Zeus Trojan
What is Zeus Trojan?
Zeus Trojan is a malicious trojan that can steal your personal information. The trojan has been around for years and is considered to be one the most successful malware out there. Its creators allegedly retired in 2010 but the source code was released to the public, which resulted in different variants popping up. While Zeus is not as widespread as it used to be, the threat is still there.
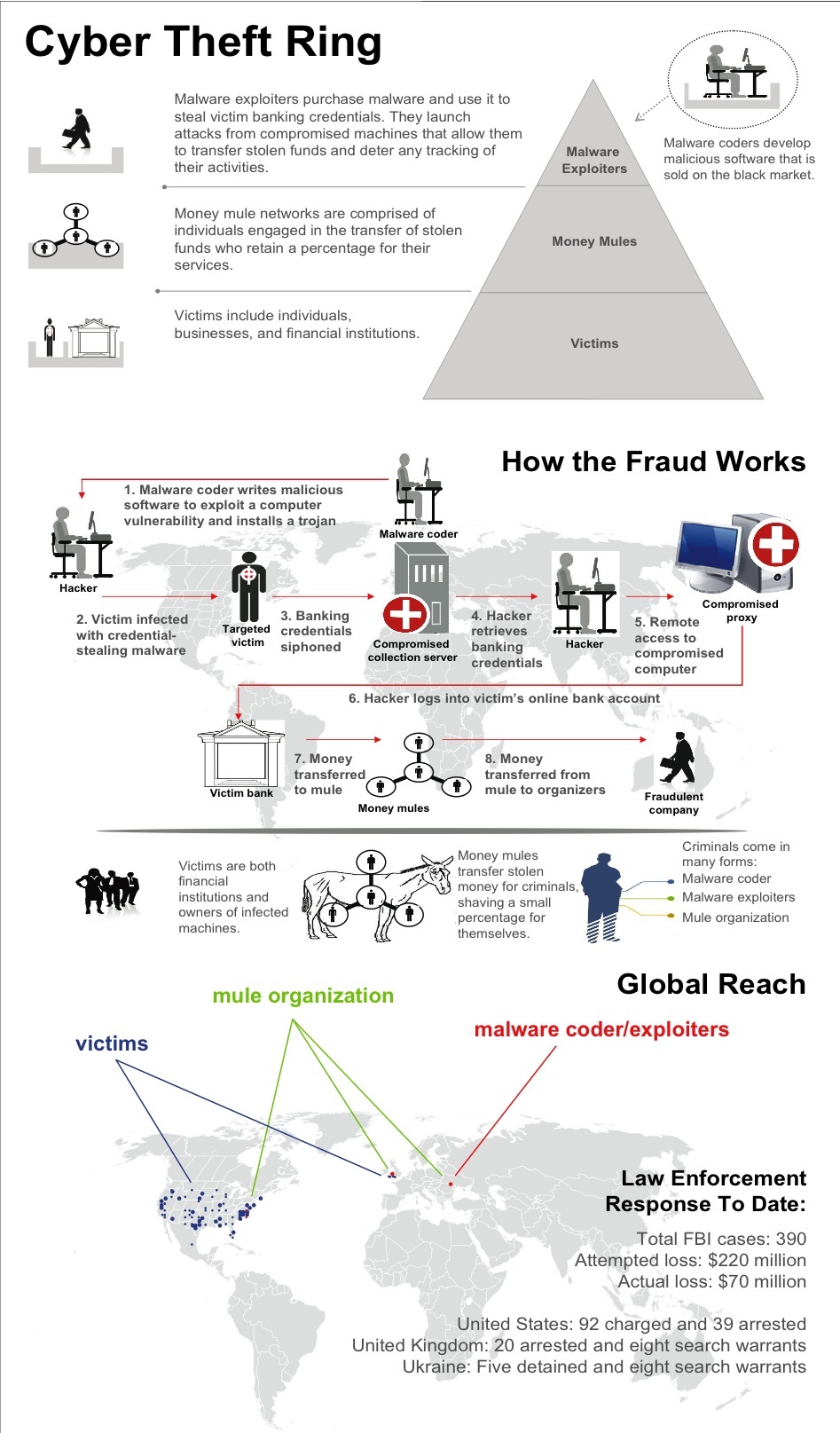
The Zeus Trojan primarily has two functions. It is commonly referred to as a banking trojan because it aims to steal banking credentials. Once it infects a device, it starts monitoring it, waiting for the user to access an online banking website. When users try to log in, their keystrokes are recorded. The second function is adding the infected device to a botnet. The network of computers that is a botnet can be used to perform large-scale attacks and collect information.
The Zeus Trojan is spread via spam messages and drive-by downloads. This is how most serious malware is spread. We will explain how you can avoid such malware in more detail but the gist of it is if you avoid opening spam emails and their attached files, as well as have anti-malware software installed, you can avoid malware.
It’s not very likely that you will notice the trojans presence on your device without anti-malware software. So if you are researching Zeus trojan, it’s likely that your anti-malware has detected it. Do not hesitate to delete Zeus Trojan as soon as possible because it poses serious threat to your computer.
How does the trojan enter your computer?
Like most serious malware infections, Zeus Trojan enters computers via spam emails and drive-by downloads. Spam emails in particular are responsible for spreading thousands of different malware. In order to convince users to open the attached file or press on the provided link, the spam email usually claims there’s an important document that needs to be opened. Since money is what catches users’ attention the most, that is the topic used in most spam emails. When users press on the link or open the attached file, the Zeus trojan is permitted to enter the computer.
Spam emails are generally pretty obvious, unless they target someone specifically and have access to certain information. But in most cases, you can spot it from a mile away. They are usually riddled with mistakes, strongly encourage you to open the attachment or press the link, the sender’s email address is usually random, and you are addressed as Customer/User/Member. It’s quite clear that you are dealing with spam when your bank supposedly emails you about a questionable transaction and refers to you as Customer instead of your name. If an email gives you any kind of red flags, do not open it straight away. You can scan attached files with anti-malware software or services like VirusTotal, which can also be used to scan a link.
Drive-by downloads is also how the Zeus trojan could get in. A drive-by download happens when you visit a corrupted website and malware downloads onto your computer. Completely legitimate websites may become corrupted so it would be nearly impossible to avoid all such websites. However, as long as you have trusted anti-malware software monitoring your computer, you should be able to avoid those malicious downloads.
What does the Zeus Trojan do?
The Zeus trojan was first detected in 2007, and over the years it had infected millions of users. In 2010, the creator allegedly retired, but once the source code became public numerous Zeus variations started popping up. Despite being created more than 10 years ago, Zeus trojan still remains a serious threat.
The primary feature of this trojan is to steal banking credentials. It has monitoring and keylogging features, which allow it to activate when you visit banking websites. The login credentials you type in are logged, which later allows Zeus operators to access your online banking account. It’s not just banking websites, it could get your social media and email credentials as well. If your mobile device is infected, the malware may also try to bypass two-factor authentication.
The other feature of this trojan is adding infected devices to a botnet. If you are not familiar with it, a botnet is a network of infected computers controlled by a command and control server. Information from infected devices could be stolen, and they could be used to perform large-scale attacks.
Tech-supports scams use Zeus malware to scare users
We should also mention that because of how notorious the Zeus trojan is, tech-support scams often mention it to scare users. A tech-support scam may appear on your screen out of the blue and claim that your device is infected with Zeus. The fake alert would claim that your information is being stolen and your files deleted, and the only way to stop it would be to call the provided number. A fake technician would convince you to give him/her remote access to your device so that your device could be cleaned. The scammer would pretend to fix the non-existent issue and then demand you pay a couple of hundred dollars for the service. Since the Zeus trojan is not on your computer, there is no need to pay anything, or call anyone for that matter.
In the future, when you get a pop-up in your browser that claims your computer is infected with something and that you need to dial the provided number, ignore the pop-up. Microsoft, Apple or any other legitimate company will not block your computer, warn you about malware via your browser, or ask you to call their tech-support in such a way. They usually do not even make unsolicited contact with their users.
Zeus Trojan removal
In order to remove Zeus Trojan fully, you will need to use anti-malware software. We do not recommend trying to manually uninstall Zeus Trojan because you could end up missing something or doing further damage to your computer. Instead, use anti-malware software. The program will do everything for you, and fully get rid of the trojan.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
