Delete Yoqs ransomware
Yoqs ransomware is a generic malware infection operated by the Djvu/STOP ransomware gang. The hacker group is responsible for releasing hundreds of ransomware versions, with Yoqs being one of the more recent ones. These versions are usually quite similar but it’s possible to identify them by the extensions they add to encrypted files. This one adds .yoqs. You will not be able to open any of the files with this extension because they’ve been encrypted. Acquiring the decryptor necessary to recover encrypted files can be difficult because only the cybercriminals operating this ransomware currently have it. And they will not just give it away for free.
Yoqs ransomware comes from the Djvu/STOP ransomware family and is mostly identical to Qqqw, Maak, Vfgj, Fhkf, and hundreds of others. Like most ransomware, Yoqs targets personal files, mostly images, photos, videos, documents, etc. You will be able to recognize which files have been encrypted by the extension added to them. Encrypted files will have .yoqs added to them. For example, image.jpg would become image.jpg.yoqs. None of the files with this extension will be openable unless you first decrypt them. But doing that will not be so easy. The only people who have a working decryptor are the people operating this ransomware. The ransom note will explain how you can get the decryptor.
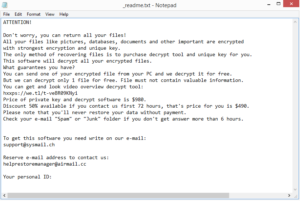
While it’s encrypting your files, the ransomware will try to distract you by showing a fake Windows update window. Once files have been encrypted, it will be quite obvious. In addition to encrypted files, you will also find _readme.txt ransom notes in all folders that contain encrypted files. The note explains how you can decrypt files. The cybercriminals operating this ransomware offer the decryptor for $980 but also promise a 50% discount to those who make contact with them within the first 72 hours. Whether they actually give the discount or not, paying the ransomware is rarely recommended. There are no guarantees that you would actually receive a decryptor since you are dealing with cybercriminals. They can easily just take the money and not send the decryptor since they’re not really obligated to help. It has, unfortunately, happened many times before. In addition, one of the reasons why ransomware is so widespread is because victims give in to demands and pay the ransom. As long as ransomware is profitable, cybercriminals will continue this malicious activity.
The best way to fight ransomware is to regularly back up files. If you keep them somewhere safe, whether ransomware gets into your computer will not matter because you will be able to recover files quite easily. If you are dealing with this ransomware but have copies of your files in a backup, you should have no issues with file recovery. However, before you connect to your backup, you need to completely delete Yoqs ransomware from your computer. Make sure to use anti-malware software because if the ransomware is still present when you access your backup, your backed-up files may become encrypted as well.
If you do not have copies of your files stored anywhere, waiting for a free decryptor may be your only option. However, developing a free decryptor for ransomware like Yoqs ransomware can be difficult because it uses online keys to encrypt files. That means that the keys are unique to each user, and without those keys, a decryptor will not work. So unless the cybercriminals themselves release the keys when they close up shop (or if law enforcement does it if they ever catch those responsible), it’s unlikely that a free Yoqs ransomware decryptor will become available. Nonetheless, you should back up your encrypted files and occasionally check NoMoreRansom for a free decryptor.
How does ransomware infect computers?
Ransomware, like most malware, is distributed via spam emails, torrents, ads, etc. Users with bad browsing habits have a much higher chance of picking up an infection. So developing better ones is a good way to avoid malware infections.
Torrent sites are notoriously badly regulated, and malicious actors certainly take advantage of this. They upload torrents for popular movies, TV series, video games, software, etc., with malware in them, and hope careless users fall for the trick. It’s particularly common to find malware in torrents for content that’s very popular. For example, when a new Marvel movie comes out, torrents for it are usually full of all kinds of malware.
But one of the most common ways users pick up malware is via email attachments. Malicious actors purchase email addresses from hacker forums, so if your email has ever been leaked, you have a high chance of receiving a malicious email. Fortunately for users, those emails are usually quite obvious. They are full of grammar and spelling mistakes, are sent from dubious email addresses, and address users with generic terms like User, Customer, Member, etc. Senders of these emails usually claim to be from legitimate companies whose services users use. For example, you may receive an email from someone claiming to be a parcel delivery service. But what gives these malicious emails away is usually grammar and spelling mistakes. Obviously, emails from legitimate senders will not contain any mistakes because they look unprofessional. Furthermore, emails from companies whose services you use will address you by your name, not generic terms.
It should also be mentioned that some malicious spam attempts will be more sophisticated, so it’s always recommended to scan all unsolicited email attachments with anti-virus software or VirusTotal before opening them.
Yoqs ransomware removal
Because ransomware is a very complex malware infection, it’s always recommended to use anti-malware software. So do not try to remove Yoqs ransomware manually and instead use anti-malware software. Once the ransomware is no longer present, you can start recovering your files safely. Keep in mind that if the ransomware is still on your computer when you connect to your backup, your backed-up files would become encrypted as well.
If you do not have a backup, your only option may be to wait for a free decryptor. Whether or not one will be released is questionable but there’s not much else you can do besides wait.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.