How to remove Qlkm ransomware
Qlkm ransomware is one of the Djvu/STOP ransomware versions. It’s one of the more recent ransomware to come from this ransomware family. It can be identified by the .qlkm file extension added to encrypted files. You will not be able to open encrypted files until you use a decryptor on them.
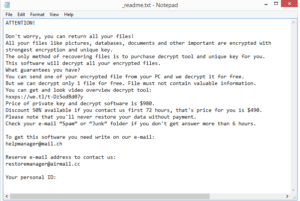 The ransom note dropped by Qlkm ransomware
The ransom note dropped by Qlkm ransomware
Djvu/STOP ransomware family is rather notorious for having released hundreds of ransomware in the last couple of years. Qlkm ransomware is one of the more recent one. Other ransomware in this family includes Pola, Wbxd, and Coos. This ones adds .qlkm to encrypted files, which is why it’s known as Qlkm ransomware. Once files are encrypted, you will not be able to open them unless you first run them through a decryptor. However, the issue with that is that the only people who have the decryptor are the cyber criminals operating this ransomware. And they will not be generous enough to just give it to you. As explained in the _readme.txt ransom note it drops, you would need to pay $980 (or $490 if contact is made within the first 72 hours) to get the decryptor.
For users who do not have backup for files, paying may seem like a good option. However, in reality, not all users who pay get the decryptor. Users should keep in mind that they are dealing with cyber criminals who are unlikely to feel obligated to help, even if a payment is made. Unfortunately, many users in the past have not received a decryptor, despite paying. So while whether you pay or not is your decision, you should be aware of the risks involved, including that you could end up losing your money.
If you do have backup, you can access it to start file recovery as soon as you remove Qlkm ransomware from your computer. To do which you would need to use anti-virus software. If the ransomware is still present when you access backup, you could end up with encrypted backed up files.
If you don’t have backup, we suggest backing up your encrypted files and waiting for a free decryptor to become available. There is a free decryptor available for old Djvu/STOP ransomware versions, but it does not work for ransomware that uses online keys to encrypt files. And that unfortunately includes Qlkm ransomware, and all other versions that were released after August 2019. You can find more information about it here. One that works for Qlkm may be released by malware researchers in the future, if law enforcement release the keys or if the cyber crooks behind this ransomware do it themselves.
How does ransomware infect a computer?
If you’re not sure how the ransomware got into your computer, it may have been triggered by you opening a malicious email attachment, downloading pirated content via torrents, clicking on a malicious ad, etc. Usually infection happens because of bad browsing habits.
Malspam email is one of the most common ways ransomware can enter a computer. All you need to do to get infected is open the malicious attachment and enable macros when prompted. Fortunately for users, malspam is usually quite obvious. Malicious emails usually try to imitate official emails, though they usually do a poor job at that. The most obvious sign of a malicious email is a random sender’s email address, especially when the sender claims to be emailing because of some kind of official business. Another sign is an abundance of grammar and spelling mistakes. It’s also pretty common for them to pressure users into opening the file attachments by claiming it’s some kind of important document that needs to be reviewed. To protect yourself from malware, always scan unsolicited email attachments with anti-virus software or VirusTotal before opening them.
It’s also very common to encounter malware in torrents. Pirating is considered to be quite dangerous, considering how badly regulated torrent sites are. Malicious actors can easily upload malware disguised as some popular movie, TV show, game, or software. It’s especially common for torrents for popular content to contain malware. For example, when Game of Thrones was airing, episode torrents often had malware in them. We strongly suggest you refrain from pirating via torrents, not only because it’s dangerous but also because it’s essentially stealing content.
Lastly, we should mention that it’s important you install updates as they come out. Updates patch known vulnerabilities which could be used by malware to get in. It’s very much recommended to enable automatic updates.
How dangerous is Qlkm ransomware?
The first sign of a Qlkm ransomware infecting your computer is a fake Windows Update window. The window is shown to distract you from the fact that your files are being encrypted. By the time you notice, all your personal files (documents, photos, videos, etc.) will be encrypted. You can tell which ones by the .qlkm extension added. As an example, text.txt would become text.txt.qlkm. As you’ve likely already noticed, you are not able to open encrypted files. The only way to recover them is to use a decryptor.
Once ransomware is done with file encryption, it will drop _readme.txt ransom notes in all folders containing encrypted files. The note explains that files can be recovered if a ransom is paid. Two contact addresses are given, helpmanager@mail.ch and restoremanager@airmail.cc. Both the note and the contact email addresses are basically identical to the ones provided by the other Djvu ransomware versions. The note says that to get the private key to recover files, paying a $980 ransom is necessary. Supposedly, if you make contact within the first 72 hours, the price would be lowered to $490. The cyber crooks also offer to decrypt one file for free, as proof that they actually have the decryptor. However, just because they can help you, does not mean they will. As we said above, countless users have paid but not received anything.
At this moment in time, recovering files for free without backup is not possible. That may change in the future, which is why you should back up encrypted files.
How to delete Qlkm ransomware
We don’t recommend you try manual Qlkm ransomware removal because it’s a complicated infections that should be dealt with anti-virus software. Once you remove Qlkm ransomware, you can access your backup safely. Unfortunately, removing the ransomware does not decrypt files.
Site Disclaimer
WiperSoft.com is not sponsored, affiliated, linked to or owned by malware developers or distributors that are referred to in this article. The article does NOT endorse or promote malicious programs. The intention behind it is to present useful information that will help users to detect and eliminate malware from their computer by using WiperSoft and/or the manual removal guide.
The article should only be used for educational purposes. If you follow the instructions provided in the article, you agree to be bound by this disclaimer. We do not guarantee that the article will aid you in completely removing the malware from your PC. Malicious programs are constantly developing, which is why it is not always easy or possible to clean the computer by using only the manual removal guide.
