How to delete Rugj ransomware
Rugj ransomware is one of the most recent file-encryption malware to come from the Djvu/STOP malware family. There are many almost identical ransomware threats out there because the gang behind Djvu/STOP keeps releasing new versions essentially on a daily basis. The extension they add to encrypted files helps differentiate between them. This particular ransomware adds .rugj to files it encrypts, hence why it’s known as Rugj ransomware. Unfortunately, it’s currently not possible to decrypt files for free.
Rugj ransomware is essentially identical to .maql, .zaps, .nqsq, and .tisc. They all encrypt the same files, drop the same ransom note, etc. Even the prices for the decryptor are the same. They do, however, add different file extensions. If your files have .rugj added to them, you are dealing with the Rugj ransomware. It will encrypt all your personal files, including photos, video, images, documents, etc. As an example, an encrypted file would look like this – image.jpg.rugj. You will not be able to open any files with this extension unless you first use a specific decryption tool on them. However, the only ones with a working decryptor are the cybercrooks operating this ransomware.
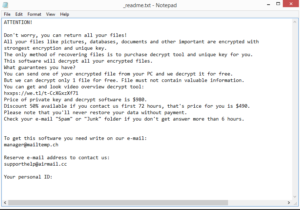
While your files are being encrypted, the ransomware will show a fake Windows update window to distract you. Once it’s done, it will drop a _readme.txt ransom note to folders that contain encrypted files. The note is pretty generic and essentially threatens victims that files are unrecoverable unless they get a decryptor. The cybercrooks operating this ransom offer the decryptor for $980, or $490 for victims who contact them within the first 72 hours. Whether you pay the ransom or not is your decision but we feel it’s necessary to explain the risks involved so you can make an informed decision. The biggest issue with paying the ransom is that it does not guarantee that you will actually be sent the decryptor. Since you are dealing with cybercriminals, there are no guarantees that they will keep their end of the deal after you make the payment. Countless users in the past have paid but received nothing in return. Another reason why it’s generally not recommended to pay the ransom is that as long as victims continue paying, cybercriminals will continue their malicious activities. If users develop the habit of backing up files on a regular basis, they would not need to pay the ransom.
If you have a backup, you can start file recovery as soon as you delete Rugj ransomware from the computer. Be careful to fully remove the ransomware with all of its components because if it’s still present when you connect to your backup, the backed-up files would become encrypted as well. This is why it’s recommended to use anti-virus programs to delete ransomware. For users who don’t have a backup, file recovery options are very limited. The only option is to wait for a free decryptor to be released. While there is a free Djvu/STOP decryptor developed by Emsisoft, it will not work on versions released after 2019 (including Rugj) because they use online keys to encrypt files. This means that the keys are unique to each victim and unless they are released, it’s not possible to develop a working decryptor. However, it’s not impossible for the keys to be released by the cybercriminals themselves when they decide to close shop. Law enforcement may also release a decryptor if they ever catch those responsible for this ransomware. So back up encrypted files and check NoMoreRansom from time to time for a decryptor.
How is ransomware distributed?
If you’re dealing with ransomware, you likely have bad browsing habits. Harmless actions like opening unsolicited email attachments or pirating via torrents could lead to serious malware infections. If you familiarize yourself with how ransomware spreads and develop better browsing habits, you should be able to avoid malware in the future.
Malicious email attachments, or malspam, are one of the most common ways users encounter ransomware. Cybercriminals buy thousands of email addresses from hacker forums and then use them for their spam campaigns. The spam emails have file attachments that would initiate an infection if you open them. Commonly, malicious actors pretend to be from companies whose services users supposedly use in order to force users into opening the emails. Fortunately for users, it’s quite easy to differentiate between malicious and legitimate emails. One of the most noticeable signs that an email may be malicious is grammar and spelling mistakes. Legitimate emails from a company you use will not have any grammar/spelling mistakes because it looks unprofessional. But spam emails are always written in broken English and contain mistakes. The way an email addresses you can also signal whether it’s legitimate or not. If the sender claims that you use their services, they will use your name to address you. If generic terms like “User”, “Customer”, “Member” are used, it’s likely that you’re dealing with a scam. While most malicious emails will be generic, some may be more sophisticated. Thus, it’s recommended to scan all email attachments with either anti-virus software or VirusTotal.
It’s also very easy to pick up ransomware infections via torrents. Torrent platforms are often poorly moderated, which allows cybercrooks to upload their malware in torrents disguised as movies, TV series, video games, software, etc. It’s especially common for popular content torrents to contain malware. For example, whenever a new Marvel movie comes out, it’s guaranteed that its torrents will contain malware. By downloading copyrighted content via torrents, you’re not only essentially stealing content but also endangering your computer.
Rugj ransomware removal
Ransomware is a very complex malware infection so we do not recommend you to try to remove Rugj ransomware manually. This could cause even more damage or you may not delete it fully. If you connect to your backup while the ransomware is still on the computer, files in the backup would become encrypted as well. Thus, we advise using anti-malware software to delete Rugj ransomware.
If you don’t have a backup, your only option is to back up encrypted files and wait for a free decryptor. Even if it’s not available at the moment, that may change in the future. However, you need to be very careful about the sources from where you download decryptors because there are many fake/malicious ones. NoMoreRansom is a good source for decryptors because it’s guaranteed to be safe.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.