Remove Yqjs ransomware
Yqjs ransomware is malware that encrypts files. It’s part of the notorious Djvu/STOP ransomware family operated by a cybercrime gang that releases new ransomware on a regular basis. These malware infections essentially take personal files hostage in order to extort money from victims. If you find that your files have been encrypted and now have .yqjs added to them, you will be unable to open them. You will first need to run the files through a decryptor. However, the only people who have it are the cybercrooks operating this ransomware. And they will only give it to you if you pay the ransom.
If this isn’t your first time dealing with ransomware from the Djvu/STOP ransomware family, you may have noticed that Yqjs ransomware is practically identical to Mljx, Hgsh, Yqal, Wnlu, and many other versions. The versions can be differentiated by the extensions they add to encrypted files. This one adds .yqjs. For example, an encrypted image.jpg would look like this: image.jpg.yqjs. None of the files with this extension will be openable. The ransomware will target all of your personal files, including photos, images, videos, documents, etc.
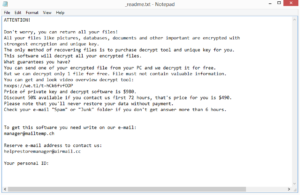
The ransomware will start file encryption immediately after it’s initiated. To distract victims, it even shows a fake Windows update window. Once it’s done, Yqjs ransomware will drop a _readme.txt ransom note in folders that contain encrypted files. The note is identical to the ones dropped by other ransomware versions from this family. It explains that files have been encrypted and how to decrypt them. Unfortunately, the latter involves paying money to cybercriminals. The price for the Yqjs ransomware decryptor is $980, though the operators offer a 50% discount to those who make contact within the first 72 hours. Whether that is true or not, paying the ransom is still risky. There are no guarantees that you will get the decryptor considering that you are dealing with cybercriminals. They may just take your money and not send the decryptor in return. It has happened in the past. While whether to pay or not is your decision, you need to be aware of the risks.
Unless you have copies of your files in a backup, it’s currently not possible to recover encrypted files. However, all hope is not lost because a free decryptor could be released in the future. There currently is a free Djvu/STOP decryptor by Emsisoft but it will not work on ransomware versions that use online keys to encrypt files. That includes Yqjs ransomware. Unfortunately, Yqjs and the majority of other ransomware in this family use online keys, which means that keys are unique to each user. Without those keys, developing a universal decryptor that recovers files is highly unlikely. However, it’s not impossible that a decryptor will be released sometime in the future. The ransomware operators themselves may release the keys if they ever decide to close shop. Or they may be caught by law enforcement. So we recommend backing up encrypted files and waiting for a free decryptor. NoMoreRansom is a good source to check whether a decryptor is available or not.
After you remove Yqjs ransomware from your computer, you can safely start file recovery if you have a backup. However, you need to make sure the ransomware is fully gone before connecting to backup because otherwise, all your backed-up files would become encrypted as well.
Ransomware distribution methods
Spam emails are one of the main methods used by malicious actors to spread malware. It’s a method that requires little effort and abilities. Cybercriminals purchase the email addresses of potential victims from various hacker forums and then spam those addresses with malicious emails. But for one reason or another, the emails carrying malware are usually quite noticeable. They do not target anyone specifically. Rather, a large number of users at the same time, which is why cybercrooks cannot personalize the emails. But in addition to being very generic, the emails are full of grammar and spelling mistakes, making them even more obvious. Senders often pretend to be from legitimate senders, supposedly emailing on the behalf of companies whose services users use. But when the emails are full of grammar/spelling mistakes, it’s pretty obvious that the sender is not legitimate. Furthermore, even when senders claim that users use their services, they address them using generic terms like “Customer”, “User”, “Member”, etc. When you receive an email from a company whose services you do use, you will always be addressed by your name because generic greetings look unprofessional.
To avoid opening anything malicious, we highly recommend scanning all unsolicited email attachments with anti-virus software or VirusTotal. It can save you from a lot of trouble if you develop this habit in addition to backing up your files.
Malicious actors distribute their malware via torrents as well. You probably already know this but torrent sites are quite poorly managed. Malicious actors often take advantage of this and post torrents with malware in them. They’re often disguised as torrents for popular movies, TV series, video games, software, etc. It’s especially common to have malware in torrents for recently released movies. As an example, when a new Marvel movie is released, you will find many malicious torrents of it. We are sure you know this, but downloading copyrighted content for free via torrents is not only stealing, but it’s also dangerous for the computer.
Yqjs ransomware removal
You will need to use anti-virus software to remove Yqjs ransomware from your computer because it’s a very complex malware infection. Unless you know exactly what you’re doing, we do not recommend trying to delete Yqjs ransomware manually because you could end up causing further issues. Or you may not fully get rid of the ransomware, which would allow it to return later on. And if the ransomware is still present when you connect to your backup, the files in the backup would become encrypted as well, destroying your chances of recovering files. Thus, use anti-virus software to get rid of the ransomware. Once it’s fully gone, you can start recovering files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.