Lqqw ransomware removal
Lqqw ransomware is a harmful piece of malware that encrypts files. It comes from the Djvu/STOP ransomware family, and there are already hundreds of versions of essentially the same ransomware. The versions are released on a regular basis, with Lqqw ransomware being the most recent one. It can be recognized by the .lqqw extension added to encrypted files. At this current moment, is not possible to decrypt files that have been encrypted by Lqqw ransomware for free.
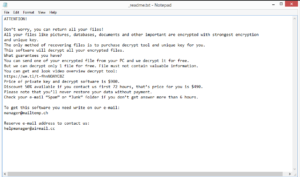
Ransomware like Hoop, Muuq, Aeur, and Orkf all belong to the same Djvu/STOP ransomware family. For the most part, they’re identical but can be differentiated by the extensions they add to encrypted files. The name of the ransomware is the extensions it adds. So Lqqw ransomware adds .lqqw. The ransomware targets personal files, including photos, images, videos, and documents. An encrypted image.jpg file would become image.jpg.lqqw. Files with that extension will not be openable unless they are first run through a specific decryptor. However, that decryption tool is, at the moment, only obtainable by buying it from the malicious actors operating this ransomware. The process of buying it is explained in the _readme.txt ransom note that gets dropped in all folders containing encrypted files. The note explains that the decryptor can be purchased for $980 or with a 50% discount if contact is made within the first 72 hours. manager@mailtemp.ch and helpmanager@airmail.cc are given as the contact addresses.
However, as always, paying the ransom is not recommended. While the decision is yours to make, you need to be aware of the risk involved in paying the ransom. First of all, there are no guarantees that you will actually get the decryptor. Unfortunately, it’s not uncommon for ransomware operators to take the money and not send the decryptor. After all, there’s nothing really stopping them from doing so. Second, if you pay once, cybercriminals may target you again because they think you will pay one more time. And it should be mentioned that the reason ransomware continues to thrive is because victims pay the ransomware.
The best remedy to a ransomware infection is a backup of all important files. If you have a backup, you can start recovering files as soon as you remove Lqqw ransomware from your computer. However, make sure to use anti-virus virus software to remove Lqqw ransomware because if it’s not removed fully and you access your backup, backed-up files would become encrypted as well.
For those without backup, waiting for a free decryption tool may be the only option. Software company Emsisoft has developed a free Djvu/STOP decryptor but it only works for a very limited amount of Djvu versions. And unless it used offline keys that are already known to Emisoft to encrypt your files, it will not work on Lqqw ransomware. It’s not impossible that a working decryptor will be released sometime in the future, so we recommend backing up encrypted files while you wait. You can check NoMoreRansom from time to time for the decryptor.
Ransomware distribution methods
Good browsing habits significantly decrease the chances of encountering various malware, including ransomware. Such infections are often spread via malicious email attachments, torrents, malicious ads/updates/downloads, rootkits, etc. It’s a good idea to become familiar with the distribution methods and develop better browsing habits if you want to avoid malware in the future.
Torrents are notorious for being malware-ridden, mainly because torrent sites are very badly moderated. Malicious actors can easily upload all kinds of malicious content and disguise it as a torrent for a popular movie, TV show, video game, etc. It’s especially common to find malware in torrents for content that is popular. For example, Marvel movie torrents often have malware in them, both before and after said movies are released in theaters. Pirating copyrighted content is not recommended not only because it’s essentially stealing content but also because it’s dangerous for the computer.
Malicious email attachments are also a very common way ransomware is spread. The malicious spam campaigns carrying malware are usually sent to users whose email addresses have been leaked by some kind of service or breached. Cyber crooks buy these email addresses in large quantities and then use them for their spam campaigns. Emails carrying malware are often low-effort and fairly obvious, which benefits users as they have an easier time avoiding infections. When an unsolicited email with an attachment lands in your inbox, carefully inspect the contents before opening the attachment. The senders often claim to be contacting users on behalf of some service they supposedly use and pressure them into opening the attachments by declaring them important documents that need to be reviewed as soon as possible. However, such emails are often riddled with grammar and spelling mistakes, which is one of the most obvious signs of a malicious email. Another thing to take note of is how the email addresses you. If the sender claims to be from a company whose services you use but uses User, Member, Customer, etc., to address you, it’s likely spam. Finally, we highly recommend that you scan all unsolicited email attachments with anti-virus software or VirusTotal before opening them.
Lqqw ransomware removal
We advise against attempting to manually remove Lqqw ransomware because that could cause additional damage. Furthermore, you might not fully delete Lqqw ransomware, which would later allow the malware to recover. The safest option is to use anti-virus software. Once the ransomware has been fully removed, you can access your backup and start recovering files.
If you don’t have a backup, your only option is to wait for a free decryptor to be released. It’s not currently available because it’s necessary to have the encryption keys to develop one but it’s not impossible that the keys will eventually be released by the cybercriminals themselves when they stop their malicious activities or by law enforcement agencies if they ever catch those responsible.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.