Flubot malware targets Android users in Australia
Thousands of Australians are being bombarded with scam text messages that are distributing the Flubot banking trojan. Scamwatch, a website run by the Australian Competition and Consumer Commission (ACCC), has released a warning advising users to not click on links in suspicious messages, as that would lead to a serious malware infection. Reportedly, over 5500 reports about this particular scam have been made to Scamwatch. Considering that many users do not report suspicious messages, the number of those who encounter this scam is likely much higher.
The new Flubot spam campaign targeting Australians has been noticed in early August this year, and in merely a month Australia’s Scamwatch has received over 5500 reports of these scams. Earlier this year, European users were bombarded by the same scam text messages.
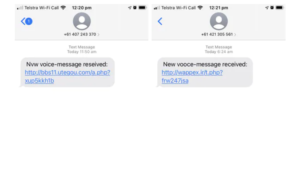
As displayed above, the text messages distributing Flubot come from different numbers every time and claim that there is a new voice message, which can be supposedly accessed by clicking on the displayed link. However, instead of listening to a voice message, users would be prompted to install the Flubot malware disguised as some kind of app if they click on the link. Interestingly enough, the grammar and spelling mistakes in the text messages are even more obvious than usual. For example, one message says “new vmice-meszage received”, while another claims that “you have a mqssed calk”. In some cases, malicious actors deliberately make such mistakes in order to eliminate users who are generally more cautious of such messages. However, in this case, it may be just a very low-effort distribution campaign.
The text messages include a suspicious-looking link, which if clicked would eventually lead to a malware infection. When the link is clicked, a window appears and displays the user’s phone number, as well as how long the supposed voice message is. Users would be instructed to download the “voicemail app” aka Voicemail71.APK. The downloaded “app” is actually the Flubot malware. During the installation process, users would be asked to allow the app to read and send text messages, make phone calls, access and extract contacts. It should be mentioned that Flubot is an Android malware and will not affect iPhone users, even if they receive the text message with the link.
Once the malware is installed, it will try to steal login credentials, credit card information, and personal details. This is done by displaying fake windows when users browse using the infected devices. For example, when users try to access their online bank website, they will be shown a convincing fake window where they would put in their login credentials. Once they are typed in, the credentials would be sent to the malicious actors operating this scam. This is how these scammers can steal all kinds of information.
Removing Flubot malware
Considering that the Flubot malware steals personal information and login credentials, immediate action is required if the infection is present on an Android device. There are three possible courses of action for victims. For users who have little confidence that they can deal with the infection themselves, it’s recommended to contact a professional. For those who wish to deal with it themselves, downloading an anti-virus app from the Google Play Store is an option, as is performing a factory reset. For those unaware, performing a factory reset would delete all data stored on the device, including photos, messages, and files.
Once the Flubot malware is gone, it’s necessary to change all passwords that have been entered when using the infected device. It should also be mentioned that passwords should never be reused. It’s also recommended to contact the bank in order to secure banking accounts and prevent any fraudulent transactions.
Tips on avoiding Android malware
Scams and malware affecting smartphone users are becoming more and more common, and that is unlikely to change in the future. However, it’s possible to avoid being affected as long as a few simple guidelines are followed. Below are a few tips for users to protect themselves.
- Never click on links in text messages. No bank, parcel delivery service, government agency/organization, etc., will ever send a text message with a link.
- Do not engage with scammers by calling the numbers from which scam text messages come. At the very least, calling them would signal that the phone number is actually in use and can be used in future scams.
- Do not trust text messages simply because the sender appears safe. Various spoofing techniques are used in these kinds of scams to disguise the actual sender.
- Do not download apps from unknown sources. While not 100% malware-free, the Google Play Store is the safest place to download apps from.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.