What is Koti Ransomware
Koti Ransomware will encrypt your files
Koti Ransomware is file-encrypting malware from the Djvu ransomware family. It’s a dangerous piece of malware because it will essentially lock your files and demand that you pay a ransom to get them back. It demands $980, which is the same amount all other versions of Djvu ransomware demand. All encrypted files will have the .koti extension added to them, hence why this ransomware is named Koti. The ransomware also drops a ransom note, which will explain how you need to pay to receive the decryptor.
Paying the ransom is not a good idea, it never is when it comes to ransomware. You have no reason to trust cyber crooks to keep their work and send you a decryptor once you pay. There have been many cases in the past where users paid but were not sent anything, and there are no guarantees that this will not happen to you as well.
The gang operating this ransomware have released more than two hundred Djvu variants making it one of the most notorious ransomware families currently active. Fortunately for some users, the malware being so widespread means that researchers may develop a free decrypter much faster than they usually would. Decryptors for a lot of Djvu ransomware versions are already available. However, whenever a new version comes out, it cannot be decrypted with the old decryptor.
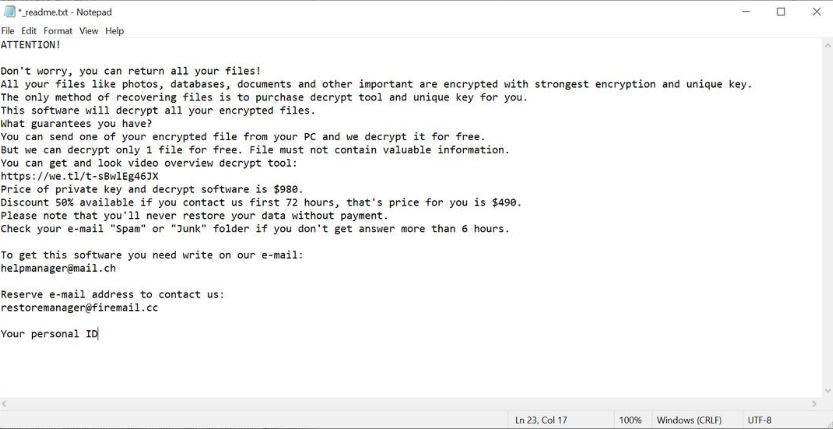
_readme.txt:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-sBwlEg46JX
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@firemail.ccYour personal ID
If you have backup and files were backed up prior to infection, you can recover files from there. However, you first need to delete Koti Ransomware and make sure no traces of it are left behind. Only when you computer is clean will it be safe to access your backup.
How does ransomware spread?
Malware infections like ransomware usually spread via spam email attachments. Infected files are attached to spam emails, and if users download and open the file, the ransomware can launch. In many cases, the emails are fairly obvious. They are sent from random email addresses, contain loads of grammar and spelling mistakes, and pressure you to open the attachment. The senders of such emails also often claim to be from legitimate companies, some government agency, etc. By using known company names, malware distributors try to make users lower their guard so they’d open the attached file without question.
But like we said, the emails are fairly obvious if you know what to look for. In general, you should not engage with unsolicited emails until you make sure they are safe. Do not open any attachments before you scan them with anti-virus software or VirusTotal.
Another method ransomware uses to infect computers is via vulnerabilities. Because of this, it’s important that you regularly update your system and software.
What does Koti Ransomware do?
Once it successfully infiltrates your computer, it will start encrypting files. It will also delete Shadow Volume Copies, as well as stop anti-virus from running on the computer. It mainly targets files users find most important, such as photos, documents, videos, etc. All encrypted files will have the .koti file extension, so you will know which files have been affected. A ransom note (_readme.txt) will also be dropped in folders containing encrypted files. The note is fairly generic, it explains that files have been encrypted and that you can recover them by buying their decryptor. The price is $980 but if you contact them within the first 72 hours, the price would be lowered to $490. They also offer to decrypt one file for free, provided that it does not contain valuable information. The email address given to contact them is helpmanager@mail.ch, or restoremanager@firemail.ch.
If you do not have backup of your files, paying the ransom may seem like a good idea. The decision is yours to make but we should warn you that paying will not necessarily help recover files. You are dealing with cyber crooks who do not care whether you recover files. There is nothing stopping them from simply taking your money and not sending you a decryptor.
If you’re not going to pay but have no backup of files, you should back up the encrypted ones somewhere safe and wait for malware researchers to release a free decryptor. Like we said above, a lot of Djvu versions are already decryptable.
Koti Ransomware removal
You will definitely need to use anti-malware software to remove Koti Ransomware. You will need to first boot your computer in Safe Mode to prevent the malware from blocking your anti-virus. Do not attempt to uninstall Koti Ransomware manually because you could end up causing more damage.
Once Koti Ransomware removal has finished, you can safely connect to your backup and start restoring files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
