Qmak ransomware removal
Qmak ransomware is a generic file-encrypting malware that was released by the same cybercrime gang behind ransomware like Irfk and Palq. They all come from the same Djvu/STOP ransomware family and are very similar. You can identify which Djvu ransomware you’re dealing with by the extension that gets added to encrypted files. In this case, .qmak will be added to your personal files. You will not be able to open any of these files unless you first use a decryptor on them. Unfortunately, the only people with a working decryptor are the ones operating this ransomware.
Qmak ransomware is more or less identical to Qdla, Irfk, Palq, and Cool. They’re all ransomware from the Djvu/STOP malware family. Regular versions from this ransomware family are released on a regular basis, with hundreds of versions currently out there. Like most ransomware, Qmak ransomware targets personal files, including photos, videos, documents, images, etc. It’s pretty obvious when files are encrypted because they all have extensions added to them. This particular ransomware adds .qmak, hence why it’s known as Qmak ransomware. For example, image.jpg would become image.jpg.qmak. You will not be able to open files with that extension unless they are first decrypted.
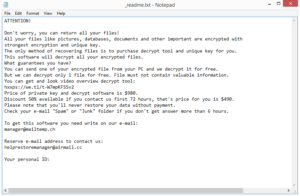
As soon as file encryption starts, the ransomware will try to distract you with a fake Windows update window. Once it’s done with file encryption, it will drop a _readme.txt ransom note that explains how to get the decryptor. Unfortunately, acquiring the decryptor involves paying $980. The note also mentions a 50% discount for those who make contact with the malware operators within the first 72 hours. Whether that’s true is hard to say, as is whether you’d actually get the decryptor if you paid the ransom. Keep in mind that you are dealing with cybercriminals and there is nothing to obligate them to actually send the decryptor when they receive the ransom money. It has happened many times in the past. In the end, it’s your decision whether you pay the ransom or not but you should be aware of the risks involved.
If you already had a habit of backing up files, you can start recovering them as soon as you remove Qmak ransomware from the computer. Use anti-virus software to delete Qmak ransomware because otherwise, you may not get rid of it fully, allowing the ransomware to recover. If you connect to backup while ransomware is still present, your backed-up files would become encrypted as well.
If you don’t have a file backup, the only way you may be able to recover files is by waiting for a free decryptor to be released. However, it will not necessarily be possible to release one because Djvu ransomware versions use online keys for file encryption. That essentially means that the keys are unique to each user. And without those keys, developing a free decryptor is unlikely. It’s not impossible that the keys will be released sometime in the future, so all hope is not lost. The cybercrooks themselves may release the decryptor when they eventually close up shop. Or law enforcement agencies may eventually catch them. So back up encrypted files and check NoMoreRansom for a decryptor from time to time. If you have already looked for a decryptor, you may have come across a free Djvu/STOP decryptor by Emsisoft. It is a working decryptor but it only works on versions that used offline keys to encrypt files. Ransomware released after 2019 usually does not do that.
Ransomware distribution methods
Users who have bad browsing habits are much more likely to pick up some kind of malicious infection because they open email attachments without first checking that they’re safe, download copyrighted content via torrents, click on ads while browsing high-risk websites, etc. Developing better habits would help avoid these kinds of infections.
If your computer is infected with a serious infection like ransomware, you may recall opening an unsolicited email attachment. Malware is often distributed via emails because it’s a relatively low-effort method. Malicious actors purchase thousands of leaked email addresses and then use them to launch their malspam campaigns. Because one campaign targets a large number of users, the emails are usually quite generic. They are full of grammar and spelling mistakes, are written in broken English, and use generic “User”, “Member”, “Customer” words to address users. Senders often pretend to be emailing on behalf of some company whose services users use so the mistakes are usually quite glaring. Not to mention that official correspondence from a company of which you are a customer will always address you with your name. Using generic phrases to address customers would make a company look unprofessional.
In some cases, malicious emails are targeted. It usually happens if cyber crooks are able to gather at least some information about their target. This is why it’s recommended to use an anti-virus program or VirusTotal to scan all unsolicited email attachments before opening them.
If you frequently pirate via torrents, you’re risking a malware infection. Because a lot of torrent sites are poorly moderated, malicious actors can easily upload their malware and disguise it as some kind of entertainment content like a movie, video game, TV series, software, etc. If users aren’t too familiar with what malware in torrents looks like, they may end up initiating it. Not only is pirating via torrents essentially stealing content, but it’s also dangerous for the computer and the files on it.
Qmak ransomware removal
When it comes to ransomware, it’s not a good idea to try to get rid of it manually. Thus, we strongly recommend using anti-virus software to delete Qmak ransomware from your computer. If you try to do it manually and not remove it fully, and you access your backup, your backed-up files would become encrypted. Only connect to your backup when the ransomware has been fully removed. For those without a backup, the only option is to back up the encrypted files and wait for a free decryptor to become available.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.