What is CoronaVi2022 ransomware
What is CoronaVi2022
CoronaVi2022 is a new ransomware infection that encrypts files. The ransomware is referred to as CoronaVi2022 because of the email address cyber crooks give for users to contact them. Cyber crooks have been actively using the coronavirus name for their malware and spam campaigns so ransomware named CoronaVi2022 is not surprising. What’s interesting about this infection is that it doesn’t come alone. While the CoronaVi2022 encrypts files, a Kpot data-stealing trojan is stealing sensitive information in the background. The infection is also distributed in an unusual way, via a fake system optimization tool. More traditional ways may also be used to spread the infection. We will explain CoronaVi2022 distribution in the following section of the report.
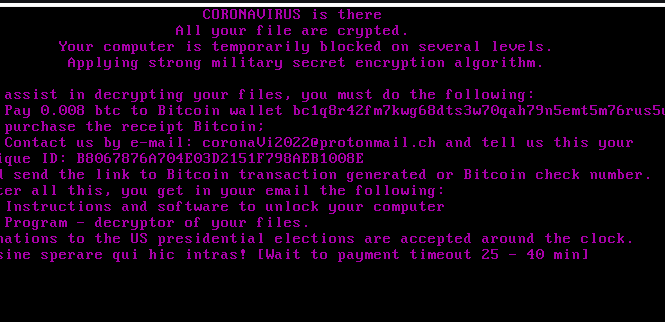
The ransomware does encrypt files but it demands only a small sum in exchange for file decryption, which is rather strange. The requested sum is around $50 while other ransomware usually ask for hundreds of dollars minimum. Nevertheless, paying the ransom is not a good idea and we cannot recommend it. Instead, recovering files via backup after CoronaVi2022 removal is the ideal option.
How is CoronaVi2022 distributed?
The CoronaVi2022 is using an unusual distribution method. It is disguised as the system optimizer WiseCleaner. WiseCleaner is a legitimate program that many people use to clean up their computers. The distributors of this ransomware have disguised their malware as this program and have created a fake website for it. When users visit the website and download the fake WiseCleaner, they end up with the ransomware and data-stealing trojan on their computers. It is unlikely that many people will randomly stumble upon the fake website and download it, but it’s not impossible.
It’s also not impossible for the ransomware to be distributed in more traditional ways like spam emails. It’s always recommended to not randomly open unsolicited email attachments because they could be harboring all kinds of malware. Emails carrying malware usually have certain signs that give them away, such as obvious grammar and spelling mistakes in an email that’s claiming to be official correspondence, ransom senders’ email addresses, and strong pressure to open the attachment. Any suspicious email attachment should be scanned with anti-malware software or a service like VirusTotal. In general, it’s best to avoid venturing into the spam folder and opening unsolicited emails.
What does CoronaVi2022 do?
The ransomware begins the encryption process immediately, and targets files like photos, videos, documents, etc. It’s essentially aiming to take any important file for hostage. All encrypted files will also be renamed. The name will contain the crook’s email address, the underscore symbol and then the original file name. A file named “file.jpg” will be renamed to “coronaVi2022@protonmail.ch_file.jpg”. A CoronaVirus.txt ransom note will automatically open, the computer will then reboot and the ransom note will be displayed across the screen. The note will change in around 45 minutes but the contents will remain more or less the same. Another 15 minutes after that, the computer will reboot and load Windows and display a text ransom note.
The note itself is rather unusual. First of all, it only asks for 0.008 Bitcoin ($45 at the time of writing), which is a very small sum compared to what other ransomware ask. The note also mentions the US presidential elections and says that donations are accepted around the clock. The small ransom sum and the election mention gives the impression that getting victims to pay the ransom is not the main intention. Instead, spreading a data stealing trojan may be the primary goal.
The CoronaVi2022 ransomware is not the only malware that enters the computer. Along with it comes the Kpot data-stealing trojan. While users deal with the ransomware, the trojan may be stealing personal and sensitive information in the background.
It goes without saying that paying the ransom is not an option. Not only is file decryption not guaranteed, you’d also lose your money. While the sum is not a big one, many people paying it would mean a profit for cyber crooks behind this malware. The only sure way to recover files would be to use backup. If you have backed up files prior to infection, once you remove CoronaVi2022 from your computer you can recover files.
Develop a habit of backing up files regularly in order to avoid losing files in case of a repeat infection or computer malfunction.
CoronaVi2022 removal
The majority of credible anti-malware programs will detect the infection. They should be able to delete CoronaVi2022 from your computer without much issue. However, getting rid of the infection does not mean files will return to normal. They will remain encrypted until they are decrypted with a CoronaVi2022 decryptor.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
