Nqsq ransomware removal
Nqsq ransomware is the most recent file-encrypting malware to come from the Djvu/STOP ransomware family. The group operating this ransomware is responsible for releasing hundreds of file-encrypting malware infections, all of which can be identified by the extension they add to encrypted files. This ransomware adds .nqsq, hence why it’s known as Nqsq ransomware. At this moment in time, it’s not possible to recover files for free, unless you have backed up your files.
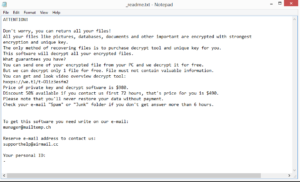
Nqsq ransomware comes from the same malware family as Tisc, Rigd, Koom, and Hoop. All versions are more or less the same, but they can be differentiated by the extensions they add to files they encrypt. In this case, it would be .nqsq. For example, image.jpg would become image.jpg.nqsq. All files with this extension will be unopenable unless they are first put through a decryptor. All personal files will be targeted by ransomware, including photos, videos, documents, images, etc. While the ransomware is encrypting files, it will show a fake Windows update window. Once files are done being encrypted, a _readme.txt ransom note will be dropped in all folders containing encrypted files. The note explains it’s only possible to decrypt files using a special decryptor that victims can buy for $980, or $490 if contact is made within the first 72 hours. Unfortunately, it is correct that files can only be decrypted using that decryptor. Nonetheless, it’s not a good idea to pay the ransom.
Whether you pay the ransom is your decision but generally, it’s not recommended to give in to the demands. Keep in mind that you are dealing with cybercriminals, and there is nothing obligating them to help you even if you pay. Many users in the past have paid but received nothing in return. The demanded ransom is quite a large amount of money so you should be aware of the risks before deciding.
If you regularly backed up your files prior to the ransomware infection, there should be no issue with file recovery. However, before you access your backup, it’s necessary to fully remove Nqsq ransomware from the computer. It’s best to use anti-virus software. Only when the ransomware is fully gone should you connect to backup and start recovering files. Otherwise, files in your backup would become encrypted as well.
If you do not have file backup, your options are, unfortunately, quite limited. The only option is to wait for a free decryptor to become available. There is a free Djvu/STOP decryptor available but it will only work to decrypt files encrypted by older versions. Older versions used offline keys to encrypt files, meaning they were the same for all victims. However, new versions, including Nqsq ransomware, use online keys, which means that they are all different. Unless the cybercriminals themselves release the keys, it’s not possible to develop a universal decryptor that would work for all victims. However, it’s not impossible that it will be released in the future, so it’s recommended to back up encrypted files and wait for a free decryptor to become available. We should also warn you that there are many fake decryptors that could lead to more malware infections. Stick to sources like NoMoreRansom to download safe decryptors.
Ransomware infection methods
When it comes to ransomware, it’s usually users who have bad browsing habits that infect their computers. Seemingly minor things like opening unsolicited email attachments, clicking on ads, downloading pirated content via torrents, etc., could lead to ransomware infection. Developing better habits can go a long way towards avoiding encrypted files.
One of the most common ways ransomware infects computers is via malicious email attachments. It’s enough to simply open the wrong attachment and the ransomware can initiate. This is why it’s very important to learn how to notice malicious emails. Fortunately, unless they target someone specific, the emails are quite generic, thus easily recognizable. It should be first mentioned that malicious emails are made to look like they are sent from legitimate companies whose services users use. For example, the sender may claim to be from a package delivery service, an online store, or a bank. But because malicious emails are full of grammar/spelling mistakes, it’s easy to notice when an email is actually legitimate. In addition to the mistakes, how an email addresses you can also give it away. Generic spam emails address users as “Users”, “Members”, “Customers”, etc. If a company whose services you use sends you an email, it would address you by name. We should also mention that just as a precaution, you should scan all unsolicited email attachments with your anti-virus software or VirusTotal before opening them. This will ensure that you will not open anything malicious.
Torrents are another common way ransomware spreads, more specifically, torrents for copyrighted content. Torrent sites are notoriously badly regulated, which allows malicious actors to easily upload malware disguised as a popular movie, TV show, video game, software, etc. Malicious actors take full advantage of this. It’s especially common to find malware in torrents for something that’s particularly popular at the time. For example, when a Marvel movie comes out, torrents for that movie will mostly be malware. Pirating is not only stealing content but also dangerous for the computer.
Lastly, you should be very careful about what ads you click on and interact with. In particular, when you visit high-risk websites, you need to be very careful when interacting with any ads because they will likely be dangerous. You should also install an adblocker program to block intrusive ads and pop-ups.
Nqsq ransomware removal
Because ransomware is a very complex malware infection, it’s not recommended to try and remove Nqsq ransomware manually. Incorrectly removing it could cause even more damage or allow it to recover later on. If the ransomware recovers or is not fully removed when you connect to your backup, those files would become encrypted as well. It’s much easier and safer to use anti-virus software to delete Nqsq ransomware from the computer. Once the ransomware is gone, you can access your backup and start recovering files.
Users who have not backed up their files do not have many options when it comes to recovering files. The only way victims would be able to recover files is if a free decryptor gets released. While it’s not currently available, malware researchers may be able to develop a universal decryptor. So we recommend backing up those encrypted files and waiting for a free decryptor to become available.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.