immune to online attacks. That is why it is important to stay in the know about the latest online safety related issues. In this article, we will discuss top 5 cyber security threats that you should look out for in 2016.
1. Mobile Malware
Cyber criminals have been expanding their range of attacks for a while now, targeting not only computers, but also mobile phones and tablets. This tendency will continue on in the near future, especially considering the rising number of users who access their online banking accounts on their mobile devices. Handling banking needs in such a way is not the best idea, especially if your smartphone does not have any kind of a security application on it. Moreover, as retailers replace outdated point-of-sale systems with pin and chip devices, the attacks will shift from in-store to online and mobile ones.
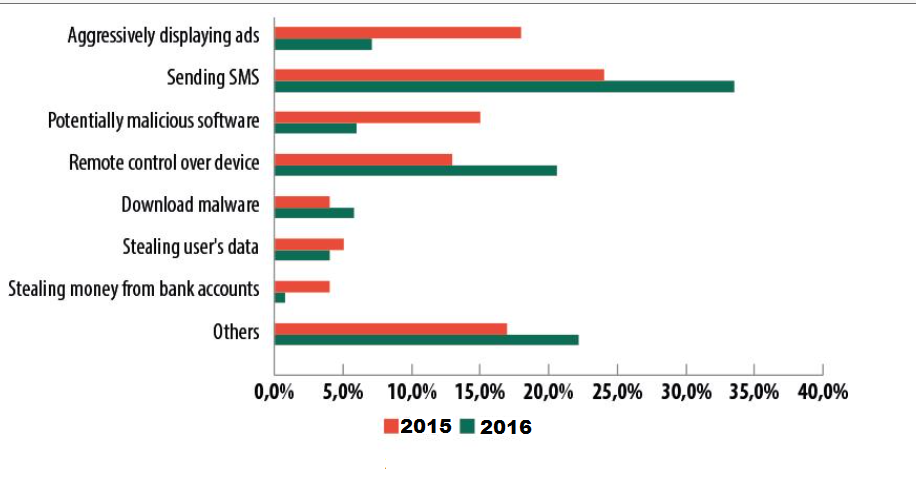
2. The Internet of Things
The Internet of Things refers to the connection of various devices including your home appliances, cars and so on to the Internet. Although there lots of advantages when it comes to these new technologies, there are also plenty of vulnerabilities to be exploited by hackers. The problem with having all of your devices interconnected is that if cyber crooks corrupt one of them, they get access to all other devices connected to it. These issues are relatively new, however, as the number of users that employ the Internet of Things grows, so will the number of possible risks related to it.
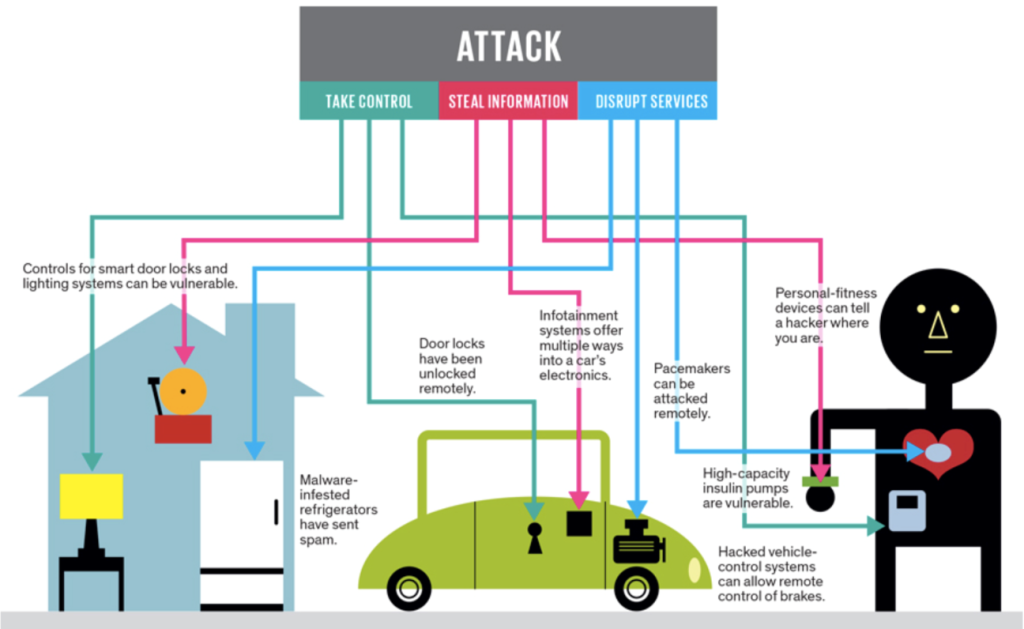
3. Data Theft for 2016
Personal data theft is not exactly a new trend, however, it is definitely a serious issue. Nowadays cyber criminals not only steal your information, but they also make sure that you can no longer access it yourself. Various ransomware applications have been spreading online for a while now. The malicious programs can infect your computer and encrypt your files demanding that you pay a ransom fee, if you wish to restore them. Needless to say, making the payment does not guarantee anything. The only way to deal with this type of cyber security issue is to have a powerful anti-malware tool protecting your system and to have your important information safely backed up.
4. Third-party attacks for 2016
Cyber crooks use third-party attacks in order to breach one target and gain the necessary credentials to infiltrate a much bigger one. Smaller companies that are not as secure as the market leaders can be exploited if they get hired by the large businesses. Adding a separate security screening for used contractors may help prevent unwanted attacks.
5. Vulnerabilities of major critical infrastructures
Another possible future concern has to do with critical infrastructure industries that are full of contradicting devices, which can easily be exploited. Some of the Industrial Control and Supervisory Control and Data Acquisition systems are over ten years old. These systems may suffer from remote cyber attacks, system failures, human error, and so on. As you can see, there are plenty of issues that may be caused by cyber criminals. It is hard to deny the fact that the number of these issues will continue to grow. That is why it is important for you as an individual user to be prepared for dealing with them. You can improve your cyber security by installing a reputable anti-malware utility onto your computer and making sure that it stays up-to-date.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.

